Cyphercor named Top 20 Most Promising CA Technology Providers
April 29, 2015 •
Cyphercor is excited to announce that CIOReview has named us one of the Top 20 Most Promising CA Technology Providers in recognition of our award-winning two-factor authentication (2FA) solution LoginTC.
We are so pleased to have been honoured for our ability to enhance customers’ CA SiteMinder (more recently known as CA Single Sign-On) identity access management deployments by seamlessly integrating a strong second layer of protection with minimal effort and cost.
You can learn more about CIO’s selection process and find out the reasoning behind why they decided to grant us this distinction in this press release. In addition to the top 20 distinction, CIO has also published a full-page spread about Cyphercor on page 16 of the CA Technologies April 24, 2015 issue. The top 20 list can be found on pages 14-15. The issue is available here.
The LoginTC SiteMinder Connector is essentially a SiteMinder authentication scheme which you can download as a zip file, install on your SiteMinder Policy Server and then make available for any of your SiteMinder realms. It maintains all of LoginTC’s key unique characteristics:
- Available for iOS, Android and BlackBerry devices as well as all PCs capable of running Google Chrome
- Setup takes less than an hour
- Incorporates dynamic, real-time contextual information alongside access requests
- No Personally Identifiable Information (PII) or supplementary hardware required
- Push notifications (No SMS or OTPs!) for secure access that works worldwide
- User friendly and highly adoptable interface and overall system
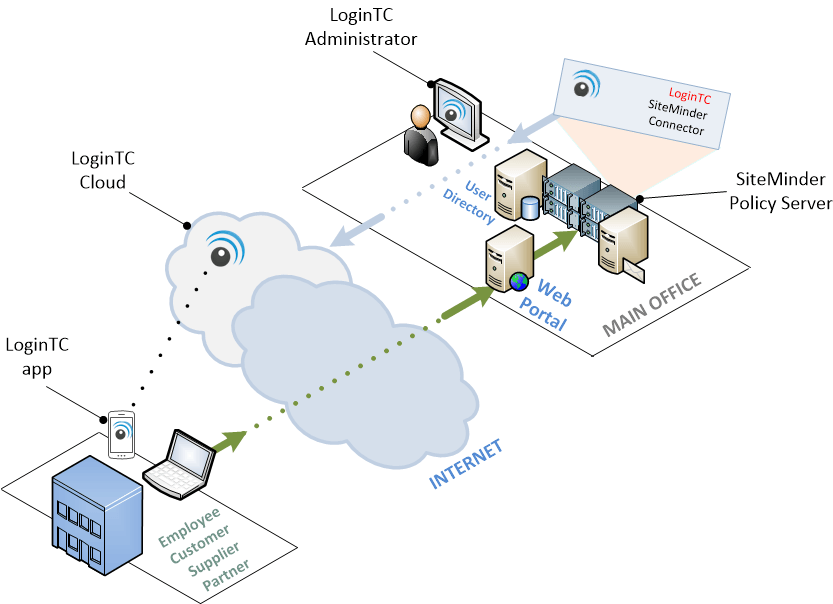
The diagram below depicts a typical enterprise deployment of the LoginTC SiteMinder Connector. The SiteMinder administrator installs the connector and selects its authentication scheme on those resources that require LoginTC 2-factor authentication. The connector can co-exist with the existing authentication schemes already in use by the enterprise.
Step-by-step instructions can be found on our detailed custom documentation page here.