Go Phish! No matter what hand you’re dealt, all moves prove risky without 2FA
February 05, 2015 •
They say ignorance is bliss. But ignorance can also lead you down a nasty path — one paved with fraudulent credit card charges, misappropriated funds, identity theft, or stolen and exposed digital goods: private photos, sensitive documents, emails, data, etc.
I’m talking about phishing. And before I started working as a Communications Specialist for Cyphercor, I was fairly ignorant to it, oblivious to numerous and constant attempts attackers make at hooking me and reeling me in so they can steal my username and password. One successful phishing attempt would have been especially catastrophic for me because, like most of the online population, I used the same password across multiple accounts. It’s bad, I know, but at least it wasn’t “password” or “123456”.
| Phishing [noun /’fiSHiNG/] The activity of defrauding an online account holder of financial information by posing as a legitimate company. ( – Google Definitions) |
Old-School of Phishing
Since we at Cyphercor specialise in defending against phishing (and other sorts of cyberattacks), I grew curious about it quickly, which led me to my junk mail. That’s where I found around 14 new classic-style phishing emails making claims like this one:
| Dear friend, Greetings. I am the manager of bill and exchange in THE BANK. I have a business of 5.5 million United States Dollars to transfer to your account for investment in your country. Get back to me and I will give you full details. |
It’s true that I think cyber-society has progressed to a point where most (but not all) of us are unlikely to fall victim to Nigerian Prince-esque schemes. They’re humorous, even. The real danger lies in what a lot of us don’t realize: modern phishing is becoming increasingly sophisticated — and the consequences are far from funny.
Swimming Toward Sophistication
According to the Anti-Phishing Working Group (APWG), more than 123,700 phishing attacks took place in the first half of 2014 (the second highest since the second half of 2009) and a total of 756 institutions were specifically targeted in these attacks, the largest number ever during a six-month period. Improved phishing techniques include…
- Email Hijacking: A hacker gains access to an individual’s email account and sends phishing emails to all of his/her contacts using the account holder’s real name, making the note much more convincing.
- SMiSHing/Text Messages: With standard SMS formatting, texts are easy to replicate. They generally contain an urgent fear-based call to action (“Your bank account has been suspended” or “You signed up for our service and will be charged X dollars”) in combination with a phony URL link to a page the hacker has set-up.
- Spoofed Websites: The hacker creates a realistic “shadow copy” of the website they’re targeting — perhaps your bank’s sign in page — of which they are in total control in order to steal your personal information. They lure you there with an official looking email (down to a near perfect imitation logo and branding) or text message containing a URL link.
- Operation Huyao: A proxy program inserted between a potential victim and the target website that acts as a relay to the legitimate site. Only pages on which information theft takes place (such as a purchase form) need be modified. This saves the hacker time and makes his/her page much more accurate.
- Trojan Attack: Some hoax emails contain attachments that, when clicked, install malware on your computer to carry out malicious criminal tasks (such as man-in-the-browser, keystroke logging and form grabbing.)
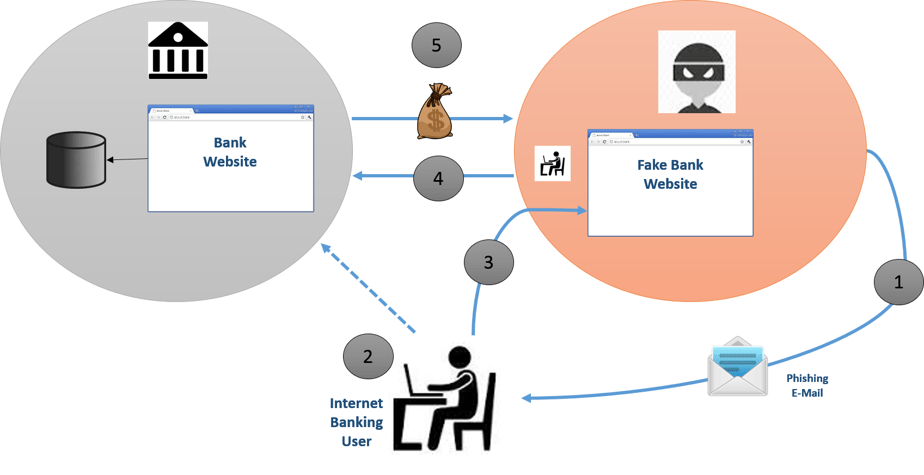
The Bait
A few major companies that were recently subject to phishing-related attacks include Target, the New York Times, Twitter, JPMorgan Chase & Co, and RSA. But bear in mind, while not as widely reported on, small and medium sized businesses are also at risk — even more so.
A Scalable Solution
When it comes to security breaches, instead of simply “What happened?” it is also prudent to ask “What didn’t happen?” In other words, “What was missing that could have prevented the attack?” The answer is a non-OTP (one time password) based two factor authentication solution, such as LoginTC.
Two-factor authentication (2FA) requires that users who attempt to access particular services possess both “something they know” (a password) AND “something they have”. In the case of the RSA, a major 2FA provider, the second factor, or “something you have” component, is typically a hard token that generates one-time passwords (or OTPs). Some OTPs do not really qualify as a second factor. The RSA breach proves that attackers would have means to generate certain valid token values. LoginTC, on the other hand, turns your mobile device (smartphone or tablet) or desktop (via Google Chrome) into the second factor. What does that mean? Well, think about it this way: even if I had explicitly sent “the manager of bill and exchange in THE BANK” my username and password s/he would have no way of infiltrating my account for a LoginTC-enabled service because s/he would not be in possession of my second factor: a smartphone, which I could use to deny any invalid access requests. There are no codes to be copied or OTPs s/he can crack. To learn more about how LoginTC works, click here.
Bottom-line
Phishing attacks as prevalent as ever and only maturing in sophistication — they’re not just for duds anymore. And before I joined the LoginTC team, I was a big juicy tuna flapping its tail above the water, calling phishermen directly to me with my splash. I have since varied my passwords and enabled 2FA wherever possible. If you want to keep your business afloat safely, without sinking its security, use the trusted two-factor authentication of LoginTC.