How VPN admins & security managers use LoginTC to protect their networks
February 25, 2015 •
With the threat of cyberattacks constantly looming, IT professionals know that password-only protection is simply not enough to safeguard the corporate resources that run behind virtual private networks (VPNs). That’s especially true right now with a rising number of workers accessing office VPNs remotely. As a result, experts are urging businesses to adopt two-factor authentication (2FA).
Here’s some insight into how VPN administrators and security managers use LoginTC 2FA to protect their networks.
Cost and Administration
LoginTC, a cloud-based 2FA solution, leverages existing mobile and virtualization investments, which means it does not require any additional hardware. Rather, it integrates seamlessly with a virtual host, an existing VPN appliance — from Cisco to WatchGuard — and end users’ smartphones, tablets or desktops. This nullifies overhead expenses while improving user experience.
- Admins use a web-based GUI to install/configure the LoginTC virtual machine on their host server.
- End-users install the LoginTC app on the device of their choice (iOS, Android, Google Chrome) where they will receive access requests via wireless push notifications.
- The VPN administrator manages VPN integration and end-users’ lifecycles with web-based tools that are easy-to-use and cryptographically protected.
- With no start-up fees, license renewals or expirations, LoginTC costs between $2.00 and $3.00/user per month, is free for 3 users, and offers substantial volume discounts.
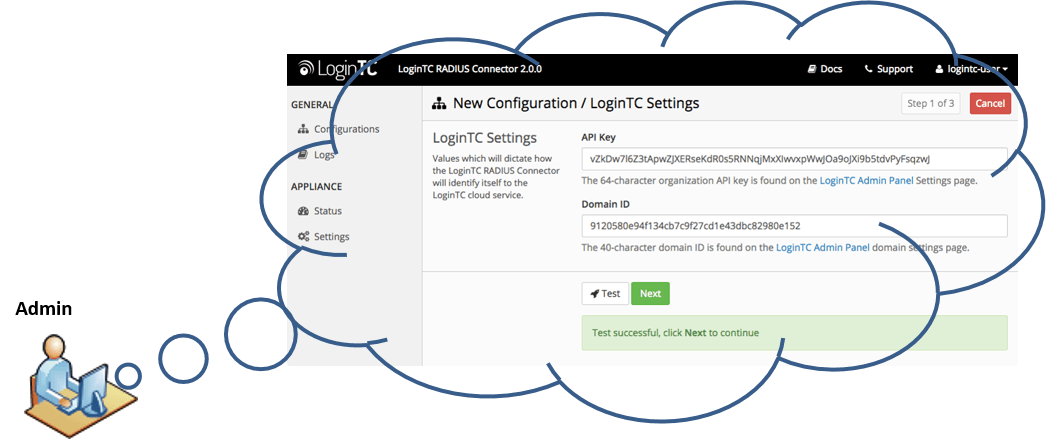
Registration and Provisioning
Scalable for millions of users, without the headache of keeping any inventory in stock, LoginTC admins issue and revoke user tokens from the cloud-based Admin Panel accessible in their browsers. Admins select the method of user registration and provisioning that works best for them and execute it from the Admin Panel:
- Manual
- Self-registration
- Bulk Upload (.csv)
- Sync with LDAP/AD directory
- REST API
On top of that, LoginTC integrates seamlessly with single sign-on (SSO) and SAML federation systems.
Security and Compliance
Through the use of Secure Remote Password (SRP) protocol, LoginTC provides premium-level, Government-trusted security, which — when enabled — helps businesses and organizations become PCI DSS, HIPAA and FFIEC compliant. This system has two major advantages, which Grant Moerschel points out in his InformationWeek article, “The Fuzzy Future of Identity Management.” He says:
- First, Salesforce doesn’t need personally identifiable information such as a phone number because tokenized challenges travel over the certificate-based Android, Apple, and BlackBerry push notification networks. Eliminating stored personal information simplifies regulatory compliance.
- Second, there are no vulnerable OTP [one time password] codes being transmitted through insecure channels such as SMS or via automated phone calls or via cycling hardware tokens that are then entered into some remote web interface form that might or might not be legitimate. And there’s a third factor: It uses the smartphone that salespeople already carry. Simplicity like this is key to getting employee adoption.
User Adoption
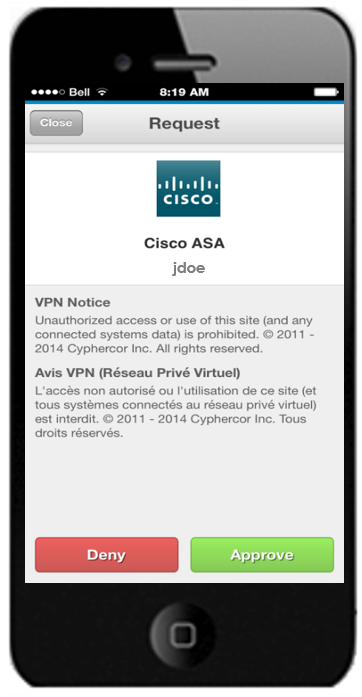
When end-users are empowered to employ their own choice of device (particularly relevant in a BYOD context) for 2FA — rather than a foreign object, such as a key fob — little to no training is required. Plus, with LoginTC’s simple 3 step system (receive, decide, unlock) users are likely to adopt the new practice more easily and more quickly, and are less likely to lose the technology at hand. When end-users are happy, administrators get to focus on other important tasks.
Proof of Concept
Some admins have carried out a Proof of Concept (PoC) before committing to LoginTC. LoginTC lends itself well to this because the LoginTC Starter Package is free for up to 3 users. The Starter Package has full-fledged functionality minus the added benefit of bonus features. This means potential customers can fully experience exactly how LoginTC will work in the specific context of their company before purchasing it.
For example, if an admin wishes to set-up 2FA for all of his/her e-commerce business’s corporate resources, which include a VPN for employee access to email and documents, as well as a WordPress content management system as a customer website, s/he could do so very easily for up to 3 users. If satisfied, the admin would simply upgrade the subscription in the Admin Panel.
To learn more about implementing LoginTC 2FA for VPNs, click here.
To stop reading about LoginTC and experience it for yourself, get started in minutes.