MFA Assessments Unpacked Part 3: Conducting Your MFA Assessment
March 28, 2023 •

In the previous part of our series, MFA Assessments Unpacked, we discussed how to prepare for your MFA assessment. This is to ensure none of your digital assets are missed and you’re aware of everyone who has access to them.
This time, we’ll start conducting our assessment with the aim of identifying two key features of our MFA set-up: Implementation Scope and Authentication Type.
Implementation Scope refers to how comprehensively MFA is applied across your infrastructure. Using the list of assets and users identified in the first two steps, we’ll determine who is required to use MFA to login those assets, and how frequently.
Authentication Type refers to the authentication methods used when MFA is enabled. Not all authentication types are created equally, and we’ll explore the various strengths and limitations of some authentication methods over others.
Let’s dive in!
MFA Assessment Step 3: Find out who’s using MFA and how often
Now that you have your categories of assets mapped out, grouped your users, and know which users can access each of those assets, it’s time to start figuring out who is using MFA and when.
Consider this example:
Company ABC has identified that their privileged accounts and regular employees both have access to their company VPN.
Their privileged employees are always required to authenticate with MFA in order to login. However, the majority of their employees do not have to use MFA to access the VPN.
That’s a gap in Company ABC’s MFA implementation.
Another thing to consider is whether there is a conditional use of MFA to access various assets. Some common examples are:
- Users don’t have to authenticate with MFA when they are in the office on the company’s Wi-Fi network.
- Users only have to authenticate with MFA once in a set number of days (i.e. every 30 or 90 days).
- Users only have to authenticate with MFA when they’re logging in from a new device.
MFA that is used conditionally can also contribute to gaps in your implementation scope.
As a best practice standard, MFA should be enforced for every user, everywhere, every time.
MFA Assessment Step 4: Confirm your company’s available authentication methods
While any MFA is better than none, it’s also true that not all MFA methods are made equally. With recent news stories highlighting the limitations of some types of authentication methods, it’s a good idea to identify what type of second-factor authentication your organization uses.
Let’s revisit the example of Company ABC in our previous step.
Of the handful of privileged user accounts that are required to use MFA to access the company VPN, most of them use push authentication with number matching enabled.
However, in the process of their MFA assessment, they uncovered that two users use SMS as their second factor of authentication.
Since SMS authentication is susceptible to a variety of attacks and bypasses, it’s not recommended for widespread use. Here’s a quick guide to the average strength of common authentication types:
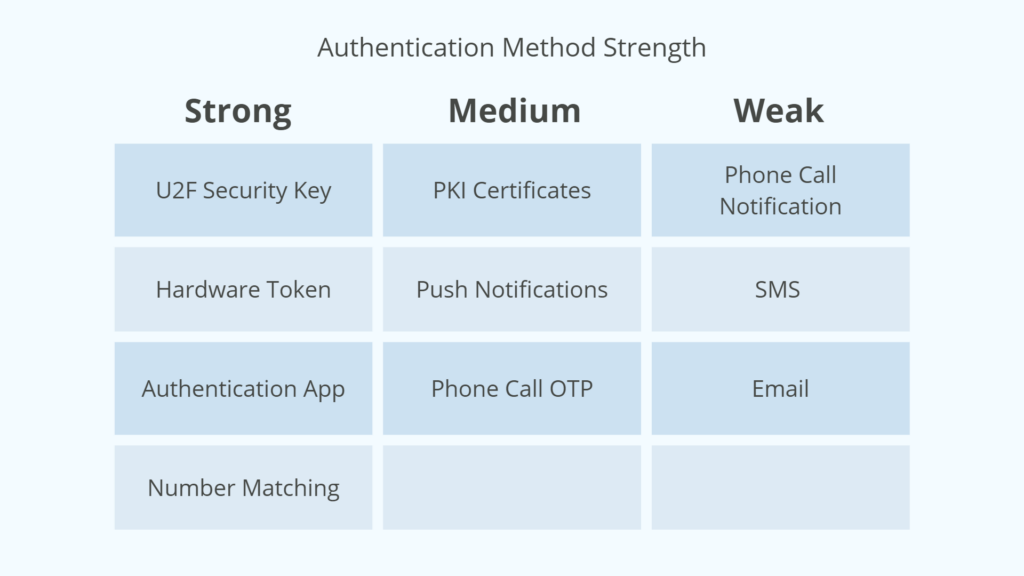
For more information on authentication types, check out the Cybersecurity and Infrastructure Security Agency’s new guidelines released last year.
The counterweight to security is often seen as usability. In general, security tools that are not usable are more likely to be bypassed or disabled by users and administrators.
Whenever possible, MFA should be simple to use and as frictionless as possible for users.
It can be tough to get the right balance between usability and security, but there are resources and experts who can help. Contact us if you have questions about finding the right authentication methods for your unique use cases.
Up next: Finishing your MFA Assessment
Tune in next time to learn about the final two steps in our MFA Assessments process: Fixing Identified Issues and Finding a Solution. These steps will help you complete your MFA assessment using actionable, concrete goals to improve your MFA implementation and solidify MFA best practices in your organization.