SMiShing: The new & dangerous way hackers are infiltrating your smartphone, and what 2FA can do about it
March 24, 2015 •
Last month, we wrote about the prevalence and increasing sophistication of phishing attacks in a blog titled, “Go Phish! No matter what hand you’re dealt, all moves prove risky without 2FA.”
I wish I could tell you the purpose of this blog is to announce that you can forget the last blog because phishing attacks have been eradicated and all is hunky dory as far as safety in cyberspace goes. Unfortunately, that’s not the case.
In fact, someone at our office has been on the receiving end of numerous phishing attempts lately — and not your average, run-of-the-mill phishing emails either. Rather, phishing via SMS also known as SMiShing. With the rise of BYOD (bring your own device) policies among SMB and enterprise organizations, we thought it crucial we bring this topic to your attention.
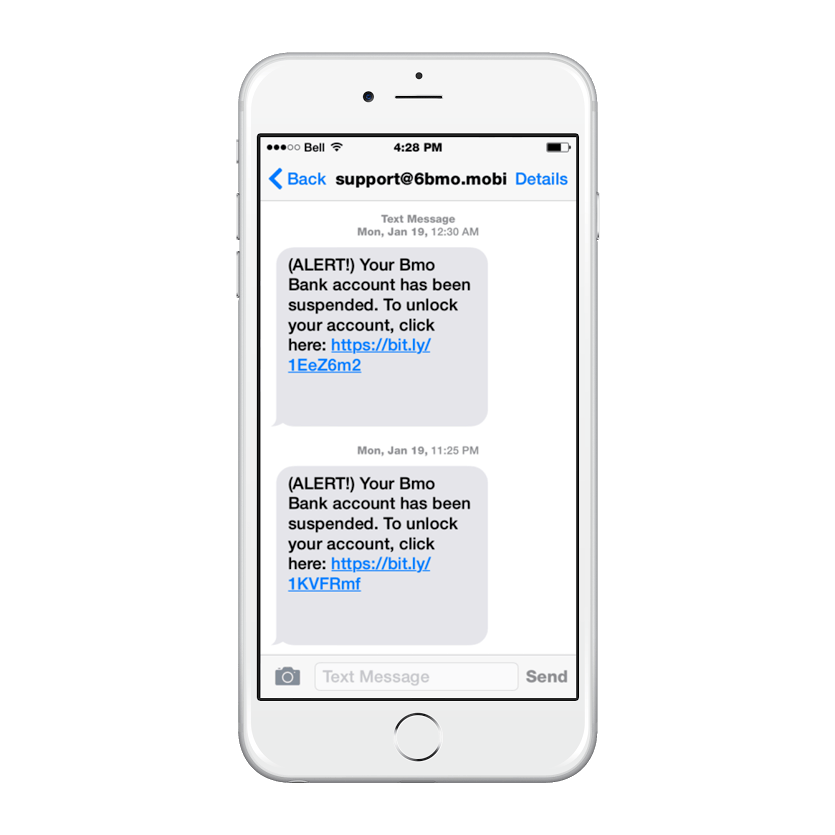
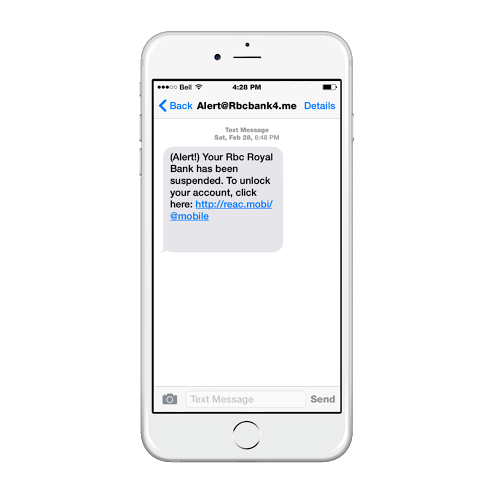
Linda Musthaler, who wrote “How to avoid becoming a victim of SMiShing (SMS phishing),” for Network World, states the following statistics:
- There are more than 6 billion cellphone subscribers in the world.
- Nearly two-thirds of all adults with a cellphone use text messaging.
- More than 90% of text messages are opened within 15 minutes of being received.
“According to Mary Landesman, senior security researcher at Cloudmark, SMS spam campaigns in the U.S. grew by 400% in the first half of 2012, and about one-third of all SMS spam includes SMiShing attempts,” Musthaler writes.
What is SMSiShing?
SMSiShing occurs when an attacker sends a text message (SMS, iMessage, etc.) to your smartphone usually posing as a trusted source (e.g. bank) prompting you to visit a URL. Often, hacker tactics include baiting you with a call to action (e.g. your bank letting you know your account has been suspended or a retailer sending you a free gift card). The URL either takes you to a false website or plants malware on your mobile device. Either method enables the attacker to steal your sensitive personal data (banking information, usernames and passwords, etc.) for malicious purposes.
Why is it dangerous?
By now, most of us are aware of email-based phishing attacks and know which suspicious characteristics to watch out for. We tend to be proactive about protecting our PCs from viruses by investing in antivirus software. The same cannot be said for mobile devices. Additionally, SMS by nature provokes more of a sense of urgency and seems inherently more personal than email does. Therefore, we’re more trusting of SMS, assuming that the sender would have required our phone number to reach us. So, we open messages and click links quickly and without careful consideration of the sender. In other words, there’s no junk mail folder for our text messages leaving us more exposed to vulnerabilities than ever!

How can I protect myself and my business?
Two-factor authentication (2FA) is the best method of protection for mitigating against phishing and other attacks, including SMiShing. However, what kind of 2FA you choose is equally important. Let’s take a one-time password (OTP) based solution as an example. Most OTPs are sent to your phone via SMS. But what good is that if your phone has been infected with malware that “sniffs” all the SMS messages being delivered to the phone? The interceptor would steal, not only your username and password, but also your second-factor credential, the OTP, and log in to your account without issue. With a non-OTP based solution like LoginTC, which uses secure remote password protocol instead, the attacker could not leverage your personal information because they would need to physically possess your LoginTC-thumbprinted device (smartphone, tablet or desktop via Google Chrome) as a second factor.
Conclusion
In other words, LoginTC can keep your smartphone safe USING your smartphone! Pretty neat, right? To secure your digital assets in minutes with LoginTC, get started now. For questions or support, email info@cyphercor.com.