Top 3 reasons to avoid SMS when choosing a 2-factor authentication provider
May 15, 2015 •
Let’s face it. The majority of smartphone-based two-factor authentication (2FA) providers today use SMS to deliver second factor codes or one-time passwords to users. Here’s why they shouldn’t:

1. SMS networks are not necessarily trustworthy.
The point of 2FA is to protect data. Which means that not only must the data be kept secure, but also all elements of the process flow being used to protect said data. Therefore, codes or one-time passwords (OTPs) that users use to “unlock” access to online accounts must travel through secure channels to get to them. Do mobile network operators run secure networks? Maybe. It’s hard to say. Especially with so many to account for, particularly when roaming. But, unfortunately, encryption used on cellular networks is known to be weak.
2. SMS can be stolen, copied onto another devices and still work.
Mobile malware (viruses) injected into cell phones can intercept SMS messages, putting their contents directly into the hands of an attacker. The attacker can then use that information to break into your accounts and steal your digital assets — even when SMS-based 2FA is enabled.
3. SMS requires cell phone service to work.
Remote work is becoming increasingly popular — and for good reason — but SMS-based 2FA adds a barrier to the experience by not working when a user has no cell service. What would happen if you wanted to access corporate resources, such as an office VPN, while away on a business trip? You would be forced to “roam” onto the untrustworthy cell networks mentioned earlier and face major fees as a result.
The solution?
There is a better way! (1) LoginTC uses Secure Remote Password protocol in its 2FA system and other methods including certificate-protected push notifications and SSL tunnels to ensure that all channels through which data passes are extremely secure. (2) LoginTC involves no SMS or OTPs and instead turns the smartphone (or desktop) itself into a second-factor credential, meaning that unless the user has a specific device on hand, they cannot access the protected account. (3) LoginTC works anywhere wireless internet can be found (i.e. worldwide) eliminating any reliance on cellular service and charges incurred for it. For more information: /get-started/.
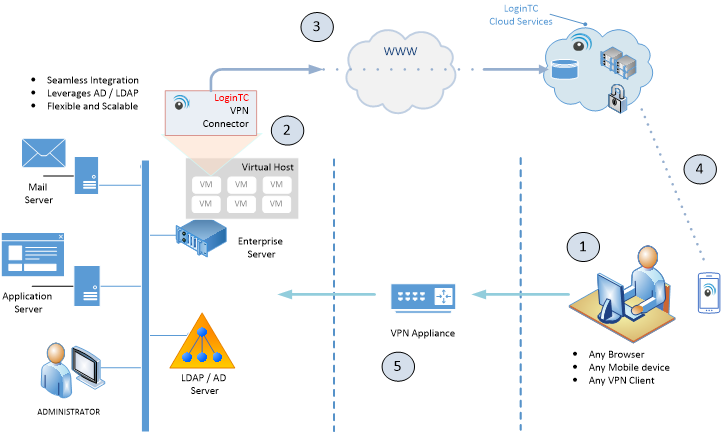
- User attempts to establish a secure VPN session with a browser or VPN client app.
- The VPN appliance prompts the user to enter first-factor credentials (username/password) while the LoginTC VPN Connector receives a request for LoginTC 2FA.
- The LoginTC VPN Connector requests confirmation of second factor credentials to LoginTC Cloud Services.
- LoginTC Cloud Services notifies user’s LoginTC mobile app (or Chrome app) via SRP protocol and prompts for LoginTC credential.
- User successfully accesses internal applications remotely.