6 Must-Have MFA Features
May 02, 2023 •

As cyber attacks become more sophisticated, organizations are turning to multi-factor authentication (MFA) as a way to secure their systems and data. MFA adds an extra layer of security by requiring users to provide two or more factors of authentication before granting access.
However, not all MFA solutions are created equal. To ensure that your organization is fully protected, it’s important to choose an MFA solution with the right features.
In this blog post, we’ll discuss the six must-have features for your MFA solution, so you can make an informed decision and keep your organization’s data safe.
Authentication Logs
As an IT administrator, having insights into important security-related actions taken by your end-users is critical.
That’s why you should look for a multi-factor solution that offers detailed authentication logs. With authentication logs, you can track suspicious activity, better respond to help desk questions, and use the data to implement better authentication policies.
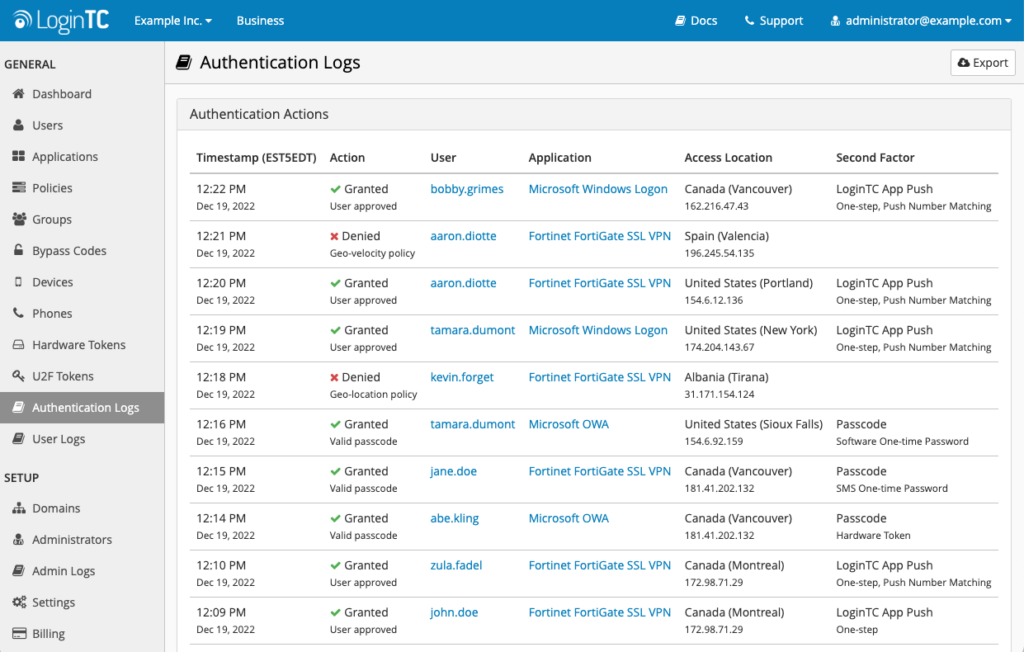
For example, if you receive a help desk call from a user who wasn’t able to authenticate, you can quickly check the logs for that user and confirm what went wrong with the request. This helps you more efficiently direct the user on how to fix the issue, and avoid it going forward.
Alternatively, you could institute a best practice of exporting and analyzing your authentication logs once a week in order to scan for unusual activity or unauthorized access attempts.
Push Number Matching
Maintaining a balance between security and usability is one of the most important aspects of a good MFA solution. You want to ensure that your users won’t struggle to use the solution, and also feel confident that it’s fully protecting them from malicious attacks.
The Cybersecurity and Infrastructure Security Agency (CISA) recommends that one of the best ways to do this is to introduce what’s known as number matching.
Number matching is a way to introduce an additional layer of security to one of the most common forms of user-friendly authentication, push notifications.
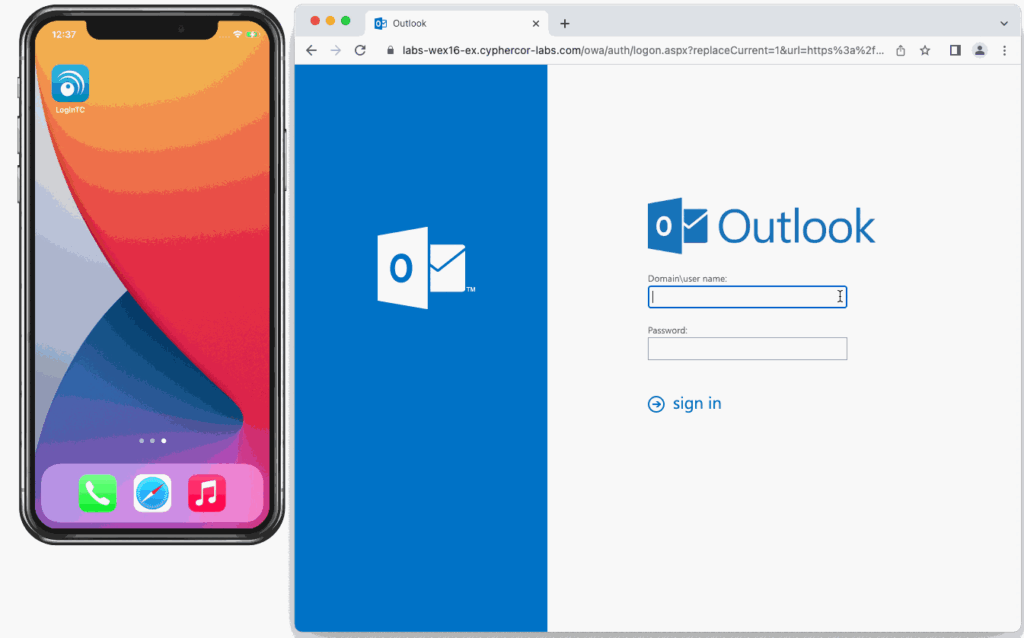
To accept a push notification request, users must first match the number on the request with the corresponding number on their authentication device.
This feature ensures that if a malicious attacker tries to send a push notification hoping that it’ll be automatically accepted by the user they’re trying to phish, the end-user will realize that they don’t have a number to match the request to. With proper employee training, they’ll be able to recognize this request as a phishing attempt, reject it, and report it to their administrator.
User Alias
As an administrator, sometimes you need to be able to run multiple accounts to test functionality. That’s why you should always look for a user alias feature with your MFA solution.
With user aliases, you won’t get penalized for additional license usage, and your administrator, standard user, and other test accounts can all be accessed through the same account.
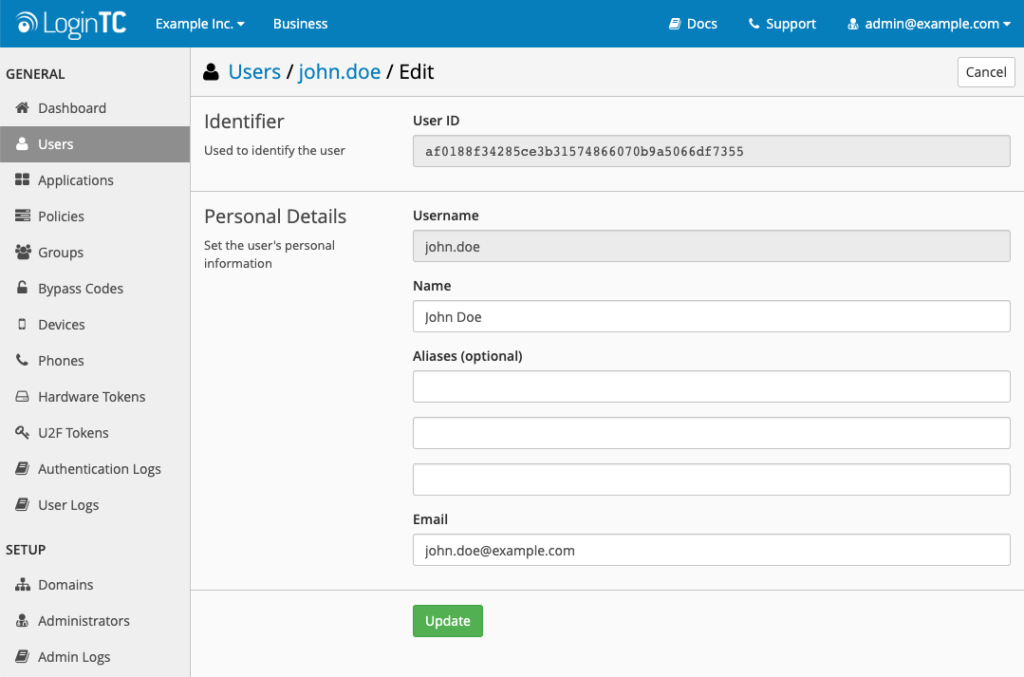
A user alias feature is also great for accommodating legacy systems. When more than one system is in use, and users have multiple standard usernames, you can add both to reduce confusion without incurring additional licensing costs.
Enrollment Link
As an IT administrator, you know that enrolling your end-users in software solutions can be a time-consuming task. This problem can become compounded when dealing with physical devices while working remotely.
That’s why you should look for an MFA solution that offers guided user self-enrollment.
A user enrollment portal allows you to set the parameters for what end-users are allowed to do, but leave the enrollment steps in their hands. This process helps users become more familiar with the security tools they’ll use every day, and frees up your time to work on more critical tasks.
User Sync Tool
Another must-have MFA tool that will save you time is user synchronization.
Instead of manually importing dozens or hundreds of end-users into your MFA solution, simply connect your LDAP-speaking user directory, such as Active Directory. With user synchronization, user details such as names, email addresses, phone numbers, and group information can be uploaded automatically.
If a user’s information changes, you only have to update your user directory and the tool will automatically make the changes in your MFA solution as well. This ensures that your critical security solutions are able to seamlessly maintain an error-free user list.
Remembered Devices
While security best practices mean that you should ask for a second factor of authentication every time you login, there are times in which it’s acceptable to allow users to stay authenticated. Finding a balance between security and usability is crucial for getting widespread adoption and reducing the impact on your help desk.
That’s why you should consider an MFA solution that supports remembered devices.
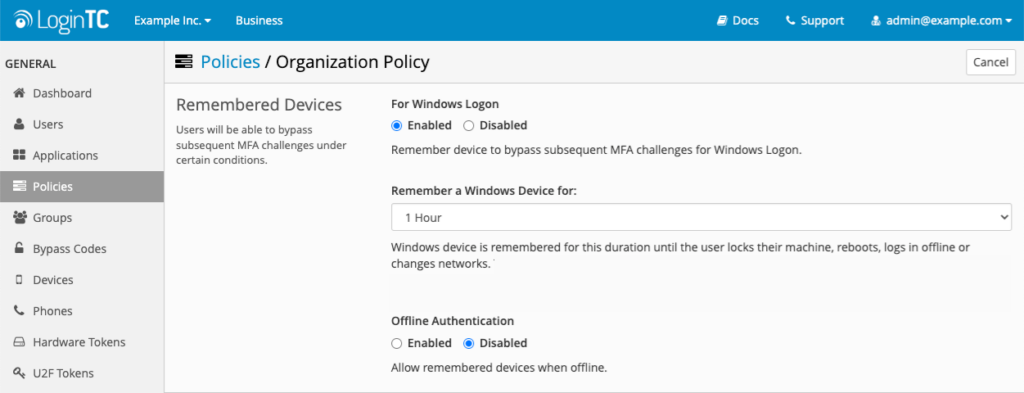
This reduces the amount of times an end-user must authenticate with second-factor credentials, so long as the device remains on the same network and hasn’t been logged out or rebooted.
As an IT administrator, this allows you to set your own authentication limits and make the process of authentication more user-friendly.
Conclusion
Whatever your reasons for needing MFA, bridging usability and security should be top of mind. When evaluating an MFA solution, you should ask about these six features.
If you’re looking for more information about user friendly multi-factor authentication, reach out to us today.