Smart Authentication
August 30, 2013 •
User experience is tied to user adoption. A security process works as long as users are bought in and willing to participate. If the process is too cumbersome, users will take the path of least resistance and ultimately expose backdoors originally unintended.
Let’s talk about two of the major actors: administrators and end-users.
Administrators
Administrators want something secure, easy to provision / de-provision and get accurate reports on. They want to reduce intrusion and attacks to 0, consistency across all machines and reduced calls to their helpdesk. The more the security solution does for them, the more time and budget they can spend on other areas of their infrastructure.
End-users
For users the authentication approach should be convenient and simple to use. Users nowadays want to be able to connect from anywhere on any device. Security is assumed. The simpler the process the more the users will use and ultimately access the protected data and services. More data and services accessed means more work done, more products/services purchased etc…
It’s a win / win / win when users are happy and secure.
Smart Authentication
The important balance between usability and security is something we think about everyday while designing and building LoginTC.
Step 1: Receive
Instead of an OTP, the mobile networks identify the users previously provisioned device as the 2nd factor. A secure notification is sent directly to the user’s smartphone. This is not an SMS, rather a native notification which allows the user to launch directly into the mobile app.
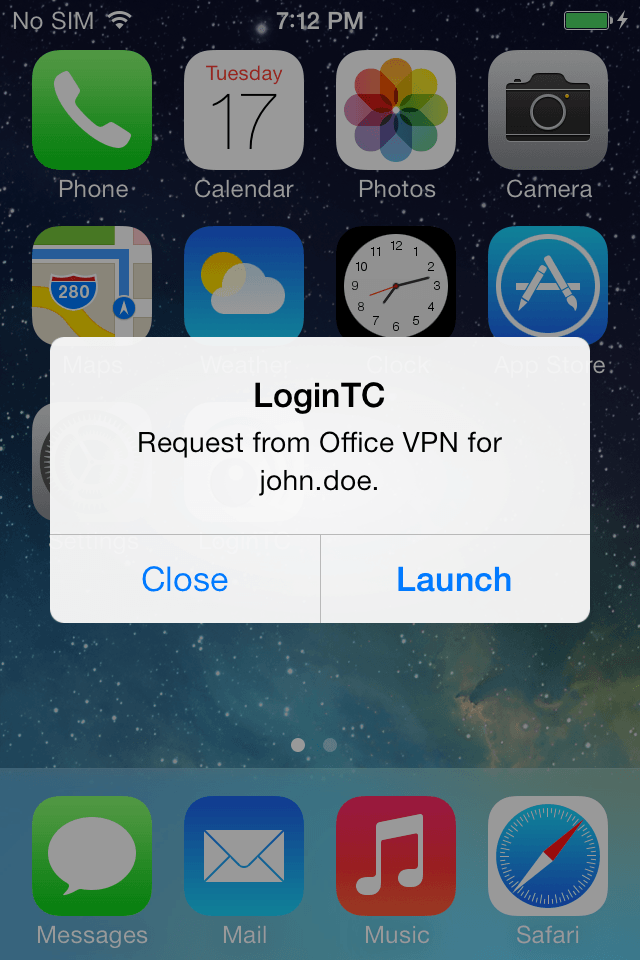
Step 2: Decide
In one screen a user can make an informed decision as to whether to approve or deny a request. Along with a custom pictogram, transaction specific attributes are included along the service and username. These attributes can be static (i.e. a legal disclaimer) or dynamic (i.e. geo source of request) based on domain specific settings.
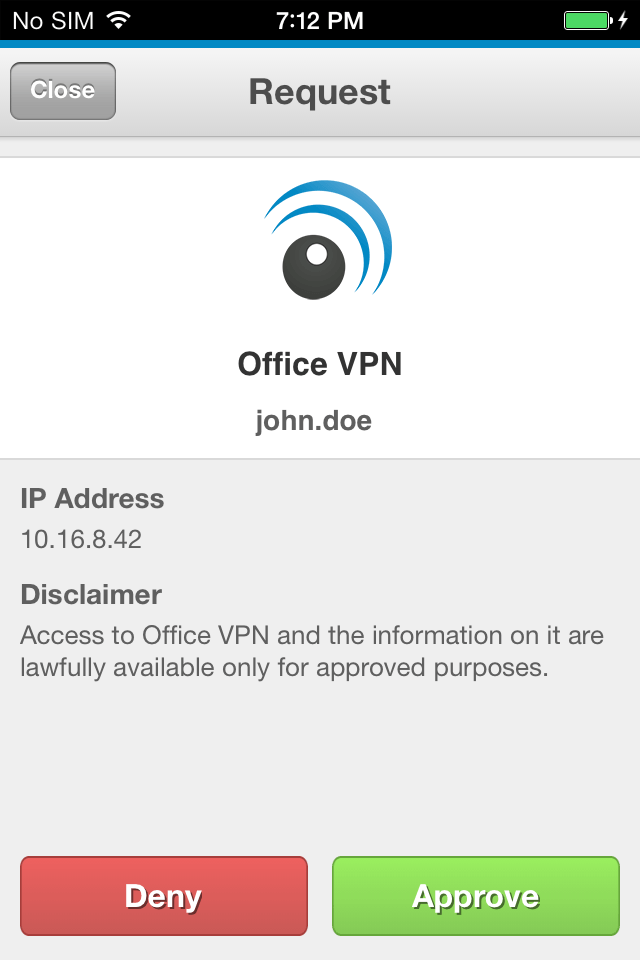
Step 3: Unlock
An administrator can also select which unlocking policy a user uses for accepting a request. A 4-digit or a passcode can be employed. Administrators can define additional policies, like passcode length, for even greater control over the authentication process.
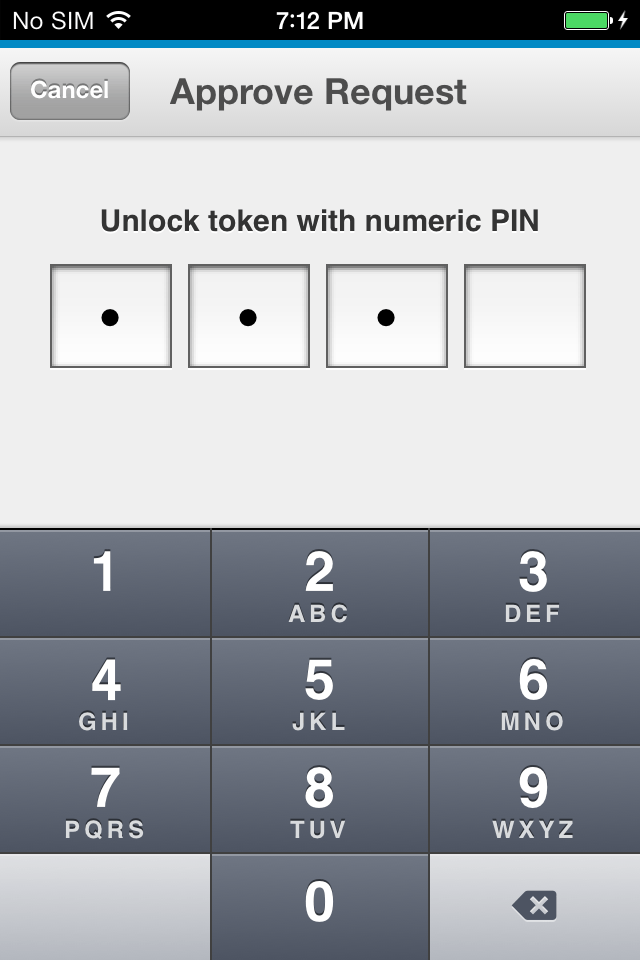
Conclusion
Giving end-users a best in class authentication experience will keep them happy and bought into the process. Happy users means less helpdesk calls and headaches for administrators. All the while the organization benefits from secure access to networks, data and services.
Win / Win / Win.