Simple Two-Factor Authentication for VPNs and remote access
July 15, 2013 •
LoginTC provides a simple and effective way to secure remote access your IT infrastructure. Whether you are looking to be PCI-DSS compliant, following industry regulations or wanting to beef up your remote access security without the hassle of deploying hard tokens, look no further. Our connector suite allows enterprise administrators to add two-factor authentication to virtually any identity and access management deployment.
Let’s take a closer look at how the LoginTC RADIUS Connector adds two-factor authentication to your VPNs. We currently support the most widely used VPNs, Cisco ASA, OpenVPN, Barracuda, Juniper, and are constantly adding more to this list.
Leverage existing infrastructure
First off, we will make a few assumptions. Your infrastructure includes a VPN which is currently using a single password factor for authentication (i.e. Active Directory, LDAP or perhaps a RADIUS based system) or an existing multi-factor solution which is too burdensome to continue with (i.e. hard tokens).
Below is a simple architecture diagram which demonstrates how the LoginTC RADIUS Connector integrates into your infrastructure.
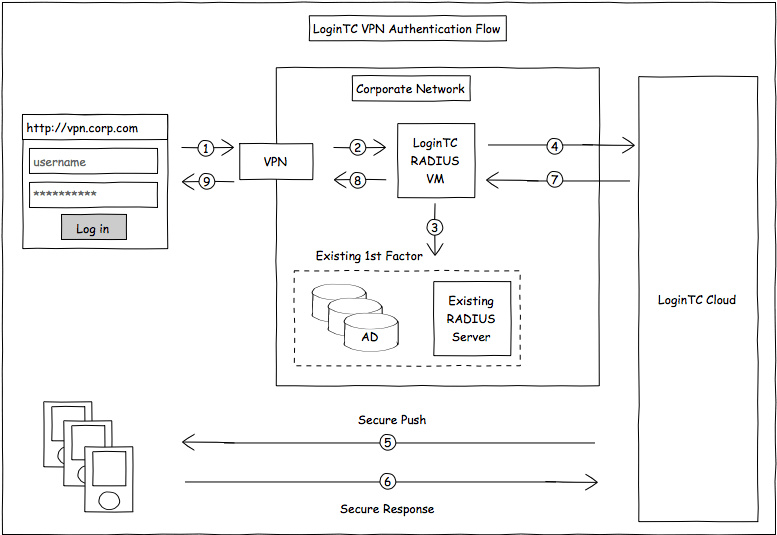
The connector is a light-weight virtual machine which sits in your infrastructure in between your VPN and existing first factor. Think of it as a proxy to the LoginTC service which augments your existing method of authentication with a mobile second factor. Breakdown of the steps:
- User launches their favourite VPN client and connects with their username and password (this can also be web based)
- The VPN sends a RADIUS request to the LoginTC RADIUS Connector
- A request is sent to verify the username and password locally (passwords never leave your infrastructure)
- If the first factor is valid send a request to the LoginTC managed service
- Request sent to provisioned device, check out Multi-factor Flow for more information
- Response from provisioned device, check out Multi-factor Flow for more information
- LoginTC RADIUS Connector verifies the state of the transaction
- LoginTC RADIUS Connector sends back OK OK to VPN
- VPN grants access to the user
This all takes place in virtually the same amount of time it would take a user to authenticate for existing remote access! Existing password policies and first-factor security policies remain untouched. The passwords themselves never leave your premise.
Easy to setup
A core tenant of the LoginTC family of products and services is to make it easy for users and administrators. Our configuration-driven setup reduces the time dramatically to pilot and deploy the solution. The LoginTC RADIUS Connector also comes with useful testing tools to verify your setup with ease.
User Migration
You will be able to run in dual mode and as the rollout of the augmented authentication happens. Configure your VPN to use the LoginTC RADIUS Connector for users that are already provisioned using group assignments. You can also configure the connector to authenticate only using first factor until your users have been migrated.
There are several options for managing your users within LoginTC:
- Individual users can be added manually in LoginTC Cloud
- Bulk operations in LoginTC Cloud
- Programmatically manage user lifecycle with the REST API
- One-way user synchronization of users to the LoginTC Cloud is performed using LoginTC Sync Tool.
