Introducing LoginTC product updates to improve authentication security and administrator processes
December 20, 2022 •
It’s been another fantastic year here at LoginTC!
From the launch of our on-premises MFA solution, LoginTC Managed, to the release of our unique cyber insurance-specific offering, LoginTC Assure, our product and development teams have been hard at work ensuring LoginTC is ready for modern cybersecurity demands.
That’s why we’re excited to close out the year with a major update to our LoginTC Cloud offering. We’ve introduced new features to give you better insights into your LoginTC accounts, especially in the area of authentication security, as well as better leverage intuitive tools for managing your own administrator account.
Let’s dive into these new features below.
Authentication Logs
This new feature has introduced a new tab to the sidebar of your LoginTC Administrator portal. The “Authentication Logs” tab shows a detailed account of all authentication attempts made by your LoginTC users.
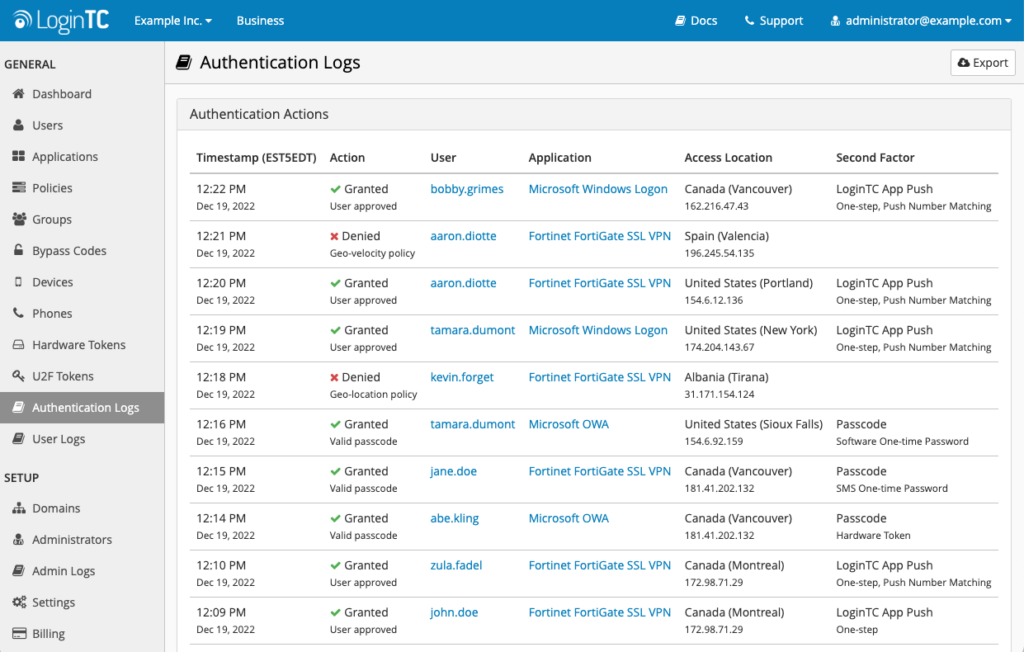
The logs show when the attempted authentication occurred, the user account, the target application, the location and IP address of the authentication request (when available), the method of authentication, and if the request was granted or denied.
In the event of a denied authentication, the logs will explain why the authentication was rejected, such as a policy violation, an invalid attempt, or an unknown user.
You can also view, filter, and export authentication log data going back six months.
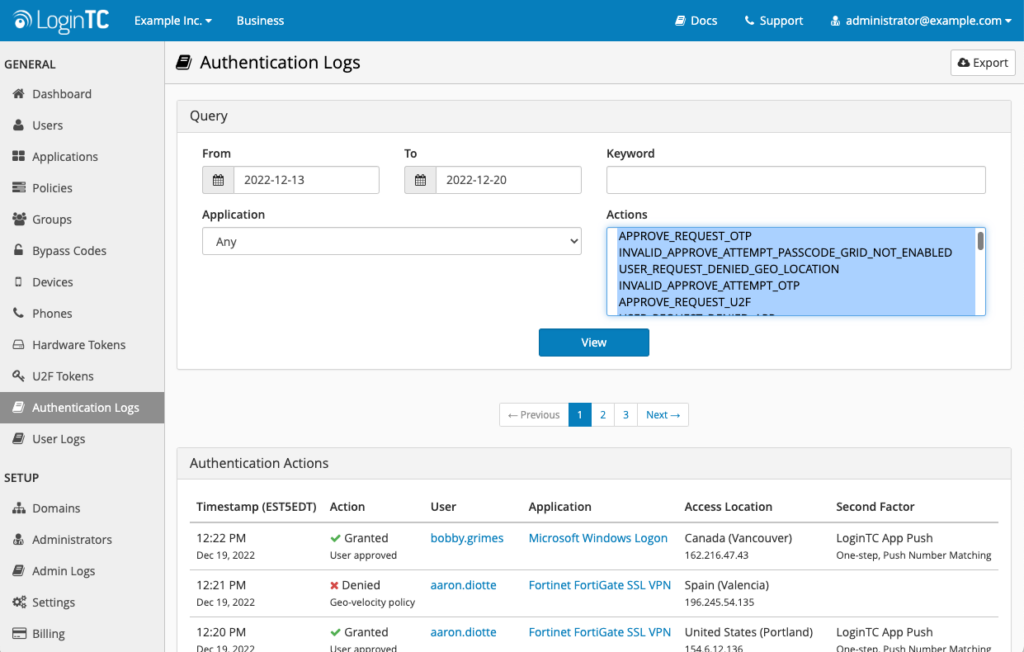
This new feature will give you comprehensive insights into LoginTC authentication actions and arm you with the knowledge you need to track suspicious activity, prompt policy use enhancements, or simply help you better respond to help desk questions from end-users.
For more information on this new feature, check out our Authentication Logs Guide.
Geo-Location Policies
Our new geo-location policy allows you to enforce authentication policies based on the location of the user attempting to log in. LoginTC retrieves geo-location information from the user’s access device IP address when available.
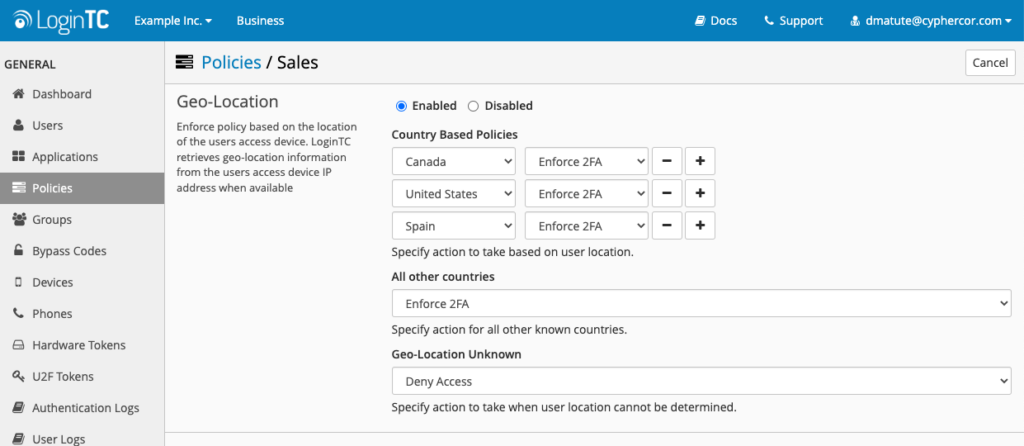
There are three aspects of geo-location policies.
The first aspect is the ability to set a policy based on the specific country that a user is logging in from. For example, you can set your policy so that all users logging in from the United States have 2FA enforced. You can also set a policy to deny access to specific countries.
Once you have your specific country policies set up, the second aspect is to set a policy for what to do with users coming from anywhere else. For example, if you set up your policies so that users from the United States, Canada, the UK, and Australia enforce 2FA, then you deny access to users attempting to log in from any other country.
On the other hand, if you set up your specific country policies to deny access to users logging in from the countries listed, then you can automatically enforce 2FA to users authenticating from all other countries.
Finally, the third aspect allows you to choose what to do with users whose location is unknown. You can either automatically deny or enforce 2FA to users with an unknown location.
Geo-Location policies give improved control over how user access is enforced based on location. Leverage this policy to mitigate malicious actors attempting authentications from countries where your users aren’t located.
For more information check out our Geo-Location Policy Guide.
Geo-Velocity Policies
We have also introduced a new authentication policy related to location tracking. Geo-velocity allows you to specify a maximum distance between a user’s last authentication location and the current authentication location attempt.
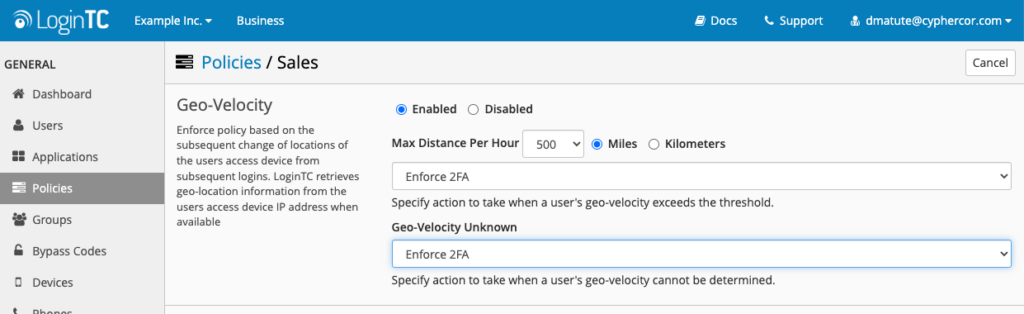
With geo-velocity, you can set a maximum distance per hour that a user can travel in between authentications, in either kilometers or miles.
For example, you could say if a user travels more than 500 miles in one hour, their attempted authentication should be denied. This helps prevent malicious actors from successfully push-phishing users by sending login attempts around the same time they think that the user logs in every day.
As with the geo-location policy, you can also choose what to do if the geo-velocity is unknown — either deny access or enforce 2FA.
To learn more about this new policy read our Geo-Velocity Policy Guide.
Administrator Token Reset
Lastly, we’ve heard from our administrators that resetting administrator tokens on their account was at times difficult. That’s why we’ve introduced improvements to our administrator token reset flow and added a new option to reset your token.
When the device you use to log in to the LoginTC administrator portal is lost or stolen, or you have a planned device change, you now have two options to move your token to a new device.
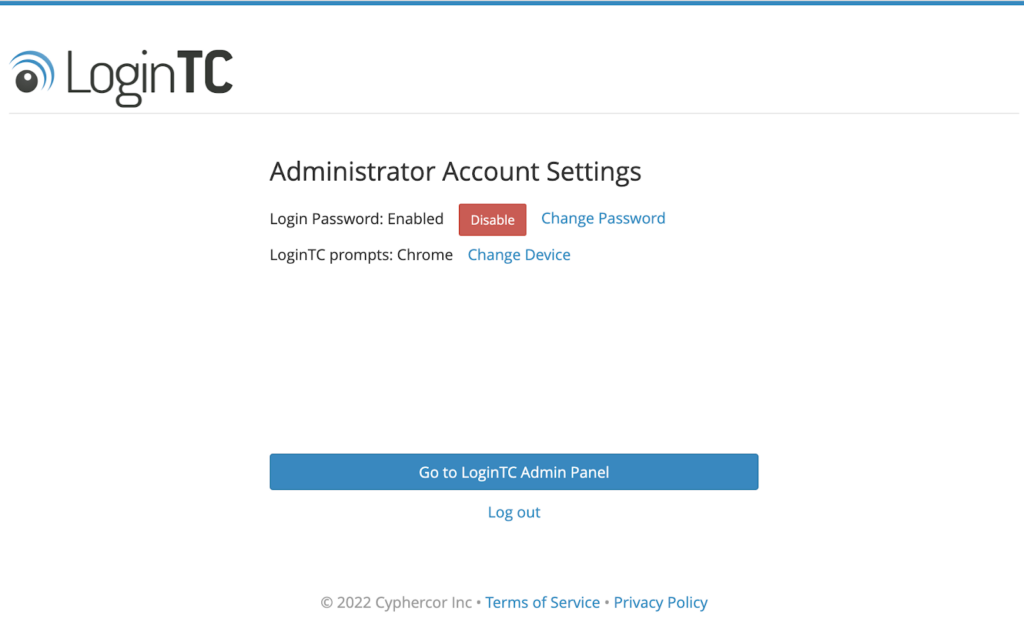
Self-initiated
In the Administrator Account Settings, there is now a Change Device option. This will initiate a token reset directly from an email link. This does not require a Recovery Key or Organization API Key.
Peer-initiated
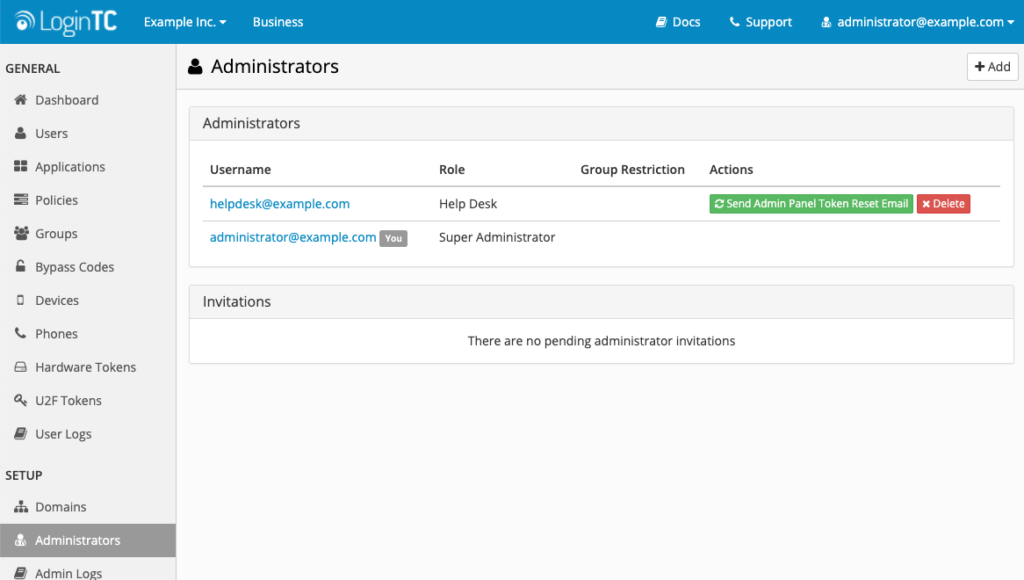
Second, a peer administrator with the SUPER_ADMINISTRATOR role can reset another administrator’s token. Again, without the need for a Recovery Key or Organization API Key. We always recommend having at least two administrators in your LoginTC organization in the event of any access issues, and this is another great reason why you should do that now if you have not done so already.
Thank you for another great year
We want to thank all of our renewing customers, new customers, and industry partners for another incredible year at LoginTC.
We hope these new features will improve your authentication processes and user experience with LoginTC. If you have any questions or want advice about how best to utilize these new policies, contact us today.