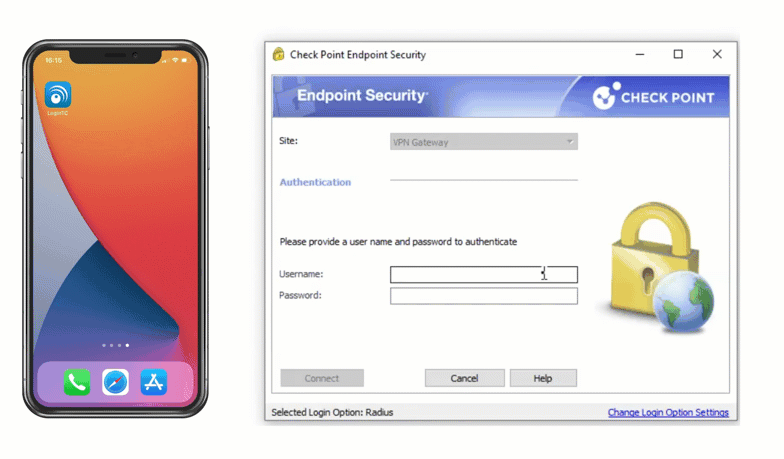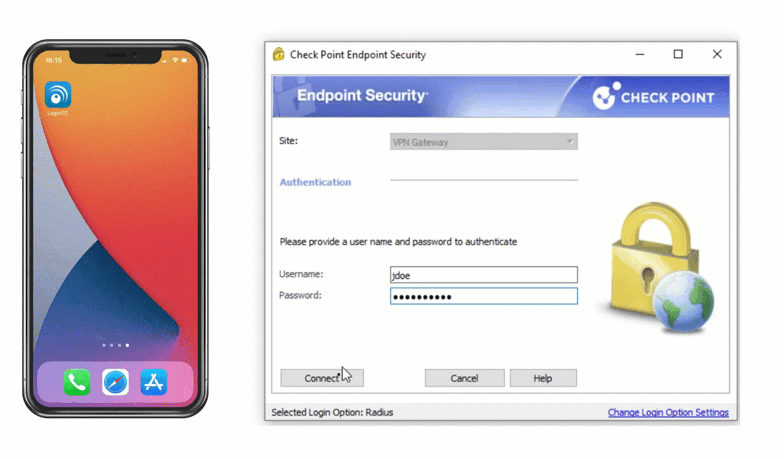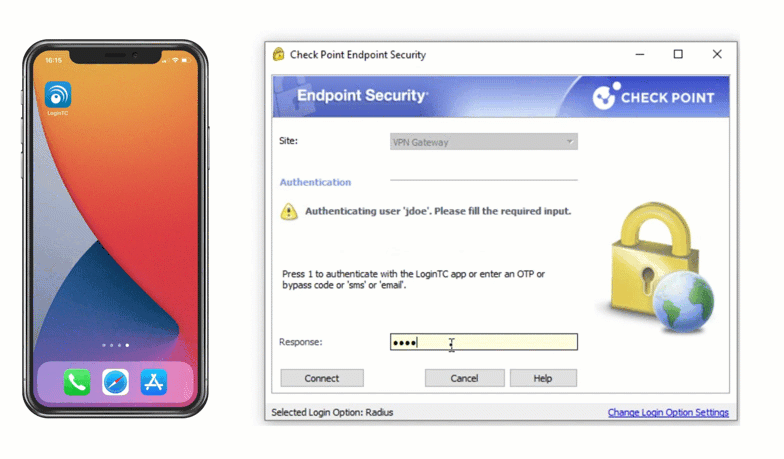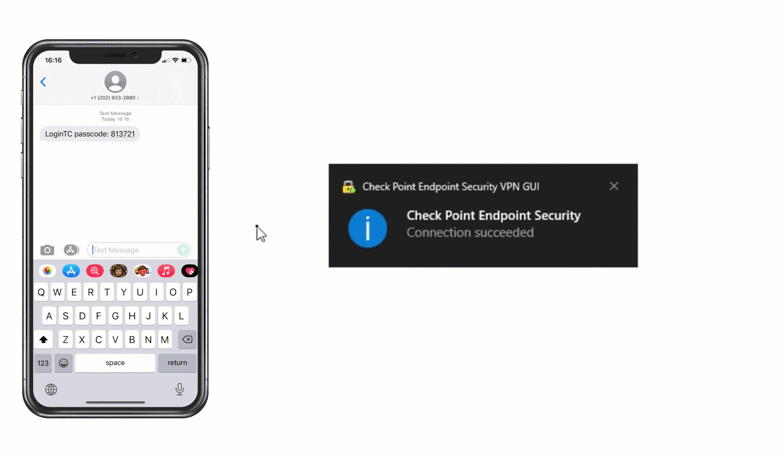
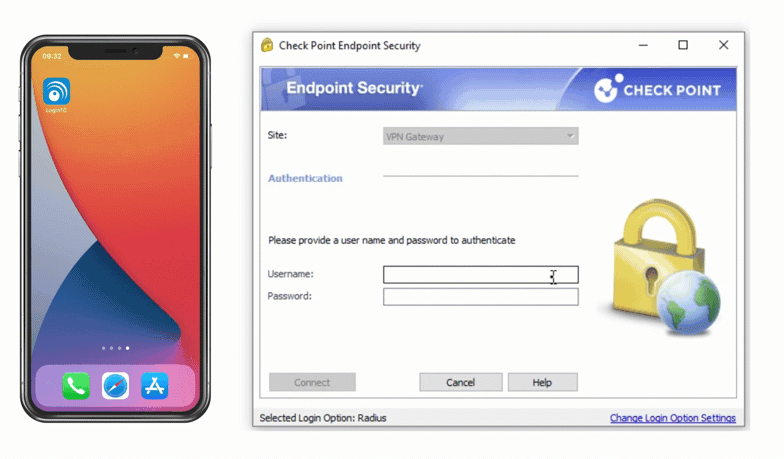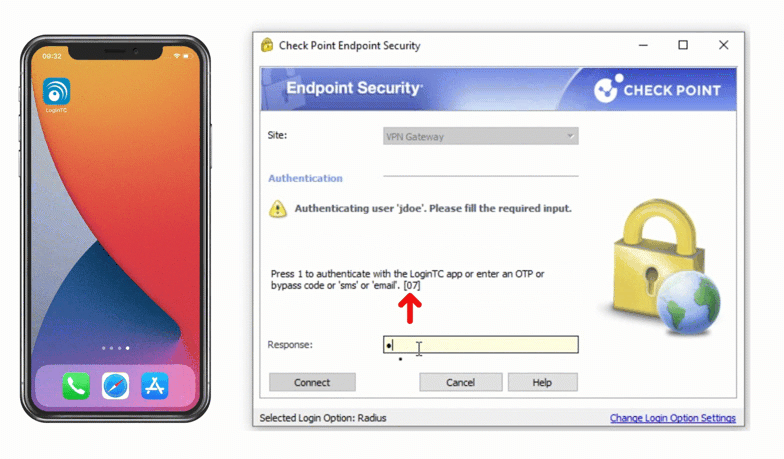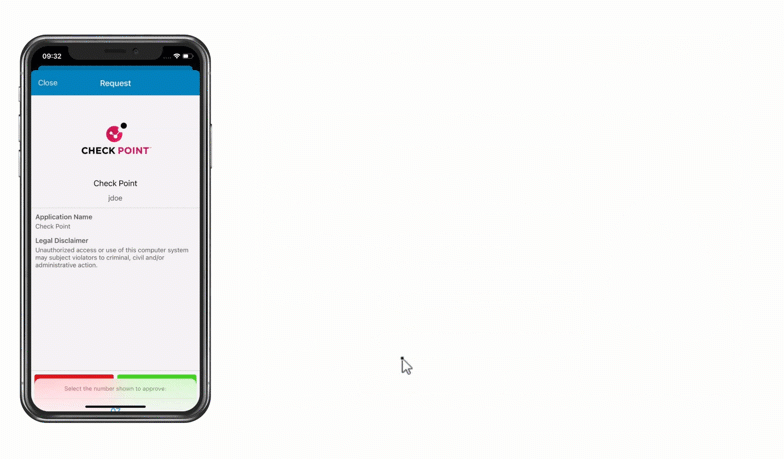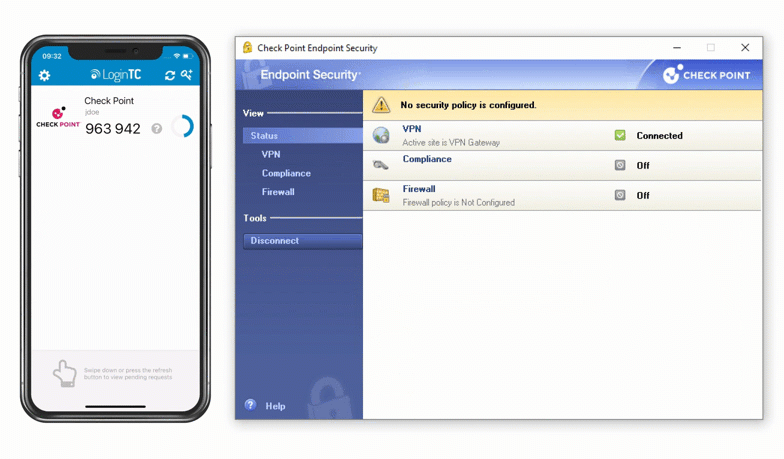
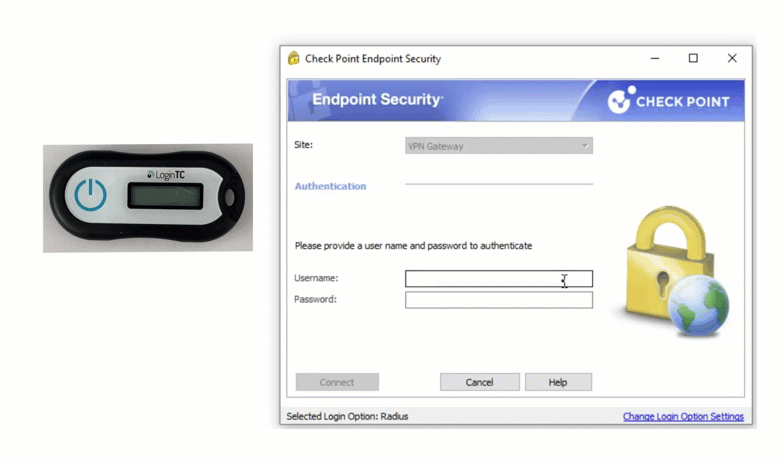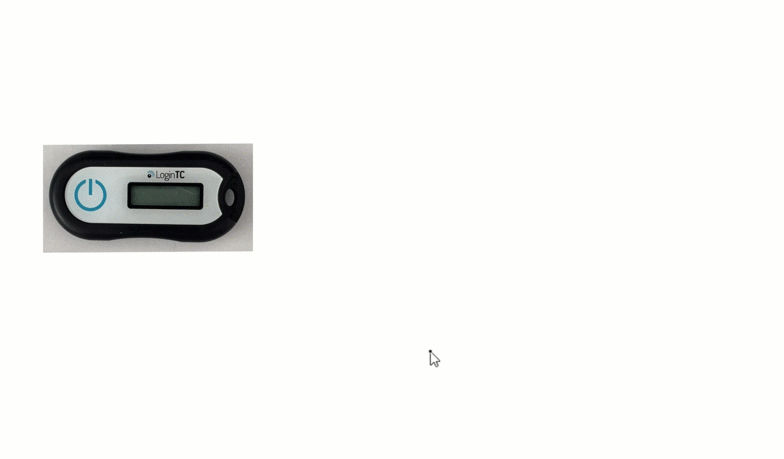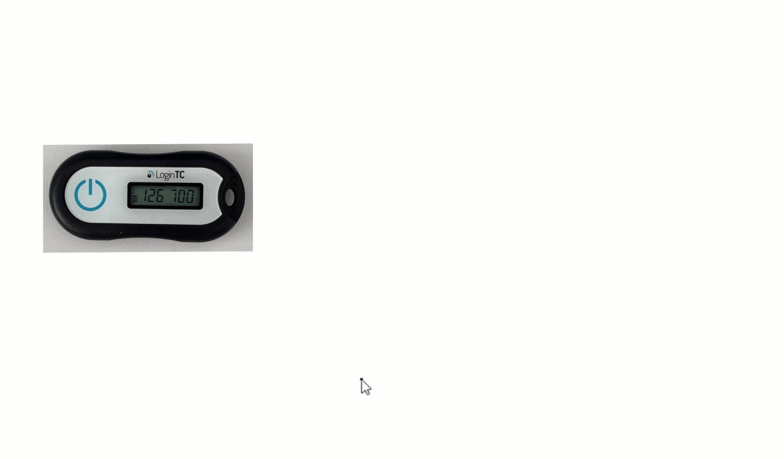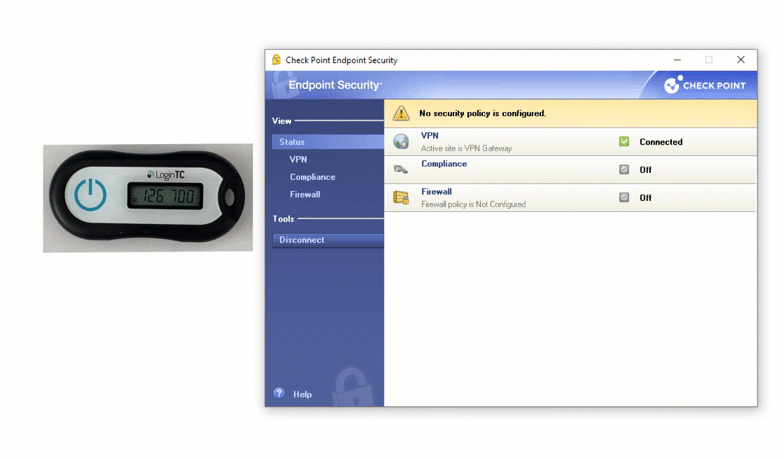
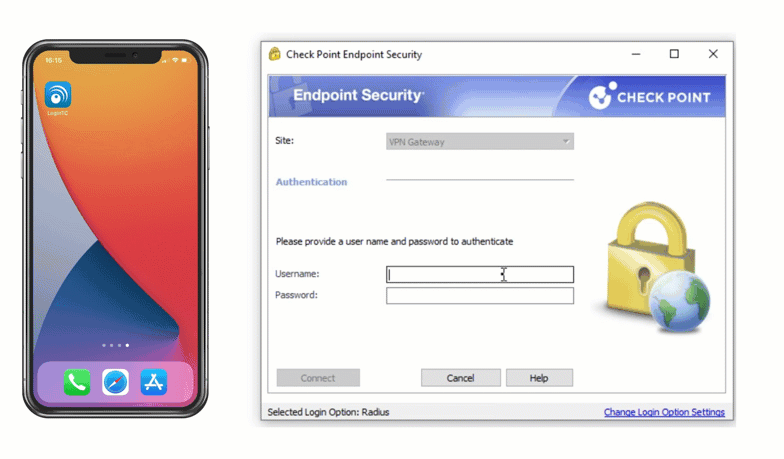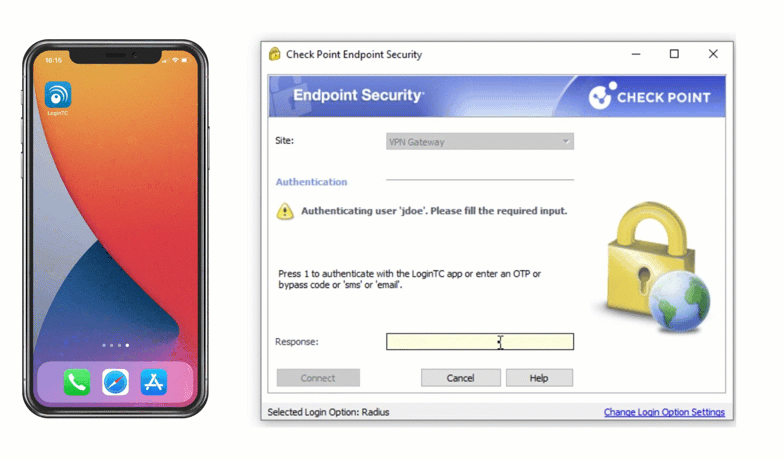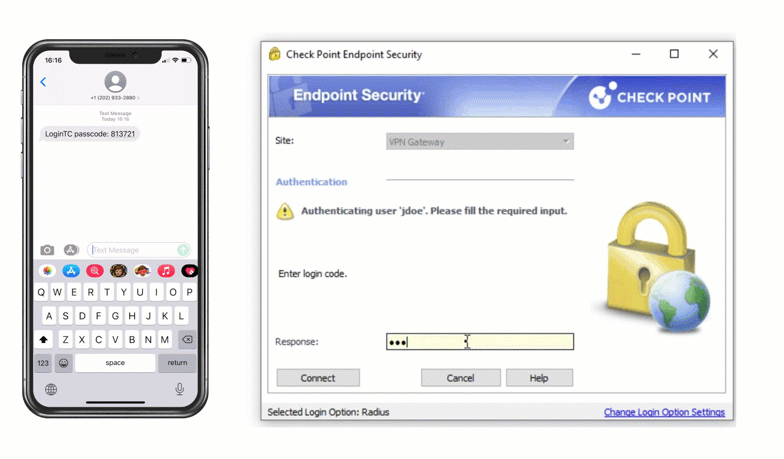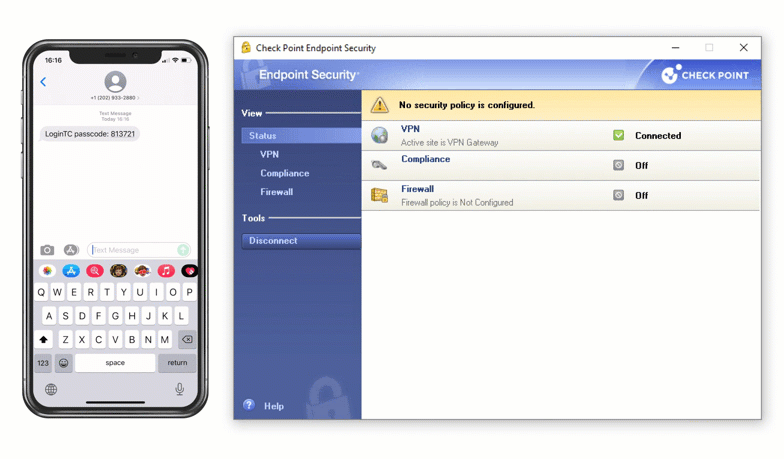
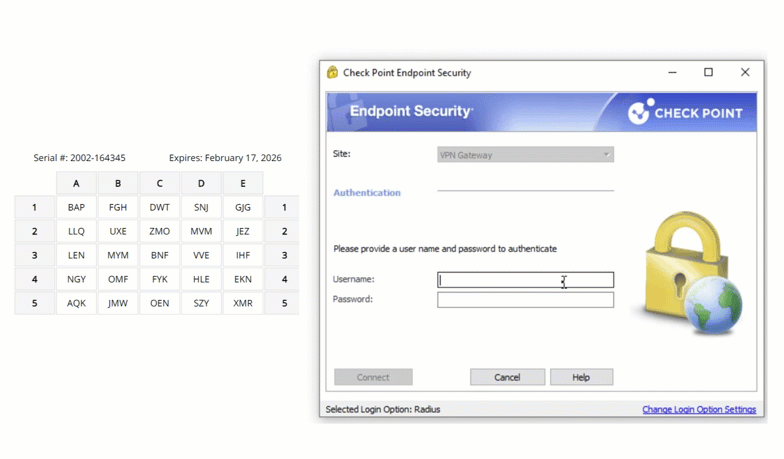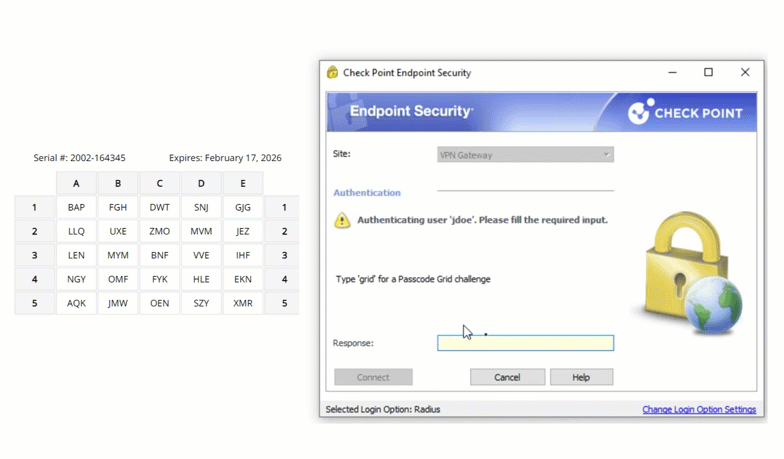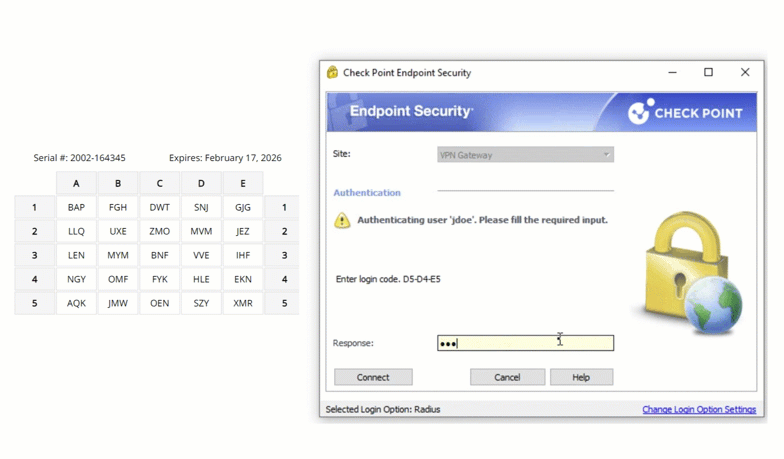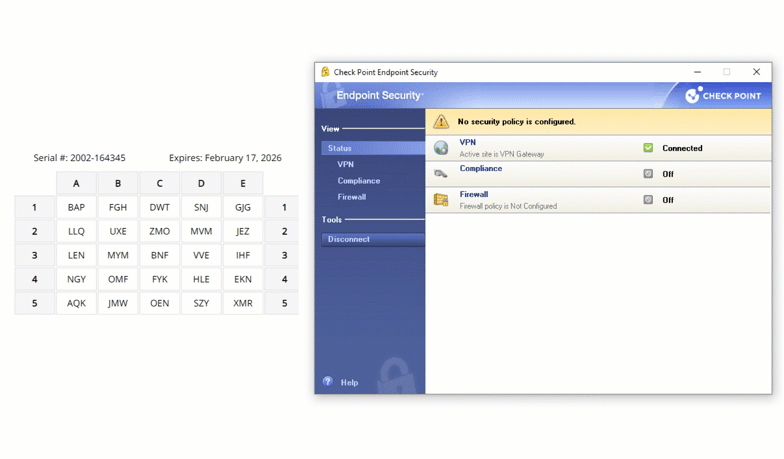
Check Point VPN Multi-Factor Authentication (MFA)
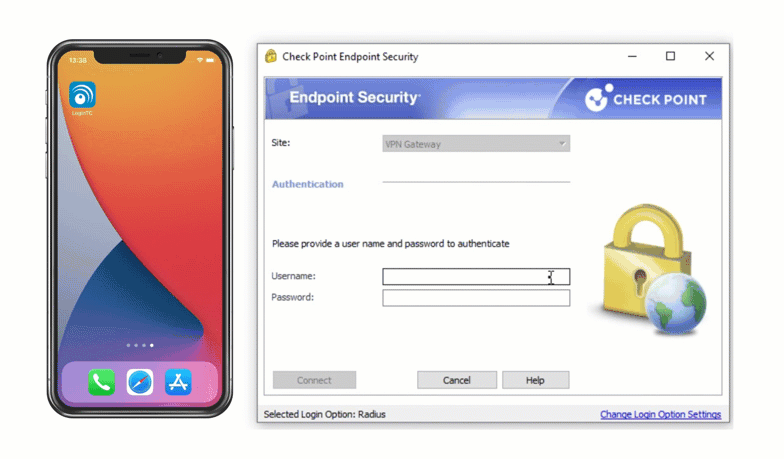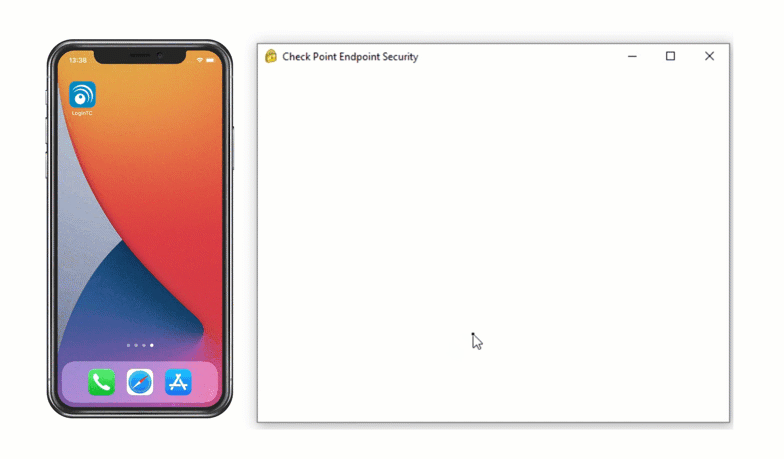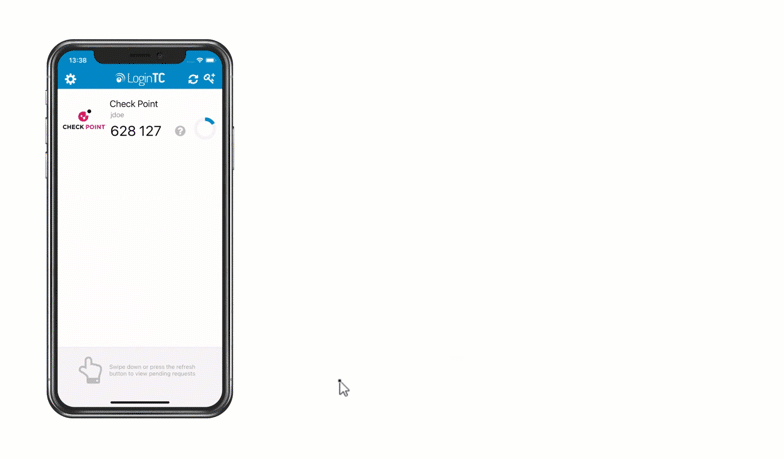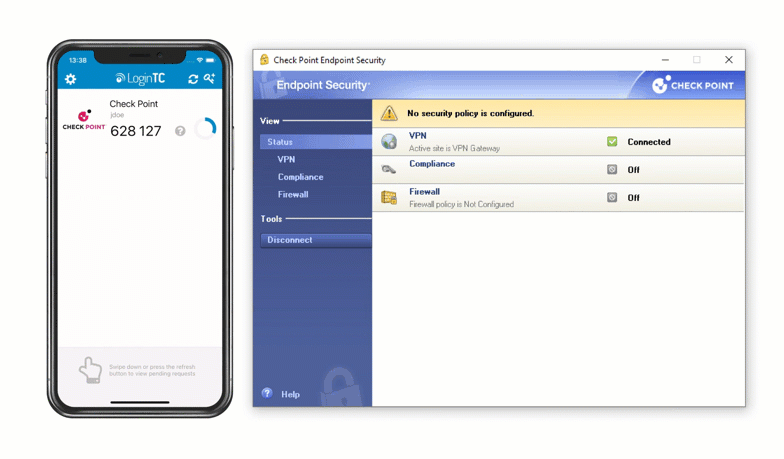
Secure access to Check Point VPN with LoginTC two-factor authentication (2FA). Easy for end-users to enroll and log into Check Point VPN and protected applications. Two-factor authentication helps prevent account takeovers.
Multiple authentication methods like Push-based authentication, Software One-Time Passwords (OTP), Hardware Tokens, Bypass Codes and Email One-Time Passwords ensure end-users can always login securely.
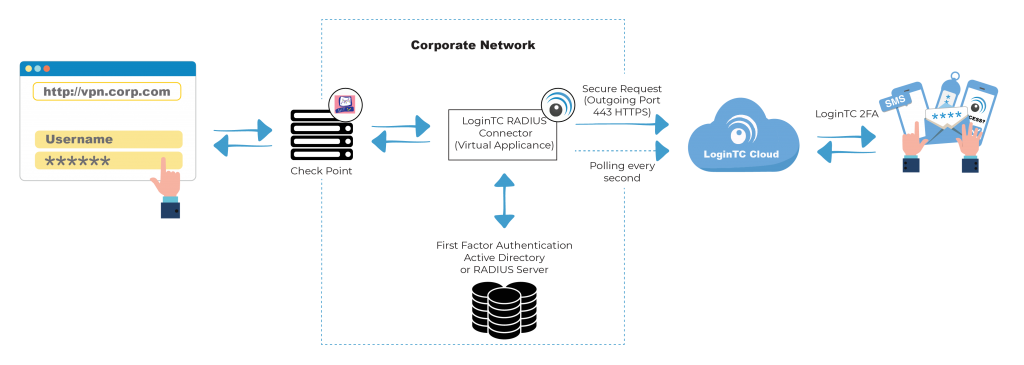
Direct integration with Active Directory means you can still leverage passwords as a first factor. Users can also be synchronized from Active Directory for a streamlined rollout.
Enable LoginTC with Check Point VPN to add multi-factor authentication (MFA) to your remote access deployment and keep your organization secure.