How to use FIDO2 Smart Card Authentication with Windows
September 12, 2025 •

Smart card authentication is familiar in the physical world, as many employees use them to unlock office doors every day. Digitally, they serve a similar purpose: verifying a user’s identity when logging into applications and services.
Traditionally, smart cards have relied on certificate-based authentication. While secure, this approach is complex and resource-intensive, limiting its use to governments and large enterprises with the right infrastructure.
Recently, however, smart cards have evolved. Some now come with FIDO2 support built in, making them easier to deploy and enabling phishing-resistant authentication. This opens up smart card authentication to a wider range of organizations, from small businesses to enterprises already using cards for building access.
In this post, we’ll look at how smart card authentication works, what FIDO2 adds, and the world-first innovation that’s enabled FIDO2 Smart Cards to be used with not just with web-based applications, but also with Windows Logins.
What is Smart Card Authentication?
Smart Card Authentication is a multi-factor authentication (MFA) method that allows end users to tap or insert a smart card to authenticate into VPNs, firewalls, web applications, and now Windows logins and Remote Desktop applications.
Smart Cards allow for both physical and digital identity verification, making them extremely versatile and efficient.
Historically, Smart Cards use certificate-based authentication in order to secure logins. This method is used largely in enterprise organizations, which can allocate resources to handle the heavy overhead that certificate authentication requires to manage.
However, in recent years some companies have begun making Smart Cards with FIDO2 authentication built in alongside certificates. These cards utilize the FIDO2 protocol to enable phishing-resistant authentication without using a traditional “Yubikey” style security key token.
What is FIDO2 Authentication?
FIDO2 authentication is a public-private cryptographic authentication method that utilizes the WebAuth standard and CTAP2 protocol to securely authenticate users.
Traditionally, FIDO2 has been implemented in two main ways. Firstly, in the form of roaming authenticators, like USB-based security keys, which allow users to carry hardware to confirm their digital identity. Secondly, as platform authenticators built into devices like phones and computers.
The introduction of FIDO2 authentication into Smart Cards opens up unique possibilities for organizations in a few different use cases.
Firstly, smaller organizations that don’t have the resources to manage the complexity of certificate-based authentication can now take advantage of all the benefits of Smart Card authentication, including bridging the physical/digital identity gap. This innovation makes Smart Card authentication a viable and worthwhile investment for a wider range of organizations.
Secondly, organizations that already use Smart Cards for physical access verification can now add additional use cases to those cards, provided they are FIDO2 enabled. This can be a cost-saving measure for many organizations, as they can now use existing identity infrastructure to secure digital assets with phishing-resistant technology.
The latest innovation from LoginTC enables FIDO2 Smart Card Authentication not just for web applications, VPNs, and Firewalls, but also for Windows logins, including Remote Access, Console, and Offline. This innovation is a first for the authentication and identity management industry, and represents a pioneering achievement years in the making.
Let’s take a look at how it works below.
FIDO2 Smart Card: Tap to authenticate
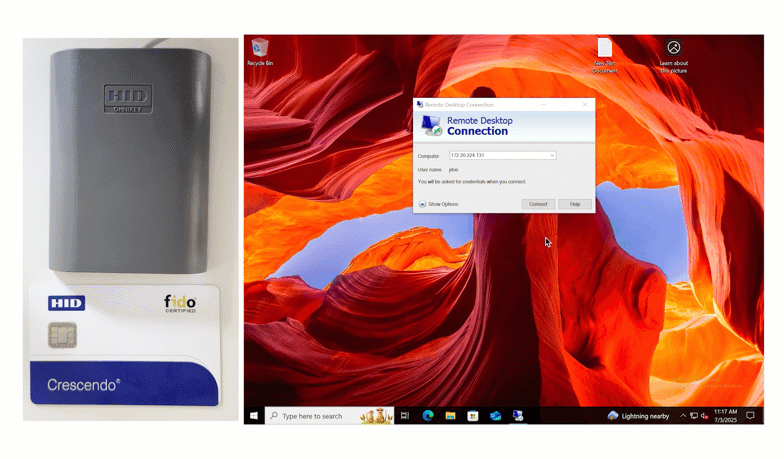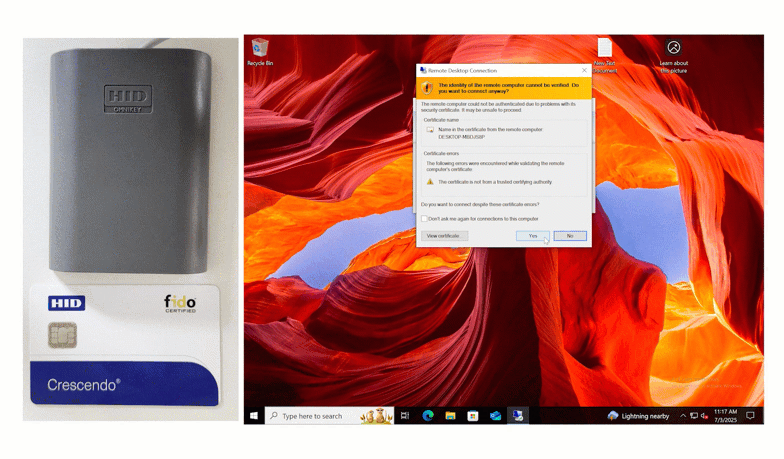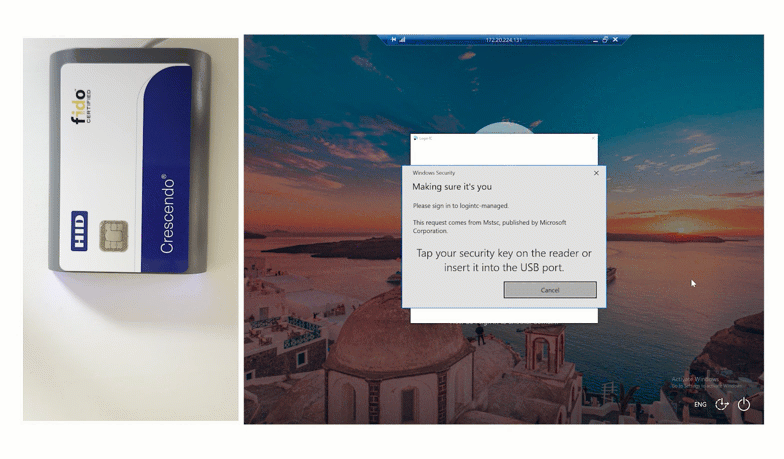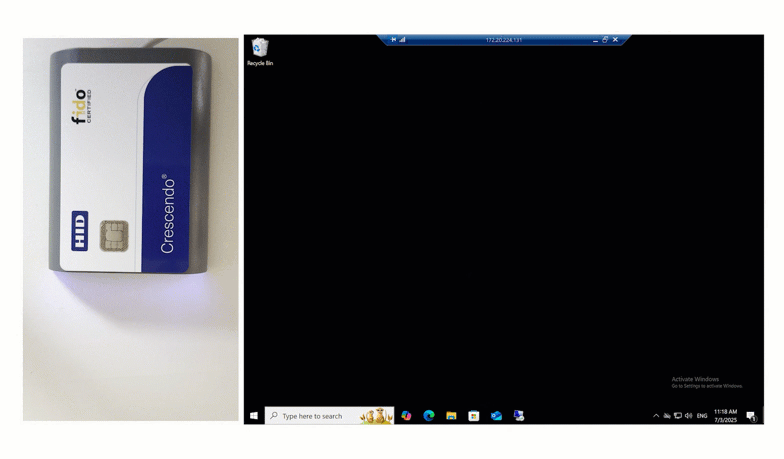
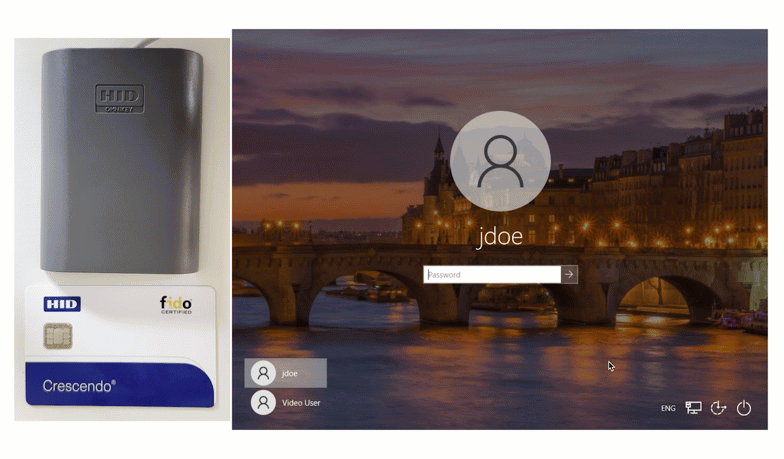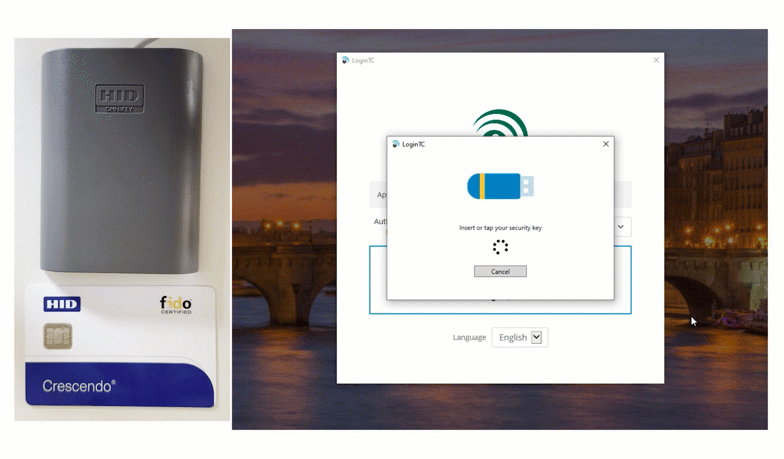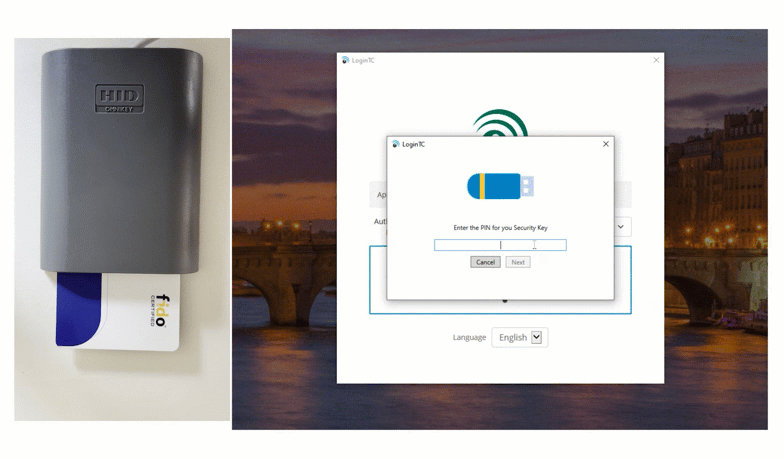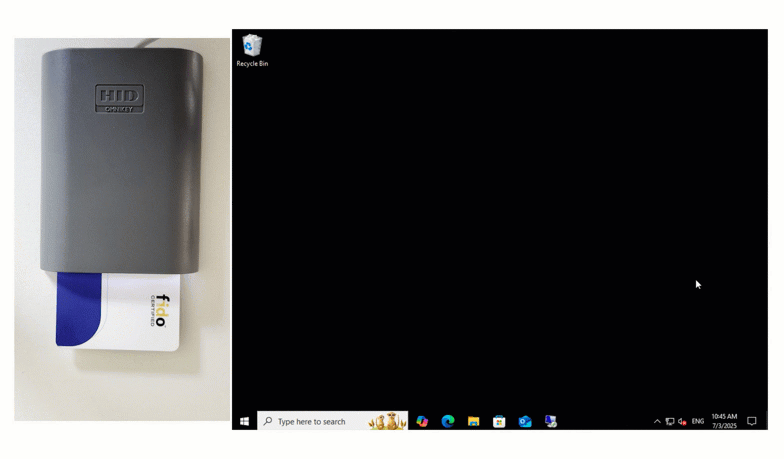
The first way of using a Smart Card for authentication is by tapping the card. Watch below as this end user logs into the Windows Console by tapping their HID Smart Card.
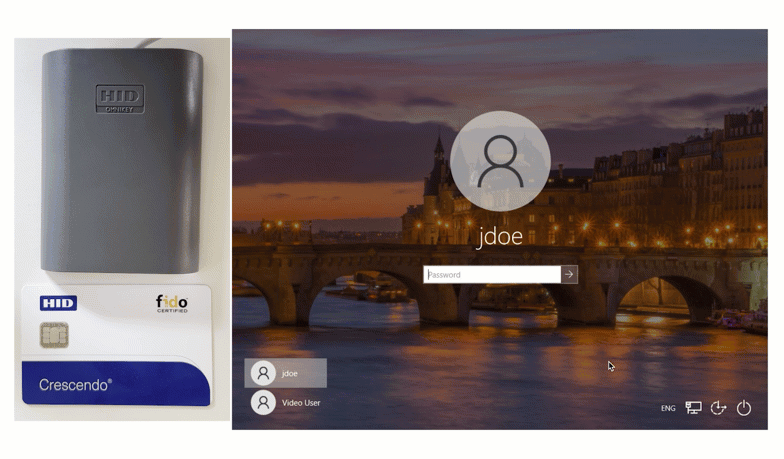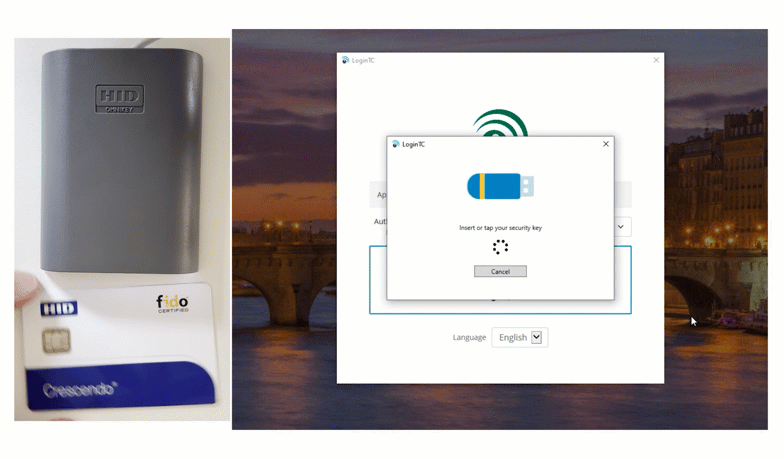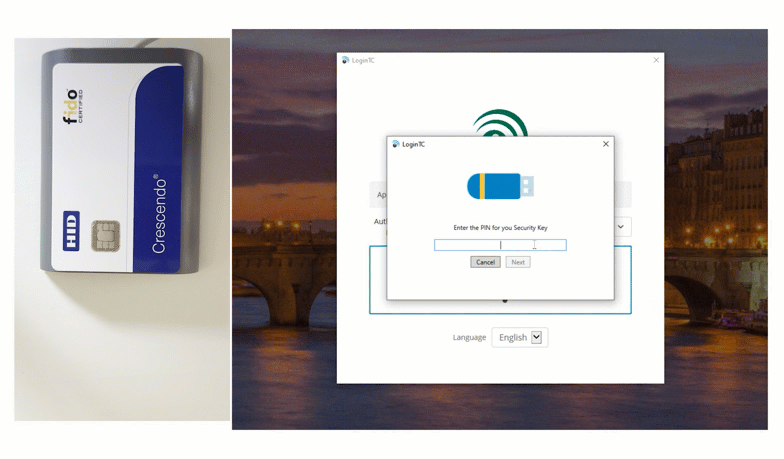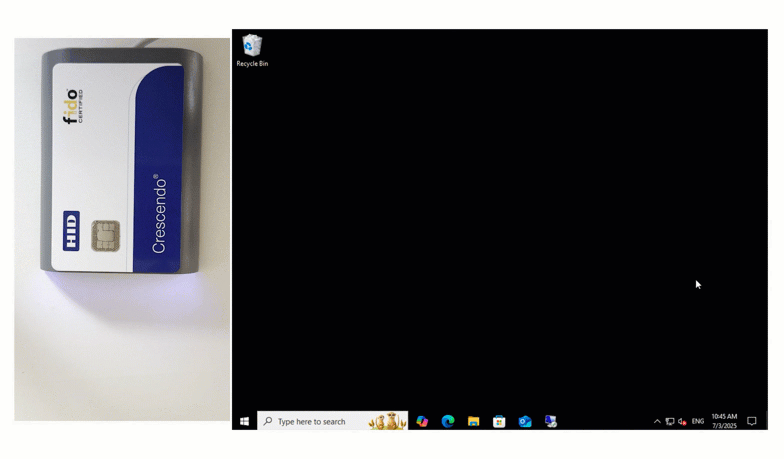
End users input their first factor credentials, and then set their unique Smart Card onto the reader. To finalize authentication, users input their pin, and are successfully logged in.
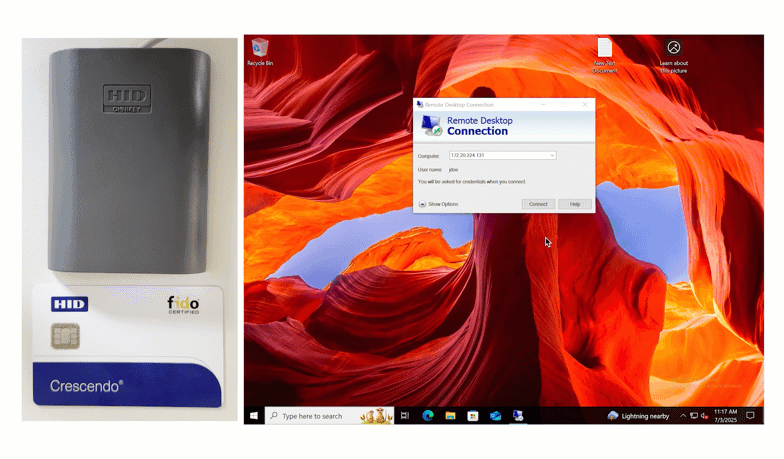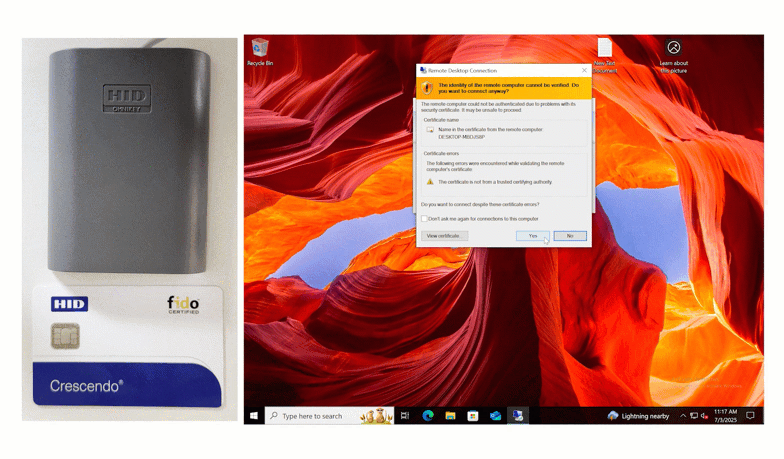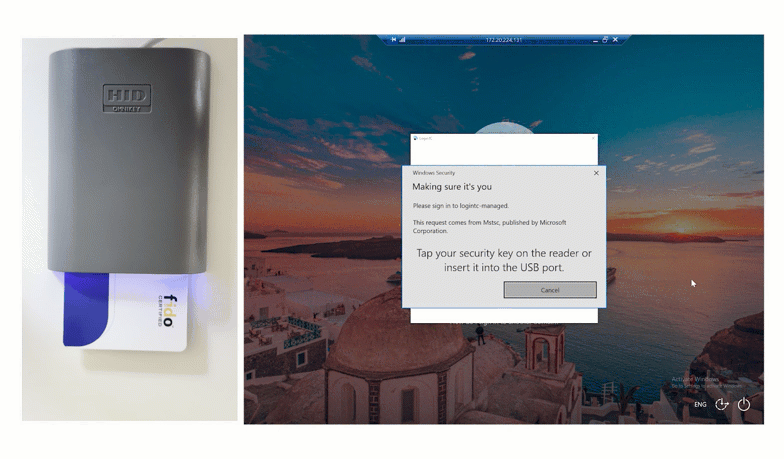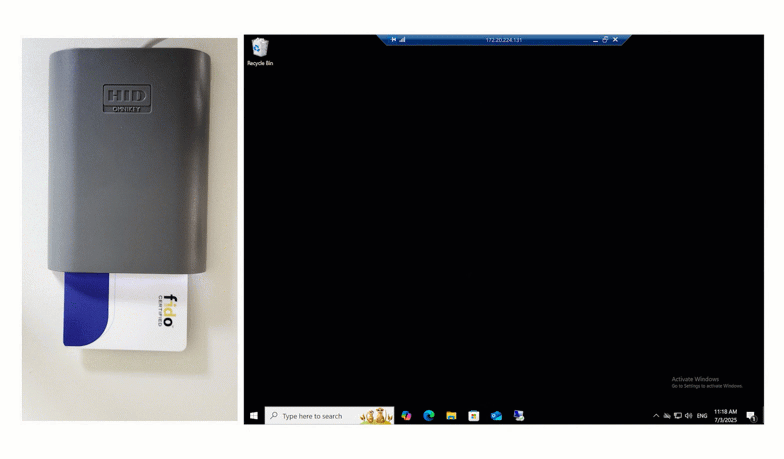
This authentication method also works with Remote Desktop.
This simple method ensures the strongest form of authentication can be achieved with a single tap.
FIDO2 Smart Card: Insert card to authenticate
The second way that Smart Card authentication can be implemented is by inserting the card into a reader. Watch below as a user logs into their Windows machine by inserting their HID Smart Card.
After inputting first factor credentials, the user inserts their card and types their unique pin into the space provided to securely login.
The insert method also works for Remote Desktop logins.
Next steps
Smart Card authentication is available to all customers of LoginTC’s Business-tier cloud MFA solution and LoginTC Managed On-Premises MFA.
Combine LoginTC MFA with the power of HID’s FIDO2-based smart cards for secure authentication into your organization’s digital assets. Smart Card authentication is compatible with the following LoginTC connectors:
- Windows Logon and RDP
- Entra ID
- Outlook Web App (OWA)
- Active Directory Federated Services (AD FS)
- RADIUS for VPNs and firewalls
Start a free trial of LoginTC today to try LoginTC for your organization.