How air-gapped MFA secures isolated networks
February 10, 2026 •

For organizations with critical infrastructure, cloud-based security is not an option. Your security policies demand complete network isolation, which creates a significant challenge: how do you enforce strong multi-factor authentication with zero internet connectivity? This is the precise challenge that a robust air-gapped mfa solution is designed to solve. It provides the strong, modern authentication your organization needs without ever requiring an external connection, giving you complete control over your security posture and peace of mind.
Security is hard, but it does not have to be complicated, even in the most secure environments. In this complete guide, we cut through the complexity. You will learn the real security risks facing your offline systems-from insider threats to physical media attacks. We will detail the technical requirements for an MFA solution that works entirely offline and show you how to find a reliable, easy-to-deploy system that meets stringent compliance mandates. Our business is protecting your business, and that starts with giving you the knowledge to secure your most valuable assets.
Key Takeaways
- Understand the fundamental difference between cloud-based MFA and authentication designed for completely isolated, offline networks.
- Learn the essential components of a true air-gapped MFA solution, centered around a self-contained on-premises authentication server.
- Identify critical use cases where offline authentication is non-negotiable for protecting your most sensitive assets and infrastructure.
- Gain a clear framework for evaluating and deploying an offline MFA solution that delivers robust security with streamlined administration.
Table of Contents
- What is Air-Gapped MFA and Why is it Critical?
- How Does MFA Work in a Fully Offline Environment?
- Key Requirements for an Air-Gapped MFA Solution
- Common Use Cases: Where is Air-Gapped MFA Deployed?
- Implementing Air-Gapped MFA with LoginTC
What is Air-Gapped MFA and Why is it Critical?
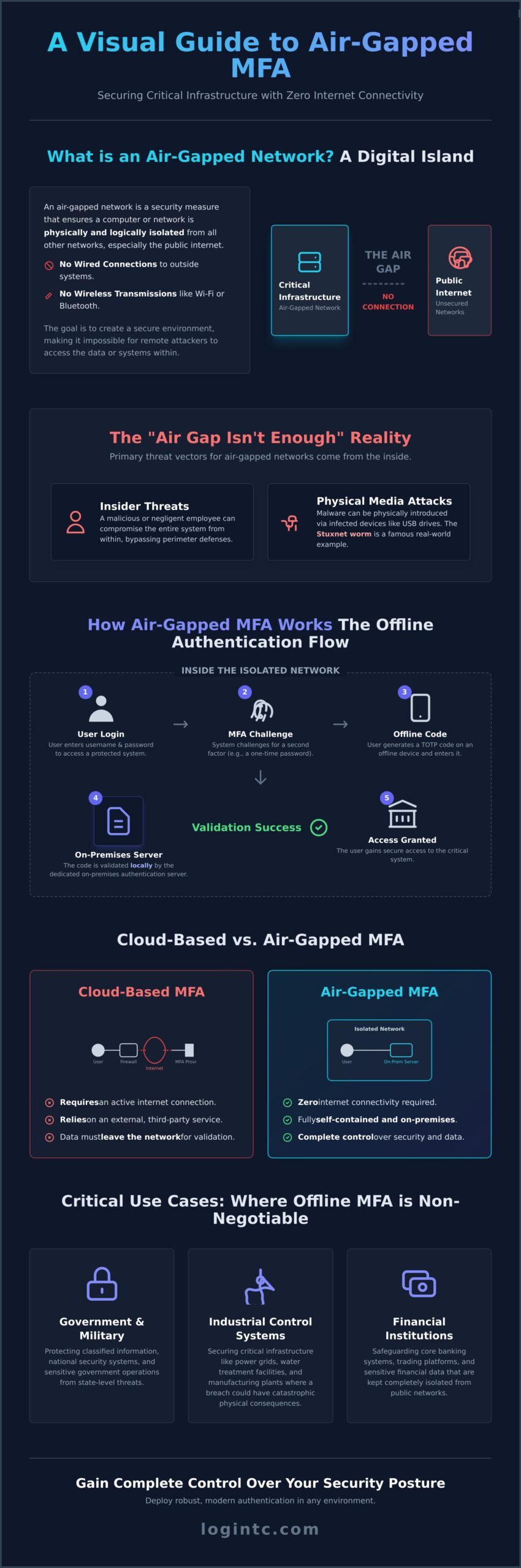
In the world of high-stakes cybersecurity, some assets are too critical to be exposed to the public internet. For these systems, organizations implement an air gap-a powerful security measure designed to create total isolation. But while physical separation is a strong foundation, it is not a complete security solution. This is where air-gapped MFA becomes an essential layer of defense, providing strong authentication in environments completely disconnected from the outside world.
Understanding the threats that can bypass physical isolation is the first step toward securing your most sensitive operations. Even the most secure perimeters require robust internal controls to verify user identity and prevent unauthorized access from within.
Defining the Air Gap: More Than Just ‘Offline’
An air-gapped network is a security measure that ensures a computer or network is physically and logically isolated from all other networks, particularly unsecured ones like the public internet. There are no wired connections to outside systems and no wireless transmissions like Wi-Fi or Bluetooth. The goal is to create a secure digital island, making it impossible for remote attackers to access the data or systems contained within it. This level of protection is standard in environments where a breach could have catastrophic consequences, including:
- Government and Military: Protecting classified information and national security systems.
- Industrial Control Systems (ICS): Securing critical infrastructure like power grids and water treatment facilities.
- Financial Institutions: Safeguarding core banking systems and sensitive financial data.
The ‘Air Gap Isn’t Enough’ Reality: Threats That Bypass Isolation
The common misconception is that an air gap equals total security. Unfortunately, determined adversaries have proven this false. The primary threat vectors for air-gapped networks don’t come from the internet; they come from the inside. Insider threats, whether from a malicious employee or a negligent one, can compromise the entire system. Furthermore, malware can be physically introduced, bypassing the air gap entirely.
The Stuxnet worm is a famous real-world example of this, where a malicious USB drive was used to introduce malware into an air-gapped Iranian nuclear facility. Once inside, an attacker with compromised credentials can still move laterally through the network, accessing critical systems. This is why simply having an air gap is not enough-you must also have strong controls to verify who is accessing what, which is the core function of an effective air-gapped MFA solution.
How Does MFA Work in a Fully Offline Environment?
Unlike cloud-based MFA that depends on a constant internet connection to an external provider, multi-factor authentication in a fully offline environment operates on a completely different principle: self-reliance. The entire authentication process is self-contained within your isolated network, ensuring that no data ever needs to cross the air gap to verify a user’s identity. This architecture provides the ultimate control and security for sensitive systems.
The typical user workflow is straightforward and secure. A user initiates a login with their username and password. The protected system then challenges them for a second factor. The user generates a one-time code from their offline authenticator-like a hardware token or an app on a company-issued device-and enters it. This code is validated internally, granting access without ever contacting an outside service. This is the core strength of a true air-gapped mfa solution.
The On-Premises Authentication Server: Your Private Security Hub
The heart of any offline MFA system is a dedicated, on-premises authentication server. This server acts as your private security hub, housed entirely within the air-gapped network. It manages all user identities, stores the “shared secrets” for generating codes, and enforces your organization’s unique security policies. When an authentication request occurs, this server handles the validation locally. This approach is the foundation of any robust on-premises multi-factor authentication strategy, guaranteeing that your security posture is never dependent on external factors.
Offline-Capable Authentication Methods
Only specific authentication methods are designed to function without an internet or cellular connection. These methods rely on pre-established secrets and algorithms that both the user’s device and the on-prem server understand. They adhere to established MFA implementation standards to ensure cryptographic strength and reliability.
- Time-Based One-Time Passwords (TOTP): Authenticator apps (like Google Authenticator or a dedicated enterprise app) use a shared secret and the current time to generate a temporary code that is valid for a short period, typically 30-60 seconds.
- Hardware Tokens: These are small, durable physical devices that generate codes based on OATH standards (Initiative for Open Authentication). They are purpose-built for offline security and are extremely resilient.
- Smart Cards/PIV/CAC: Common in government, defense, and critical infrastructure, these physical cards require a reader and contain a digital certificate that proves the user’s identity.
- FIDO2/WebAuthn (in most cases): It’s a common misconception that FIDO2 authentication requires a communication with a browser, and therefore cannot work online. However, LoginTC’s application of FIDO2 enables offline authentication with the phishing-resistant strength of WebAuthn technology. Learn more about LoginTC and FIDO2 authentication.
Methods That Do NOT Work Offline
It is crucial to understand which common MFA methods are incompatible with an air-gapped environment because they rely on external networks:
- Push Notifications: Require an active internet connection to send an approval request to a user’s smartphone.
- SMS and Voice Call Codes: Depend on public telephone and cellular networks to deliver codes.
Key Requirements for an Air-Gapped MFA Solution
Selecting the right multi-factor authentication for an isolated network is not a standard procurement process. High-security environments demand a solution built from the ground up for offline operation. When evaluating options, organizations must treat certain capabilities as non-negotiable to ensure security and manageability are never compromised. This checklist outlines the essential features for any true air-gapped MFA solution, providing peace of mind that your critical assets are protected.
Zero Internet Dependency
The fundamental requirement is absolute independence from the internet. The solution must perform all functions-including initial installation, administrator configuration, user enrollment, and daily authentication-without making a single external network call. It is crucial to verify that no “hidden” cloud components are required for licensing, updates, or feature activation, ensuring your network’s integrity remains intact.
Flexible Authentication Method Support
A one-size-fits-all approach to authentication is insufficient for secure facilities. Your chosen solution must support a range of proven offline methods to fit diverse operational needs and security policies. Look for comprehensive support for both soft and hard tokens, including:
- Time-Based One-Time Passwords (TOTP): Generated by mobile authenticator apps that work completely offline.
- Hardware Tokens: Support for physical authenticators like YubiKeys that generate secure one-time passcodes.
This flexibility gives you complete control over how users authenticate to sensitive systems.
Simplified Deployment and Management
Security should not create unnecessary complexity. Prioritize solutions that offer a streamlined, agentless deployment to minimize the administrative burden and potential attack surface on endpoints. A centralized, intuitive management console is essential for handling user administration, setting access policies, and overseeing the entire system from a single point of control, all from within your secure network.
Comprehensive Auditing and Reporting
In a high-security environment, visibility is paramount. A robust air-gapped MFA system must generate detailed, tamper-proof audit logs for all access events, including successful and failed authentication attempts. This capability is critical for forensic analysis and for demonstrating compliance with stringent regulatory standards. All reports must be generated and stored securely on-premises, with no reliance on external services.
Common Use Cases: Where is Air-Gapped MFA Deployed?
While not every organization requires network segmentation to this degree, for those that do, the security stakes are absolute. Air-gapped MFA is deployed in environments where a digital breach could have catastrophic real-world consequences. It provides an uncompromising layer of security for protecting your most critical digital and physical assets.
If your organization operates in one of the following sectors, you likely fit the profile for needing this level of advanced authentication.
Critical Infrastructure and Industrial Control Systems (ICS/SCADA)
Organizations managing power grids, water treatment facilities, and manufacturing plants operate in high-risk environments. A security breach isn’t just a data leak-it’s a potential public safety crisis. Strong, offline authentication is essential for protecting these systems.
- Prevent unauthorized access to sensitive Operational Technology (OT) networks.
- Secure Industrial Control Systems (ICS) and SCADA from remote and internal threats.
- Meet stringent regulatory standards like NERC CIP for the energy sector.
Government, Defense, and Intelligence
In the domains of government, defense, and intelligence, protecting classified information is a matter of national security. Air-gapped networks are standard practice for isolating the most sensitive data. This technology provides an essential security control for enforcing access policies within these isolated environments, securing classified networks and Sensitive Compartmented Information Facilities (SCIFs) by ensuring only highly-vetted personnel can authenticate.
Secure Research & Development (R&D) Labs
For businesses driven by innovation, intellectual property is their most valuable asset. Secure R&D labs use air-gapped environments to protect trade secrets, patented formulas, and proprietary designs from corporate espionage. By completely isolating experimental networks from the main corporate environment, these organizations ensure only authorized researchers can access sensitive data and systems, providing peace of mind that their competitive edge remains intact.
Across these diverse sectors, the common thread is the need for uncompromising security. The versatility of a robust MFA solution is demonstrated by its ability to provide strong, reliable authentication where it matters most. For organizations that cannot afford any margin of error, air-gapped mfa provides the necessary layer of protection and control.
Implementing Air-Gapped MFA with LoginTC
Understanding the principles of air-gapped security is one thing; implementing it without complexity is another. LoginTC was built to bridge that gap, providing a solution that is both incredibly secure and remarkably simple to manage. Our ‘Simply Strong’ philosophy means you get the robust protection your critical infrastructure demands, without the administrative overhead that slows your organization down.
True On-Premises Architecture, Built for Isolation
For a solution to be truly air-gapped, it cannot have any reliance on external services. LoginTC’s on-premises connector is purpose-built for this reality. It operates entirely within your network perimeter, ensuring that every part of the authentication process is self-contained. This design provides a genuine air-gapped mfa solution, giving you complete control and peace of mind.
- All user data and authentication logs remain on your servers, under your control.
- The system functions perfectly with zero internet connectivity.
- You achieve total data sovereignty, a critical requirement for high-security environments.
Effortless Administration and Rapid Deployment
Cybersecurity is hard, but managing it shouldn’t be. Unlike complex solutions that take days or weeks to deploy, LoginTC can be implemented in as little as one hour. We believe administrators are users too, which is why we designed a single, intuitive interface for managing users, policies, and authenticators. This streamlined experience reduces human error and frees up your IT team to focus on other critical tasks.
Secure Your Most Critical Assets Today
LoginTC delivers flexible, offline authentication methods to protect your most valuable assets. Our comprehensive platform secures everything from privileged access workstations and server rooms to mission-critical systems that must remain isolated.
- Windows Logon & RDP: Secure local and remote logins to servers and endpoints.
- VPNs & Network Devices: Add a critical layer of security to your network access points.
- Legacy Applications: Extend modern MFA to older systems without native support.
Stop compromising between security and usability. Discover how easy it is to implement a true air-gapped mfa strategy. Start your free trial to see how it works.
Secure Your Isolated Networks with Confidence
In today’s complex threat landscape, relying on physical isolation alone is no longer a sufficient defense for your critical infrastructure. As we’ve covered, implementing multi-factor authentication is not only possible but absolutely essential in offline environments. It provides a vital, verifiable layer of security where it’s needed most. A modern air-gapped mfa solution demystifies this process, transforming what seems like a complex security challenge into a straightforward and achievable goal for any organization.
LoginTC is purpose-built to meet these high-stakes demands. Our on-premises MFA platform delivers security you can trust, featuring an agentless architecture that simplifies management and a rapid 1-hour deployment for immediate protection. As an ISO 27001 Certified provider, we are committed to providing the peace of mind that comes from robust, reliable security. Don’t leave your most sensitive systems vulnerable. Take control of your offline security posture with a solution that is both simply strong and effortlessly effective.
Discover LoginTC’s On-Premises MFA for Air-Gapped Environments and protect your critical infrastructure today.
Frequently Asked Questions About Air-Gapped MFA
Can I use a smartphone app for MFA in an air-gapped network?
Typically, no. The use of a smartphone with active Wi-Fi or cellular capabilities would violate the core principle of an air-gapped network, which is complete isolation. True air-gapped authentication relies on dedicated hardware tokens that possess no network connectivity. These devices generate one-time passcodes (OTPs) that are manually entered by the user, ensuring the entire authentication process remains secure and completely offline from any external network threats.
Does an air-gapped MFA solution require installing software on every computer?
Not necessarily on every endpoint. The core authentication server software is installed on a dedicated machine within your secure, offline network. User workstations, however, often do not require any special client-side software. Users simply enter the OTP from their hardware token into the standard login prompt protected by the MFA solution. This streamlined approach simplifies deployment and management, reducing the administrative burden on your IT team and creating an effortless user experience.
How does user enrollment work in a completely offline system?
User enrollment is a secure, administrator-managed process conducted entirely within the offline environment. An administrator uses the on-premises management console to import a token’s unique seed file and associate that specific hardware token with a user’s account. The physical token is then securely delivered to the end-user. This controlled, hands-on procedure ensures that only authorized individuals are enrolled, maintaining the high-security integrity required in an air-gapped system.
What kind of hardware tokens are supported by solutions like LoginTC?
A flexible on-premises solution should support a wide range of industry-standard hardware tokens. This includes OATH-compliant authenticators such as YubiKeys (in OTP mode) and other common TOTP (time-based) or HOTP (counter-based) hardware tokens. Supporting multiple types gives your organization the freedom to use existing hardware or select the form factor-from key fobs to credit card styles-that best fits your security policies and user requirements.
Is air-gapped MFA compliant with regulations like CMMC, HIPAA, or NERC CIP?
Yes, implementing a robust air-gapped MFA solution is a foundational component for meeting the stringent access control requirements of many regulations. Standards like CMMC, NERC CIP, and HIPAA mandate strong, multi-factor authentication to protect critical systems and sensitive data. By isolating the authentication process from external networks, this method directly addresses mandates for network segmentation and strong identity verification, simplifying your path to achieving and maintaining compliance.
How does licensing for air-gapped MFA typically work?
Licensing is designed to be straightforward and predictable. Most on-premises solutions, including LoginTC, are licensed on a simple per-user, per-year basis. This model allows your costs to scale directly with your organization’s size without complex calculations or hidden fees. Your license includes the software, ongoing updates, and access to expert technical support, ensuring your air-gapped MFA deployment remains secure, current, and fully supported throughout its lifecycle.