Latest RADIUS Connector updates from LoginTC
May 14, 2025 •
Version updated to 4.1.5
An issue affecting upgrades from older versions of the LoginTC RADIUS Connector was identified in version 4.1.4. This has been resolved in version 4.1.5.
The latest update to the LoginTC RADIUS Connector improves the reliability of security features introduced in our previous release, and adds new functionality to better protect your organization.
Explore what’s in the latest release below.
Auto mode for Message-Authenticator and Proxy-State
In the summer of 2024, a new major vulnerability was discovered in the RADIUS protocol, known as Blast-RADIUS. As part of the attack mitigations, researchers recommended authentication clients include a Message-Authenticator attribute on each request, including where a Proxy-State attribute is present.
When LoginTC implemented this change as part of our mitigation efforts in version 4.0.11, the default option was set to Enabled. This created issues for administrators using VPNs or Firewalls that did not support the Blast RADIUS-recommended mitigations. In such cases, the Message Authenticator attribute was not compatible with the RADIUS client, and administrators were required to explicitly disable the feature to maintain connectivity.
As part of the latest release, the default is now set to Auto. This means the LoginTC RADIUS Connector will automatically determine whether the Message Authenticator requirement can be enabled. This detection occurs on the first RADIUS request. If the feature is supported, Message Authenticator attributes will be included in all subsequent requests. If not, the feature will remain disabled moving forward.
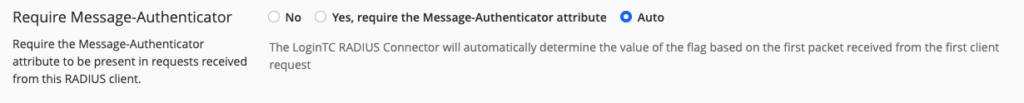
This functionality has also been implemented for requests where there is a Proxy-State attribute present.
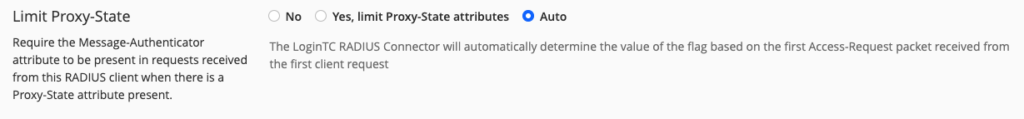
This change should make the setup process easier for administrators working with all types of RADIUS clients, although we do recommend implementing Blast-RADIUS mitigations as soon as possible.
EAP protocol support
Previously, the LoginTC RADIUS Connector supported Password Authentication Protocol (PAP) as the sole available protocol for authentication. The latest release has added support for the Extensible Authentication Protocol (EAP) as well.
EAP has increasingly become a more popular authentication protocol for some VPNs, such as Palo Alto. Additionally, some compliance standards, such as FIPS 140, require EAP-based authentication.
While authentication method capability is more limited with EAP authentication, providing support for basic methods will allow more organizations to add MFA using the EAP protocol.
Syslog improvements and package upgrades
Additional improvements in this update include new syslog performance capabilities and package upgrades. Previously there was a performance issue that occurred when the Syslog server was unreachable while using a certain transport protocol (TCP), which has now been fixed.
Conclusion
The LoginTC RADIUS Connector is a powerful tool to add comprehensive MFA to any RADIUS-speaking advice. If you have questions about this latest release, or the connector itself, feel free to contact us.