A CISO’s Guide to Multi-Factor Authentication Solutions
February 06, 2026 •

As a CISO, you know that implementing multi-factor authentication is a non-negotiable step in securing your organization. Yet, the path forward is rarely clear. Navigating the crowded landscape of multi factor authentication solutions can feel overwhelming, especially when balancing the need for robust security with practical realities. Concerns over complex integration with legacy systems, the debate between on-premises and cloud deployments, and the risk of a poor user experience causing employee friction are valid and significant hurdles.
This guide provides the clarity you need. We are here to help you cut through the noise and make a confident, informed decision. You will learn how to evaluate the key differences between MFA models, find a solution that integrates seamlessly with your current infrastructure, and improve your security posture without frustrating your employees or overloading your IT team. The right MFA solution delivers peace of mind, not more problems.
Key Takeaways
- Understand how your deployment model-cloud vs. on-premises-critically impacts your organization’s security, control, and compliance.
- Learn to assess the real strength of an MFA system by analyzing the specific combination of authentication factors it supports.
- Develop a structured evaluation process to compare multi factor authentication solutions, focusing on core technical capabilities over marketing claims.
- Discover the essential enterprise-grade features that go beyond basic MFA to simplify administration and strengthen your security posture.
Table of Contents
- Understanding the Core Types of MFA Solutions: Beyond the Cloud
- Key Authentication Methods: A Look at the Factors
- How to Evaluate and Choose the Right MFA Solution for Your Business
- Essential Features of an Enterprise-Grade MFA Solution
- Why LoginTC is the ‘Simply Strong’ Choice for Your Organization
Understanding the Core Types of MFA Solutions: Beyond the Cloud
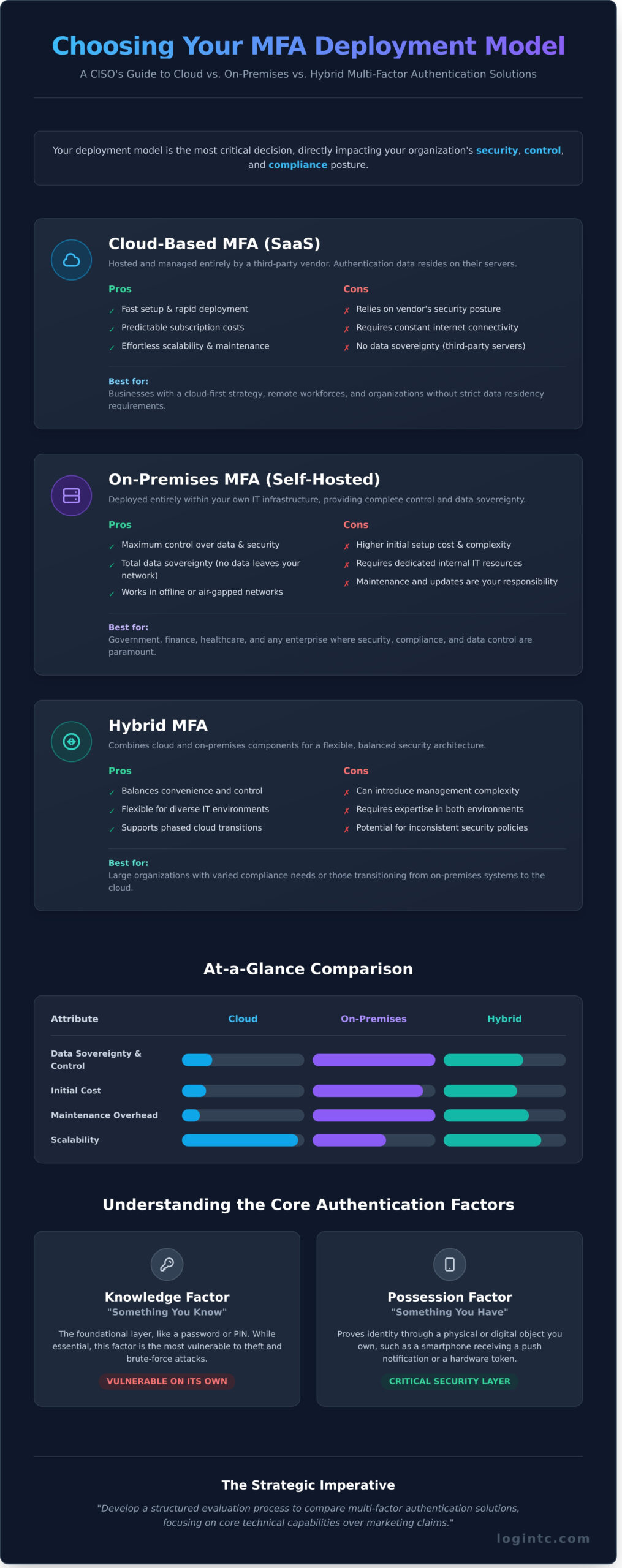
Implementing strong security is non-negotiable, but not all multi factor authentication solutions are created equal. Your most critical decision is the deployment model, as it directly impacts your security, control, and compliance posture. While the fundamental goal is always to verify user identities using multiple credentials (for a foundational overview, see what Multi-Factor Authentication is), how you deploy it matters immensely. The choice between cloud, on-premises, or a hybrid approach involves clear trade-offs, and your organization’s specific risk profile will determine the best path forward.
Cloud-Based MFA Solutions (SaaS)
A cloud-based or SaaS MFA solution is hosted and managed entirely by a third-party vendor. This model offers rapid deployment and lower initial overhead, as there is no hardware to procure or software to install. Updates and maintenance are handled automatically, ensuring you always have the latest security features.
- Pros: Fast setup, predictable subscription costs, and effortless scalability.
- Cons: Relies on vendor security, requires constant internet connectivity, and your authentication data resides on third-party servers.
- Best for: Businesses with a cloud-first strategy, remote workforces, and organizations without strict data residency requirements.
On-Premises MFA Solutions (Self-Hosted)
An on-premises solution is deployed entirely within your own IT infrastructure, giving you complete control over your data and security environment. This model is essential for organizations that cannot have authentication data leaving their network, ensuring total data sovereignty and peace of mind.
- Pros: Maximum control over data, enhanced security in a trusted environment, and functionality in offline or air-gapped networks.
- Cons: Higher initial setup cost and requires dedicated internal IT resources for ongoing management and maintenance.
- Best for: Organizations with stringent compliance requirements (healthcare, finance, government), high-security needs, or isolated networks.
Hybrid MFA Solutions
A hybrid model combines the best of both worlds. You can keep sensitive authentication data and mission-critical systems on-premises, while leveraging the cloud for flexibility and scalability where appropriate. This model allows you to apply different security controls to different parts of your environment, ensuring that highly sensitive resources remain fully protected within your network while cloud resources maintain convenience.
- Pros: Tailored security, optimal flexibility for complex IT environments, and the ability to evolve your deployment model over time.
- Cons: Increased complexity in initial architecture planning and requires careful policy management to maintain consistent security.
- Best for: Enterprises undergoing digital transformation or those requiring different security levels for different application tiers.
Your deployment choice is a strategic decision. It is essential to align it with your organization’s risk tolerance, compliance obligations, and operational reality. No single model is universally superior, and the right choice will always depend on your unique circumstances. By understanding the implications of each approach, you can make a confident, informed decision that strengthens your security posture and brings peace of mind.
Key Authentication Methods: A Look at the Factors
Understanding the strength of multi factor authentication solutions requires a deeper look at the specific authentication methods, or “factors,” they employ. Not all factors provide the same level of security. The power of MFA lies in combining factors from different categories, ensuring that even if one factor is compromised, your data remains protected. Here is how to evaluate the essential authentication methods used in modern MFA systems.
Knowledge Factors: Something You Know
This is the traditional cornerstone of authentication, including passwords, PINs, and security questions. While familiar, knowledge factors are the weakest link in the security chain because they are easily shared, forgotten, or stolen through phishing. They are a necessary foundation, but they are not sufficient on their own for robust security. Your MFA solution must add additional, stronger factors to this base.
Possession Factors: Something You Have
Possession factors are physical or digital items that uniquely belong to a user. These include:
- Hardware Tokens (Security Keys): Physical devices like YubiKeys that generate secure, one-time codes. These provide exceptional security because they are phishing-resistant and require physical presence.
- Authenticator Apps: Software-based tokens that generate time-based one-time passwords (TOTP). Apps like Google Authenticator or the LoginTC app offer a strong, convenient balance of security and usability.
- Push Notifications: These prompt users to approve or deny authentication attempts directly on a registered mobile device. They are user-friendly and secure when implemented correctly, and they eliminate the manual entry of codes.
- SMS and Email Codes: Though better than no MFA, these are the least secure possession factors due to interception risks like SIM swapping. Modern security standards discourage reliance on SMS for sensitive applications.
Inherence Factors: Something You Are
Biometric authentication verifies your identity through unique physical characteristics. This includes fingerprints, facial recognition, iris scans, and voice patterns. Biometrics are incredibly convenient and difficult to replicate. However, they require specialized hardware and raise important privacy considerations. For many enterprises, biometrics are ideal for high-security scenarios or when combined with other factors for maximum protection.
Adaptive and Contextual Authentication
Modern MFA solutions go beyond static factors by incorporating contextual data to assess risk dynamically. This includes analyzing factors like device fingerprinting, geolocation, network environment, and user behavior patterns. By continuously evaluating the risk of each authentication attempt, these systems can intelligently require additional factors only when needed, striking the perfect balance between security and user experience.
A robust MFA strategy is not just about adding more factors—it is about choosing the right combination. Your solution should support a diverse range of authentication methods, allowing you to match the security level to the sensitivity of the resource being accessed. By implementing a layered, flexible approach, you create a simply strong defense that adapts to evolving threats and protects your organization with confidence.
How to Evaluate and Choose the Right MFA Solution for Your Business
Selecting the right multi factor authentication solutions is a critical decision that requires careful evaluation of your unique business needs and technical landscape. There is no one-size-fits-all solution, and a methodical approach is essential to avoid costly mistakes or poor user adoption. This section provides a structured framework to help you confidently assess and compare MFA platforms, ensuring your investment delivers both robust security and operational efficiency.
Define Your Security and Compliance Requirements
Start with the fundamentals. Identify your regulatory obligations (such as PCI DSS, HIPAA, GDPR, or SOC 2) and your internal security policies. Do you require data residency controls? Are you mandated to use phishing-resistant authentication? Does your industry demand air-gapped or offline capabilities? These baseline requirements immediately narrow your options and ensure you do not waste time on solutions that cannot meet your compliance needs.
Assess Integration Capabilities with Your Existing Infrastructure
Your MFA solution must integrate seamlessly with your current technology stack. Make a comprehensive inventory of every system requiring protection: VPNs, cloud applications (Office 365, Google Workspace, Salesforce), on-premises servers, SSH access, legacy applications, and VDI environments. Verify that your prospective solution provides native integrations or well-documented connectors for all these systems. Pay close attention to the complexity of the integration process, including whether APIs are available and whether the vendor provides professional services support. A solution that does not protect your entire ecosystem is a solution that leaves dangerous gaps.
Evaluate Scalability and User Management
Your business will grow and change, and your MFA solution must grow with it. Evaluate how easily you can onboard new users, manage user groups, and adapt policies for different departments or roles. For large organizations, the ability to automatically provision users through directory sync (Active Directory, LDAP, Azure AD) is essential. Consider how the solution handles license management and whether it can accommodate seasonal fluctuations or mergers. Scalability also includes the user experience: will it remain fast and reliable as your user base expands?
Test the User Experience
Even the strongest MFA solution will fail if users refuse to adopt it or constantly call IT for support. Request a pilot or proof of concept to evaluate the end-user experience. Is the authentication process intuitive across all supported methods? How quickly can new employees register their devices? Does it work smoothly on both desktop and mobile? Does the solution offer self-service capabilities for device management and password resets? A positive user experience translates to faster rollout, lower support costs, and better security compliance.
Consider Total Cost of Ownership (TCO)
Look beyond the sticker price. Calculate the total cost of ownership over a multi-year period, including licensing fees, infrastructure costs (for on-premises deployments), integration expenses, training, and ongoing support. Factor in the cost of downtime or security breaches that may result from a poorly implemented solution. While cloud solutions often have lower upfront costs, on-premises deployments may offer better long-term value for large organizations with existing infrastructure. Choose the model that aligns with your budget and delivers the best return on security investment.
Verify Vendor Reputation, Support, and Certifications
Your MFA provider is a security partner, and trust is paramount. Research their reputation in the market, read independent reviews, and speak to existing customers if possible. Verify that the vendor holds relevant security certifications, such as ISO 27001 or SOC 2. Evaluate the quality and responsiveness of their customer support team—do they offer 24/7 availability for critical incidents? Are they knowledgeable about your specific use cases? A vendor who understands your challenges and provides expert guidance is a strategic asset. For a deeper understanding of comprehensive security measures, review compliance frameworks and certifications.
By following this structured evaluation process, you transform vendor marketing into actionable insight. You will confidently select the MFA solution that provides simply strong security, protects your business, and brings lasting peace of mind.
Essential Features of an Enterprise-Grade MFA Solution
A truly effective MFA solution goes far beyond basic two-factor authentication. For enterprises, the right platform must deliver a comprehensive set of advanced features that simplify administration, ensure compliance, and strengthen security posture across your entire organization. Here are the essential enterprise-grade features that distinguish a robust multi factor authentication solutions platform from a basic offering.
Centralized Management and Administration
Managing MFA across hundreds or thousands of users should not be a nightmare. An enterprise-grade solution offers a single, unified console where administrators can oversee the entire system. This includes viewing all active users, monitoring device registrations, managing group policies, and troubleshooting authentication issues from one place. Look for role-based access controls (RBAC) within the admin console so that different IT teams can manage only their relevant areas, ensuring both security and operational efficiency.
Seamless Directory Integration
Manual user provisioning is not scalable. Your MFA solution must integrate directly with your existing directory services-such as Active Directory, Azure AD, or LDAP-to automatically sync user accounts, groups, and attributes. This ensures that new employees are instantly protected when they join, and access is immediately revoked when they leave. Seamless directory integration eliminates administrative overhead and significantly reduces the risk of orphaned accounts or access control errors.
Comprehensive Auditing and Reporting
You cannot protect what you cannot see. Robust logging and reporting are essential for both security forensics and regulatory compliance. An enterprise solution must provide a clear, immutable audit trail of every authentication event. Key functions include:
- Detailed Event Logs: Track every login success, failure, device used, and geographic location in real time.
- Compliance-Ready Reports: Generate reports for audits like PCI DSS, HIPAA, and ISO 27001 with ease.
- Threat Visibility: Quickly identify suspicious patterns, such as multiple failed attempts or logins from unusual locations, to accelerate incident response.
Flexible Policy Engine
Your business has unique rules, and your security should enforce them. A flexible policy engine gives administrators granular control to create and apply custom access rules. This empowers you to enforce specific authentication methods for different user groups, applications, and network zones. For example, you can require a hardware token for administrator access to critical servers while allowing a simple push notification for access to less sensitive applications.
Ultimately, the right enterprise multi factor authentication solutions provide peace of mind by delivering simply strong security that is both powerful and pragmatic. They are designed to give your IT team complete control, ensuring your security framework supports your business operations, not the other way around. To see how these features work in a real-world deployment, explore solutions designed for effortless administration and intuitive use.
Why LoginTC is the ‘Simply Strong’ Choice for Your Organization
When evaluating multi factor authentication solutions, organizations often face a difficult choice between robust security and user-friendly implementation. At LoginTC, we believe you shouldn’t have to compromise. Our business is protecting your business, and we built our solution from the ground up to solve complex enterprise security challenges with unparalleled ease. This ‘Simply Strong’ philosophy is reflected in every aspect of our product, from deployment to daily use.
We provide robust, enterprise-grade security with an intuitive experience for everyone, because we believe administrators are users too. A streamlined management console and effortless end-user authentication mean you spend less time on support tickets and more time on strategic initiatives.
Unmatched Deployment Flexibility
Your security infrastructure is unique, and your MFA solution should adapt to it, not the other way around. We give you complete control over your data and deployment model.
- Choose Your Model: Deploy on-premises, in a completely air-gapped environment, or use a hybrid model to fit your exact security and compliance requirements.
- Maintain Full Control: With our on-premise solution, your authentication data never leaves your network, ensuring maximum privacy and data sovereignty.
- Deploy with Speed: Get fully operational in as little as one hour, not the days or weeks required by other vendors.
Built for Seamless Integration
A security solution is only effective if it protects your entire technology stack. LoginTC is designed to work with the systems you already have, securing everything from modern cloud applications to legacy hardware. Our extensive library of connectors protects critical access points including VPNs, Windows Logons, SSH, and RADIUS-based clients. Our product enhances your security posture without forcing a costly infrastructure overhaul.
A True Security Partner
Choosing an MFA provider is a long-term commitment to a security partnership. We earn that trust through proven standards and expert support. Our ISO 27001 certification demonstrates our commitment to the highest international security protocols. When you need help, you get real support from our hands-on cybersecurity experts, not a generic call center. Experience the peace of mind that comes from working with a dedicated MFA partner.
Secure Your Organization with a Simply Strong MFA Partner
As we’ve explored, selecting the right multi factor authentication solutions requires a deep understanding of your unique infrastructure, from cloud to complex on-premises environments. A successful deployment hinges on evaluating not just the authentication methods, but the essential enterprise features that ensure both robust security and an intuitive experience for your entire organization. This balance of strength and simplicity is the cornerstone of effective cybersecurity.
LoginTC delivers this balance. As your ISO 27001 certified security partner, we provide expert on-premises and air-gapped MFA that you can trust. Unlike complex systems that take weeks to implement, our ‘Simply Strong’ approach is designed for rapid deployment-often in as little as one hour. We believe security should empower your business, not create friction.
Ready to secure your assets with confidence and gain true peace of mind? Start your free trial and deploy strong MFA in just one hour. Take the decisive step toward effortless, comprehensive security for your organization today.
Frequently Asked Questions About Multi-Factor Authentication Solutions
What is the main difference between 2FA and MFA solutions?
Two-Factor Authentication (2FA) is a specific type of Multi-Factor Authentication (MFA). The key difference is the number of required authentication factors. 2FA strictly requires two factors-typically your password and a second method like a code from your phone. MFA is a broader term that encompasses any authentication process requiring two or more factors. This could include a password, a fingerprint scan, and a physical security key, providing layered, robust security for your organization’s critical assets.
Is SMS-based multi-factor authentication still considered secure?
While SMS-based authentication is better than using only a password, it is no longer considered a highly secure method. It is vulnerable to sophisticated attacks like SIM swapping, where an attacker can intercept your text messages. For this reason, modern cybersecurity standards and compliance frameworks increasingly recommend stronger, more resilient methods. We advise using authenticator apps, push notifications, or hardware tokens to provide your business with the robust protection it deserves and achieve true peace of mind.
How long does it typically take to deploy an enterprise MFA solution?
Deployment time for an MFA solution can vary significantly. Many enterprise solutions involve complex integrations that can take days or even weeks, causing disruption to your operations. However, modern and streamlined multi factor authentication solutions are designed for rapid deployment. With the right platform and expert support, it is possible to fully protect your critical systems and onboard your users in as little as one hour, making strong security both simple and efficient for your team.
Can multi-factor authentication be used to protect legacy applications?
Absolutely. Protecting legacy applications that lack native MFA support is a common cybersecurity challenge, but it is entirely solvable. Effective MFA platforms provide connectors, RADIUS proxies, or agents that act as a bridge between the modern authentication service and your legacy systems. This allows you to extend strong, centralized security policies across your entire IT environment-from new cloud services to your most critical on-premises applications-without requiring any changes to the legacy application’s code.
Which type of MFA solution is best for meeting strict compliance regulations?
To meet strict compliance regulations like PCI DSS, HIPAA, or GDPR, you need an MFA solution that offers strong, auditable authentication methods. Phishing-resistant authenticators, such as FIDO2/WebAuthn-compliant hardware security keys, are often the gold standard. For organizations with data residency requirements, an on-premises solution provides complete control over your data and infrastructure. Choosing a flexible platform that supports these advanced methods ensures you can satisfy auditors and maintain a strong compliance posture.
How does an MFA solution protect against phishing attacks?
Phishing attacks succeed by tricking users into revealing their passwords. Even if an attacker steals your password, an MFA solution acts as a critical second line of defense. The attacker cannot complete the login because they do not possess the second factor-such as a one-time code from an app, a push notification approval, or a physical security key. This effectively neutralizes the compromised password, protecting your accounts and data from unauthorized access and giving you peace of mind.