How to add on-prem MFA to Windows Server
November 18, 2025 •

Windows Server powers much of the world’s business infrastructure. Whether it’s managing users, data, and network access behind the scenes, these services are essential. But because these systems often handle administrative logins and remote access, they’re frequent targets for attackers. Multi-factor authentication (MFA) for Windows dramatically reduces that risk.
The challenge for many IT teams isn’t why to use MFA but how to deploy it effectively in an on-prem or hybrid Windows environment. This post explores both Microsoft’s native MFA integration and alternative methods for organizations that prefer a simpler, more flexible, or on-prem setup.
Let’s dive in!
Understanding on-prem MFA
Multi-factor authentication (MFA) is a security measure that requires users to provide two or more verification factors to gain access to a resource such as a Microsoft Server. Rather than just asking for a username and password, MFA requires additional verification through multiple “identity factors” which include:
- Something the user knows (knowledge factor),
- Something the user has (possession factor), or
- Something the user is (inherence factor).
In the context of Windows Server, implementing MFA on your premises can protect administrative logins, remote desktop sessions, and other critical access points. By requiring multiple forms of verification, organizations can better safeguard their infrastructure against unauthorized access, data breaches, and other cyber threats.
On-Prem MFA for Windows Server: A scenario
Picture a mid-sized company with several Windows Servers running Active Directory, file sharing, and Remote Desktop Gateway for remote staff.
Passwords alone protect all these entry points, and that’s starting to feel risky. Attack attempts against RDP are up, VPN credentials can be leaked, and shared admin passwords are hard to manage securely.
You and your IT team know you need MFA, but don’t have the time or budget to overhaul everything with new Microsoft Entra licenses or reconfigure cloud authentication. You need something that fits their existing infrastructure, not something that replaces it.
Some companies choose to go the Network Policy Server (NPS) route for Entra MFA, but there are some major limitations of this route.
Drawbacks to Microsoft NPS extension for Entra MFA
Network Policy Server (NPS) for Entra MFA can add a second factor login to VPNs and RD Gateway, but its capabilities are mainly limited to organizations with expensive Microsoft accounts and cloud-only deployments.
It’s not ideal for air-gapped or isolated networks, where organizations require on-premises software. There are also a limited number of authentication methods, which rarely work for all users.
For teams that rely mostly on on-prem infrastructure, a third-party MFA system can offer more control and flexibility.
Solution: Third-party MFA for on-prem Windows Server
Third-party MFA tools give organizations a way to secure Windows Server access without committing to Microsoft’s cloud ecosystem. These solutions integrate with Active Directory using standard authentication protocols, usually RADIUS or LDAP, so you can layer MFA onto VPN, RD Gateway, and other remote access points with minimal disruption.
LoginTC fits this model and offers two deployment paths:
LoginTC Cloud: This is the hosted version, ideal for teams that want to manage MFA centrally without maintaining extra infrastructure. It supports push notifications, TOTP, and hardware tokens, and works smoothly for most external-facing services like VPNs. Many organizations use this for simplicity, especially if they already rely on cloud services.
LoginTC Managed (On-Prem): For environments with stricter security requirements, hybrid infrastructure, or limited tolerance for cloud dependencies, LoginTC Managed provides a completely on-premises option. It’s designed for organizations that run Windows Server locally, maintain private networks, or operate systems that cannot rely on external connectivity.
With LoginTC Managed, the Windows Connector runs entirely inside your environment, authenticates directly against Active Directory, and delivers MFA without sending authentication traffic through the cloud. This makes it a strong fit for:
- Air-gapped or isolated networks
- Privileged access paths (like RD Gateway)
- Compliance-driven deployments
- Hybrid AD environments with limited cloud integration
- VPNs and firewalls that require local-only authentication
Regardless of which version is used, the flow looks the same from a user’s perspective:
- The user enters their Windows credentials.
- Active Directory verifies them.
- LoginTC triggers a second factor (push, TOTP, or token).
- Access is approved only after the MFA challenge succeeds.
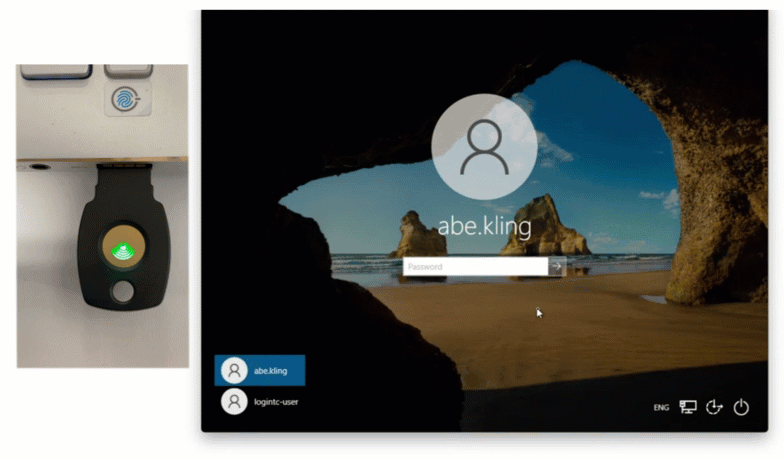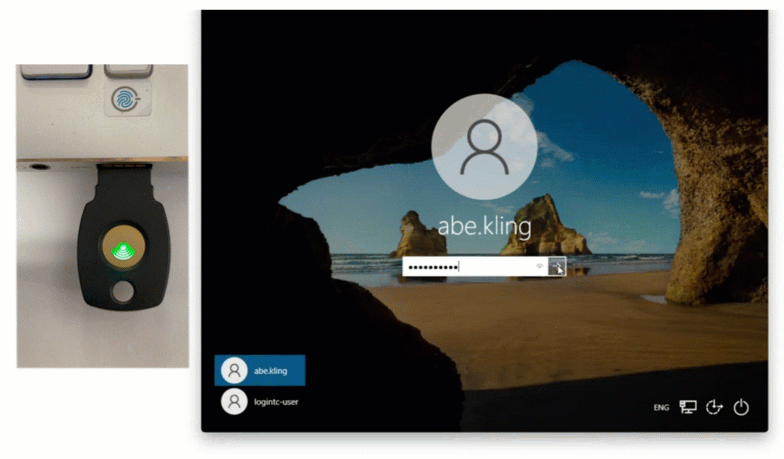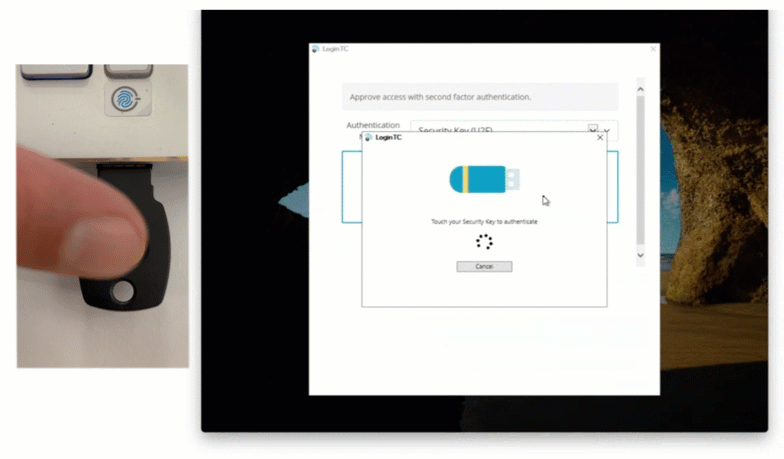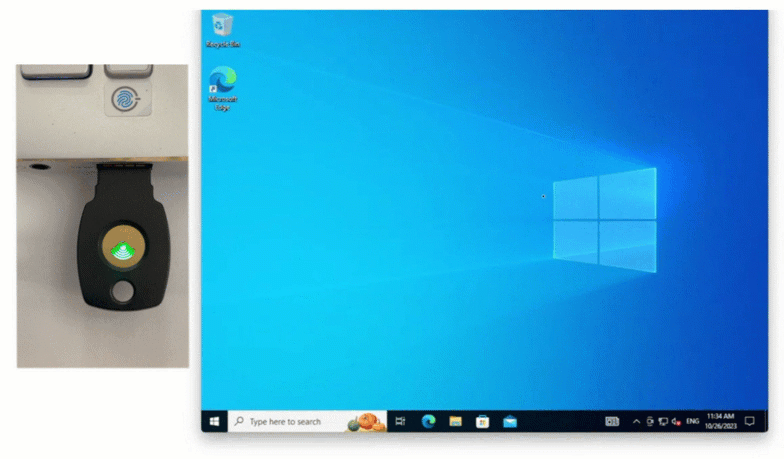
For Windows Server environments that want tighter control, reduced external dependencies, and simple drop-in deployment, LoginTC Managed is typically the best fit.
LoginTC is compatible both domain joined and local accounts, and with the following versions of Windows Server:
- Windows Server 2012 R2
- Windows Server 2016
- Windows Server 2019
- Windows Server 2022
- Windows Server 2025
The key advantage with LoginTC is flexibility: you can apply MFA exactly where it’s needed, on your timeline, while maintaining compatibility with existing authentication flows.
Rolling out on-prem MFA for Windows Server
Returning to our earlier example, the IT team decides to deploy an on-prem MFA connector rather than reworking their infrastructure for cloud MFA.
Want to see a set-up in action? Book a demo to see how to connect LoginTC Managed on-premises MFA to Windows Server.
The installation process is simple, and looks something like this:
1. Set the scope and prepare
They start by identifying which systems and applications are being used with the Windows Server and authenticate against Active Directory: for example, a VPN, RD Gateway, and a few admin workstations. Next, they create a small pilot group of users and one test environment to validate everything before going live.
2. Deploy a connector for MFA
They spin up a lightweight Windows Server VM to host the LoginTC Windows Logon Connector, an on-prem component that bridges their authentication flow. It connects to their Active Directory for the first-factor (username and password), then handles the second factor via LoginTC using a push notification, TOTP passcode, or hardware token.
The connector runs entirely on their own network, meaning no internet dependency or cloud routing is required for internal systems.
3. Integrate with Windows services
Next, they configure their Windows server to use the connector, so that every login request now passes through the connector, which verifies credentials and triggers the MFA challenge.
If users approve the login on their phone, access is granted immediately. If they deny it or ignore it, then the session never starts.
4. Test and expand
After verifying the pilot group’s logins and confirming that fallback accounts work correctly, the team gradually expands coverage to all remote users. The entire rollout takes a few days, and most users adapt without extra training since the login process feels familiar.
5. Strengthen and monitor
Once MFA is enforced for all remote access points, the IT team sets up basic monitoring to ensure availability and logs authentication attempts for auditing. From there, they plan to protect other services like VPN admin portals and shared infrastructure in the same way.
In less than a week, the organization moves from relying on passwords alone to having a modern, phishing-resistant MFA layer protecting every remote Windows Server login. And because they chose a flexible on-prem approach, they maintain full control without needing to change how their users sign in or buy additional Microsoft licenses.
Next steps
Adding MFA to Windows Server isn’t limited to Microsoft’s cloud ecosystem. Whether you run a fully on-prem network, a hybrid setup, or isolated systems that can’t rely on internet access, there are practical ways to protect your environment.
Third-party MFA solutions such as LoginTC make it easier to close common attack vectors like RDP and VPN access, without major architectural changes.
If you’re exploring ways to add MFA to on-prem Windows Servers or RD Gateways, book a demo to learn more about LoginTC’s Windows Logon Connector and on-prem deployment options.
Continue reading for a deeper dive about on-prem MFA and Windows Server.
What is Windows Server?
Windows Server powers much of the world’s business infrastructure whether that’s managing users, data, and network access behind the scenes. But because these systems often handle administrative logins and remote access, they’re frequent targets for attackers.
Multi-factor authentication (MFA) dramatically reduces that risk. The challenge for many IT teams isn’t why to use MFA, it’s how to deploy it effectively in an on-prem or hybrid Windows environment.
Benefits of on-prem MFA for Windows Server
Deploying MFA on-premises for Windows Server offers several notable benefits. First and foremost, it provides greater control over the security infrastructure. Organizations can customize and manage their MFA solution to meet specific security policies and compliance requirements without relying on external cloud providers. This autonomy is particularly important for businesses with stringent data protection mandates or those that operate in highly regulated industries.
Another advantage is the reduced dependency on internet connectivity. On-prem MFA solutions do not require continuous internet access, which is beneficial for organizations operating in areas with unreliable or limited connectivity. This ensures that users can still authenticate and access critical systems even during network outages or connectivity issues, thereby maintaining business continuity.
Additionally, on-prem MFA solutions offer enhanced data privacy. With an on-prem setup, all authentication data remains within the organization’s network, reducing the risk of data exposure to third parties. This is particularly appealing for organizations concerned about data sovereignty and the potential vulnerabilities associated with transmitting sensitive information over the internet.
Prerequisites for implementing on-prem MFA
Before implementing on-prem MFA on Windows Server, several prerequisites must be met to ensure a smooth deployment process. Firstly, it is crucial to have a comprehensive understanding of your organization’s existing infrastructure, including the network topology, server configurations, and user access patterns. This knowledge will help in designing an MFA solution that integrates seamlessly with the current environment.
Next, ensure that your Windows Server environment is up to date with the latest patches and updates. Running outdated software can expose vulnerabilities that could be exploited during the MFA implementation process. Additionally, verify that all necessary hardware and software components required for the MFA solution are available and compatible with your existing systems.
It is also important to identify the specific authentication factors that will be used in the MFA solution. This could include hardware tokens, mobile apps, biometrics, or other verification methods. Each factor should be evaluated for its security, usability, and compatibility with the organization’s user base. Providing clear instructions and training to end-users on how to use the new MFA system will further facilitate a successful implementation.
Configuring MFA settings for your environment
Once the initial installation is complete, configuring the MFA settings to suit your specific environment is crucial. Start by defining the authentication methods that will be used. This could include OTP (one-time passwords) sent via SMS or email, mobile authenticator apps, hardware tokens, or biometrics. Each method should be selected based on security requirements, user convenience, and organizational policies.
Next, configure the user and group policies to determine who will be required to use MFA and under what conditions. For instance, you might enforce MFA for administrative accounts, remote access users, or specific user groups that handle sensitive data. Ensure that the policies are clearly communicated to all users to avoid confusion and ensure compliance.
Additionally, configure any integration settings with other systems and applications. This might include integrating MFA with your existing identity management systems, single sign-on (SSO) solutions, or other security tools. Proper integration ensures that MFA is seamlessly incorporated into the overall security framework, providing a unified and robust defense against unauthorized access.
Testing your on-prem MFA setup
Thorough testing is a critical step in the MFA implementation process. Begin by conducting functionality tests to ensure that the MFA solution is working as expected. This includes verifying that users can successfully authenticate using the specified methods and that the authentication process is smooth and efficient. Test different scenarios, such as login attempts from various locations, devices, and network conditions, to ensure consistent performance.
Next, perform security testing to identify any potential vulnerabilities or weaknesses in the MFA setup. This might involve conducting penetration tests, simulating phishing attacks, or other security assessments to evaluate the strength of the MFA system. Address any identified issues promptly to enhance the overall security posture.
Finally, gather feedback from end-users to understand their experience with the new MFA system. Solicit input on the usability, convenience, and any challenges they encountered during the authentication process. Use this feedback to make necessary adjustments and improvements, ensuring that the MFA solution is not only secure but also user-friendly.
Troubleshooting common MFA issues
Despite careful planning and implementation, issues can still arise with MFA systems. One common problem is user enrollment difficulties. Users may experience challenges when enrolling their devices or completing the initial setup process. Ensure that clear instructions and support resources are available to assist users in successfully enrolling and using the MFA system.
Another issue is authentication failures. Users may encounter errors when attempting to authenticate, which could be due to network issues, incorrect configurations, or compatibility problems with their devices. Troubleshoot these issues by reviewing the system logs, verifying configuration settings, and testing the affected devices and network connections.
Additionally, users may report inconvenience or frustration with the MFA process, particularly if it is perceived as cumbersome or time-consuming. Address these concerns by optimizing the user experience, such as by streamlining the authentication steps, offering multiple verification options, and providing training and support to help users adapt to the new system.
Best practices for maintaining on-prem MFA
Maintaining an effective MFA system requires ongoing attention and management. Regularly review and update your MFA policies to ensure they align with evolving security threats and organizational needs. This might involve adjusting the authentication methods, updating user and group policies, or integrating new security technologies.
Conduct periodic security assessments and audits to evaluate the effectiveness of the MFA system. This includes reviewing system logs, monitoring for suspicious activity, and performing penetration tests to identify potential vulnerabilities. Use the findings from these assessments to make necessary improvements and strengthen the overall security posture.
Additionally, stay informed about the latest developments and best practices in MFA technology. This includes keeping up with industry standards, attending relevant conferences and training sessions, and participating in professional networks and forums. By staying current with the latest trends and advancements, you can ensure that your MFA system remains robust and effective.
Comparing on-prem MFA solutions vs. cloud-based MFA
When selecting an MFA solution, organizations must consider the pros and cons of on-premises versus cloud-based deployments. On-prem MFA solutions offer greater control and customization, as organizations can manage the entire authentication process within their own infrastructure. This is particularly beneficial for businesses with specific security or compliance requirements that necessitate complete control over their data and systems.
On the other hand, cloud-based MFA solutions offer the advantage of scalability and ease of deployment. These solutions are typically managed by third-party providers, which means that organizations do not need to invest in additional hardware or IT resources. Cloud-based MFA can be quickly deployed and scaled to meet the needs of growing businesses, making it an attractive option for organizations with limited IT capabilities.
However, cloud-based MFA solutions may raise concerns about data privacy and security. Storing authentication data in the cloud can expose organizations to potential risks, such as data breaches or service outages. Organizations must carefully evaluate the security measures and compliance standards of their chosen cloud provider to ensure that their data is adequately protected.
Conclusion and future considerations for MFA security
Implementing on-prem MFA on Windows Server is a critical step in enhancing the security of your organization’s infrastructure. By requiring multiple forms of verification, MFA significantly reduces the risk of unauthorized access, data breaches, and other cyber threats. Whether you choose an on-prem or cloud-based solution, the key is to carefully plan, deploy, and maintain your MFA system to ensure its effectiveness and reliability.
Looking ahead, the future of MFA security will likely involve continued advancements in authentication technologies, such as biometrics, behavioral analytics, and AI-driven security measures. These innovations will further enhance the robustness and usability of MFA systems, making them even more effective in protecting against evolving cyber threats.
As organizations continue to navigate the complex landscape of cybersecurity, staying informed about the latest trends and best practices in MFA will be essential. By proactively adopting and adapting to new technologies, businesses can ensure that their authentication systems remain secure, resilient, and capable of defending against the ever-changing threat landscape.