Heartbleed and Rethinking Session Management with Multi-Factor Authorization
May 05, 2014 •
The critical vulnerability in OpenSSL dubbed Heartbleed has gotten a lot of much needed attention to the security industry.
Note: All LoginTC systems were patched within hours of the news becoming public alongside communication campaigns with upgrade paths provided to all our administrators.
Online services incur long-running user sessions
Users are spending more time online signed into services, accessing personal information, managing finances, accessing corporate assets and working remotely. Each time a user signs into a service they become susceptible to session take over attacks. Using multi-factor authentication to sign in is the minimum to establish the session, what about securing it once established?
Securing the communication link between user and the service with SSL is a good idea, but doesn’t go far enough. Session take over attacks are indiscriminate to how the session was established. Security researchers at Mandiant, uncovered VPN sessions originally protected with multi-factor authentication being taken over via Heartbleed exploit. That means, even if multi-factor authentication was used to sign in, users are still exposed as are the services and corporate assets they are connecting to. The longer a user session runs, the more susceptible to attack it becomes.
Do better by taking a page from Privileged Identity Management (PIM)
In a nutshell Privileged Identity Management focuses on managing, controlling and monitoring all powerful accounts within an enterprise. Provisioning, access control, authentication, authorization, auditing all that good stuff. It is a piece of identity management which is getting a lot of attention and will get a lot more as most enterprises don’t do privileged identity management right. Security firm Beyond Trust surveyed 265 IT decision makers and found 65% of organizations have controls in place to monitor privilege access, BUT 54% of those respondents stated that they could circumvent those controls! Check out the full findings of their Privilege Gone Wild survey.
Authorization for short-term access
A key component of PIM is authorization for short-term access. Where authentication establishes who you are, authorization establishes what you are allowed to do.
- Want to sign into a service or server machine? Okay please authenticate.
- Want to transfer funds or get server root privileges? Okay please authorize.
Examples
| Unix Stack | |
| Authentication | Authorization |
|---|---|
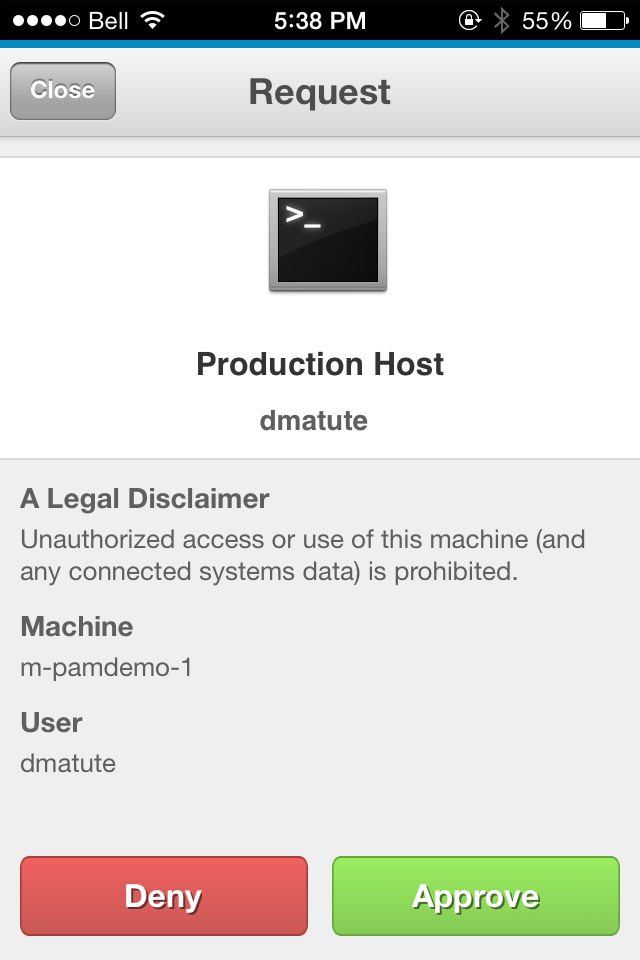 SSH as admin user into production host SSH as admin user into production host |
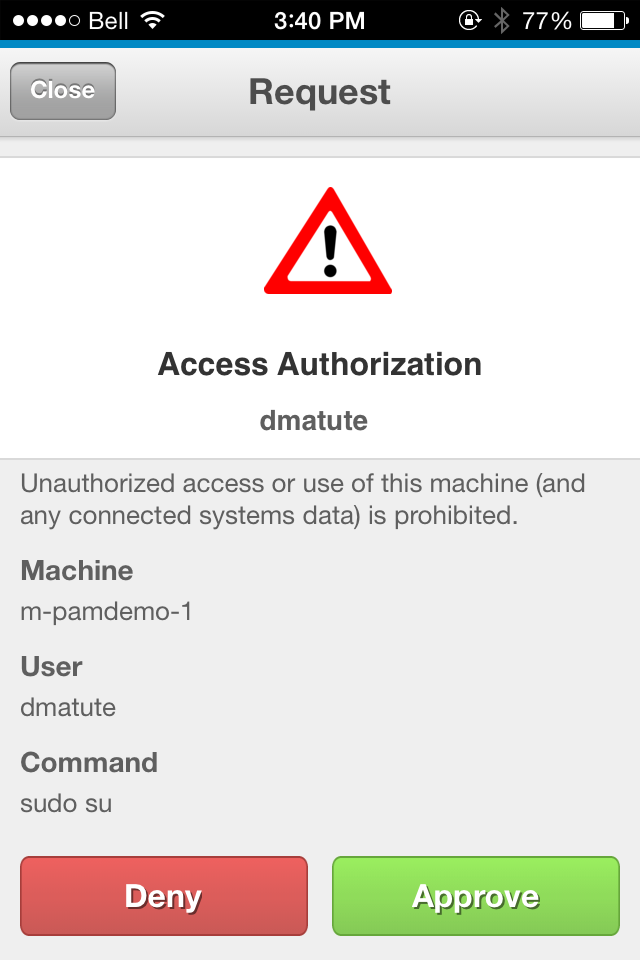 Becoming root user with Becoming root user with sudo su on production host |
| Banking | |
| Authentication | Authorization |
|---|---|
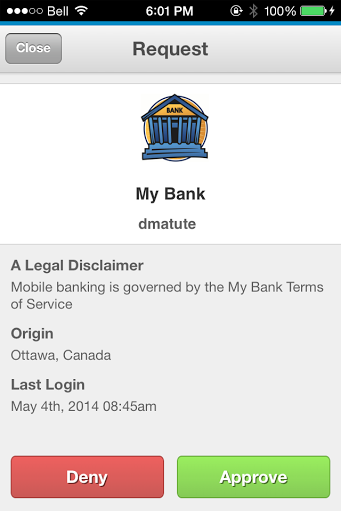 Signing into online banking account Signing into online banking account |
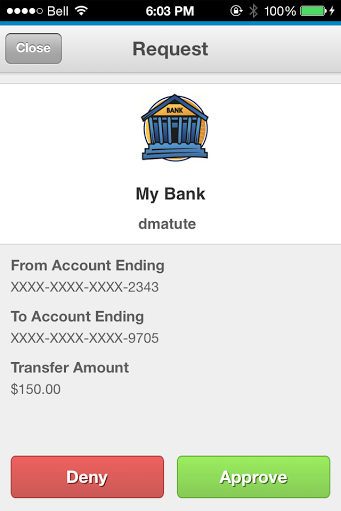 Transferring funds between accounts online Transferring funds between accounts online |
| Government Pension | |
| Authentication | Authorization |
|---|---|
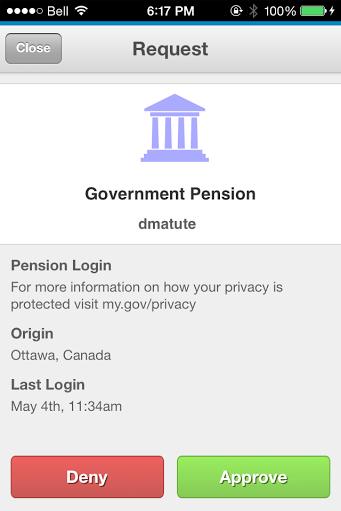 Signing into online pension service Signing into online pension service |
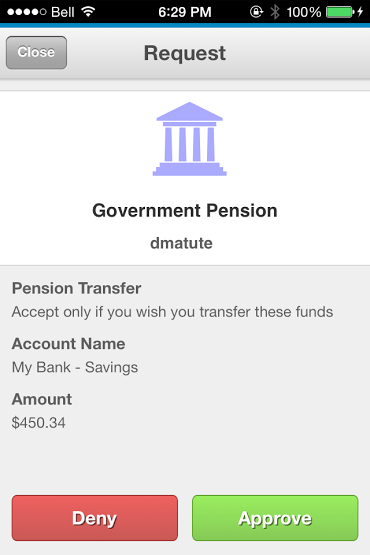 Transferring funds between pension and personal banking account Transferring funds between pension and personal banking account |
Make critical actions atomic
Critical actions should be atomic and require short-term access with an out-of-band multi-factor authorization request. Atomic means the smallest possible attack footprint. Out-of-band makes it independent of how the session was established or maintained. Multi-factor makes it more secure. All wins.
For this to work the out-of-band authorization process must be secure, easy for administrators to manage and easy for end-users to use.
LoginTC provides highly customizable authorization functionality out of the box. Combine custom domain attributes with our REST API and / or a multitude of LoginTC connectors.
Contact us at sales@cyphercor.com for more info or better yet sign up and try it out!