Last Updated: January 23, 2025
LoginTC makes it easy for administrators to add two factor authentication to SSH on their Unix systems. This document shows how to configure SSH to require two factor authentication for remote access via Pluggable Authentication Module (PAM).
Explore how LoginTC integrates with SSH below.
Subscription Requirement
Your organization requires the Starter or Professional plan to use the LoginTC SSH Connector. Explore Pricing Plans
There are a wide variety of authentication mechanism users can use to perform MFA with SSH.
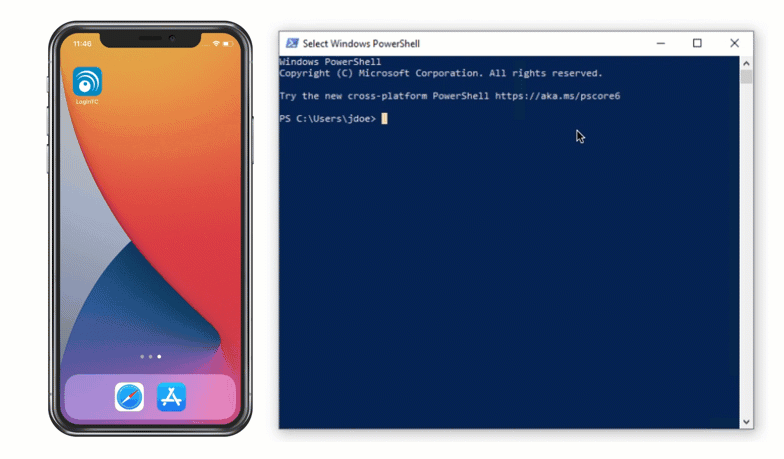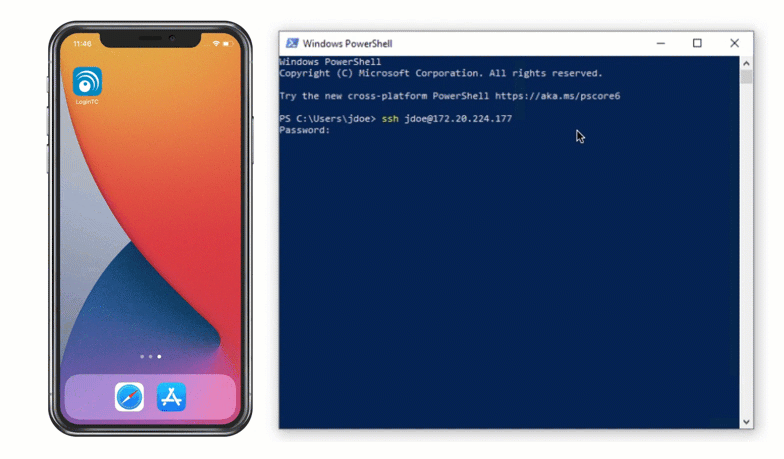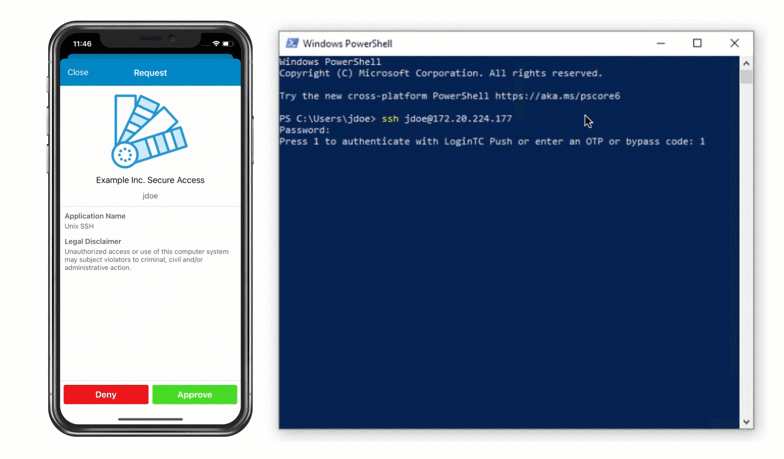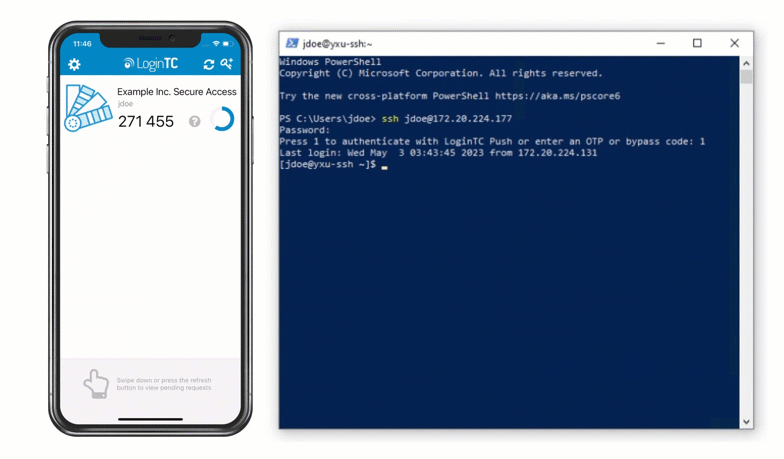
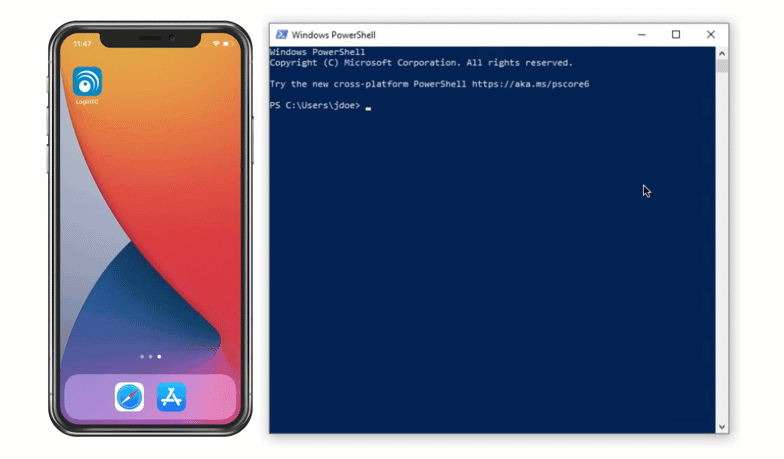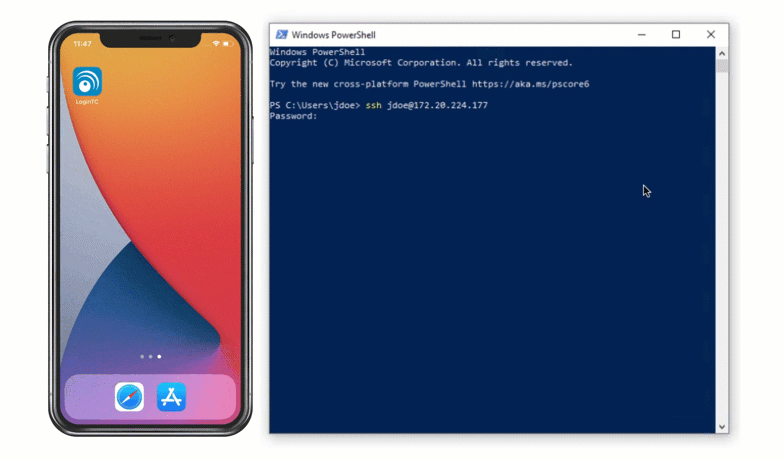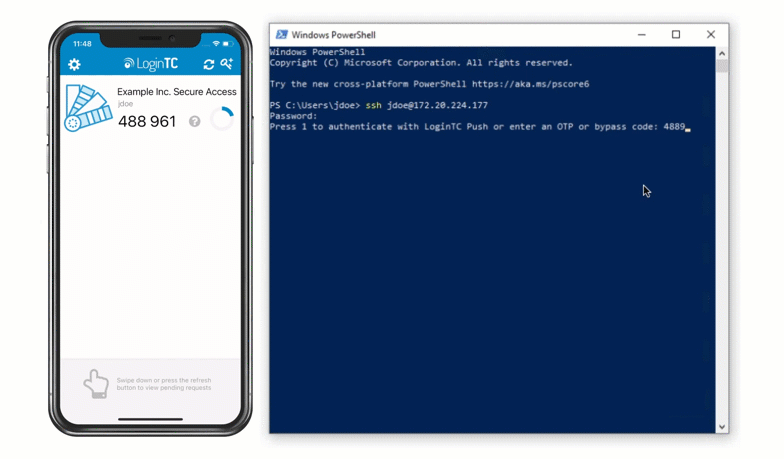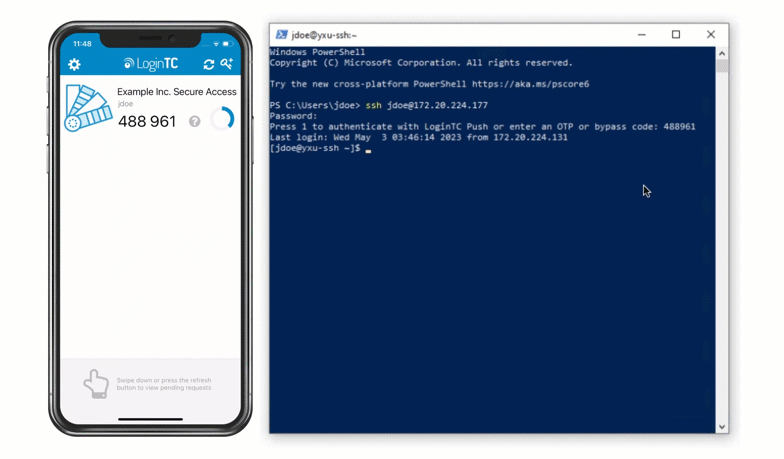
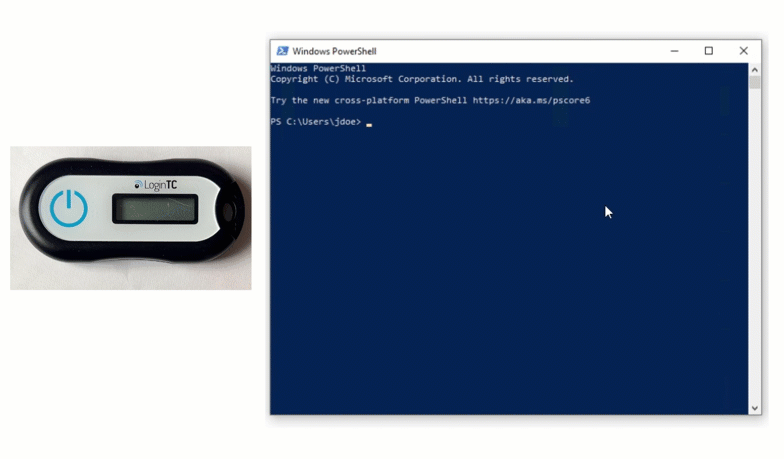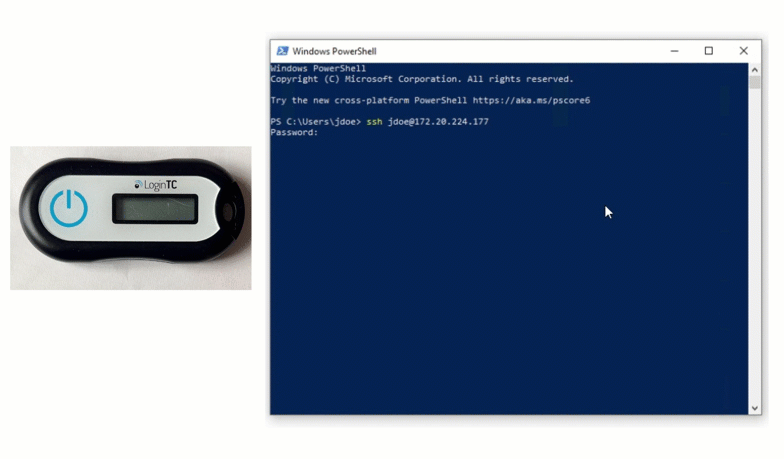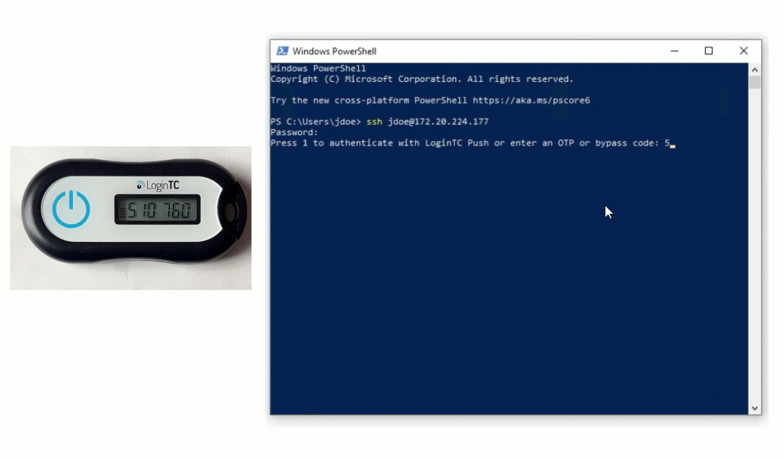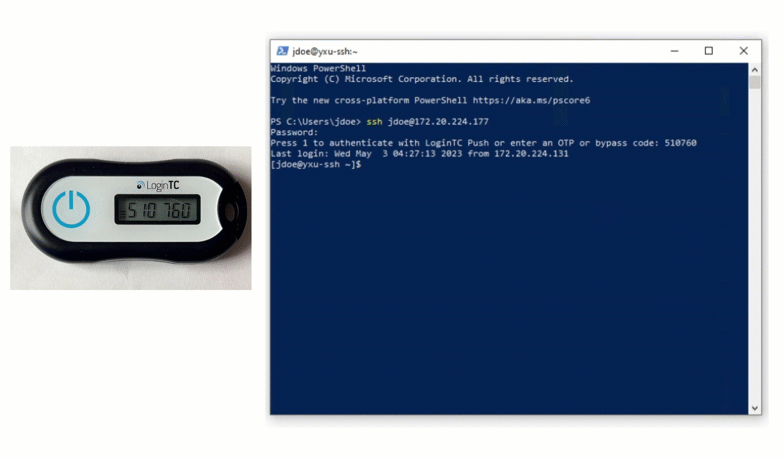
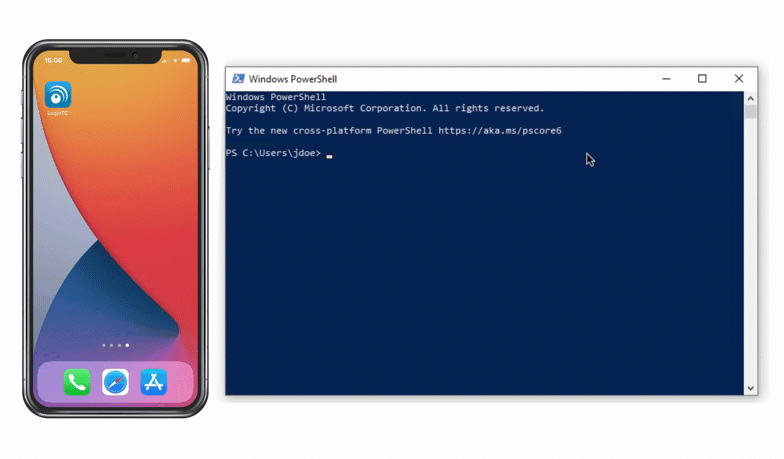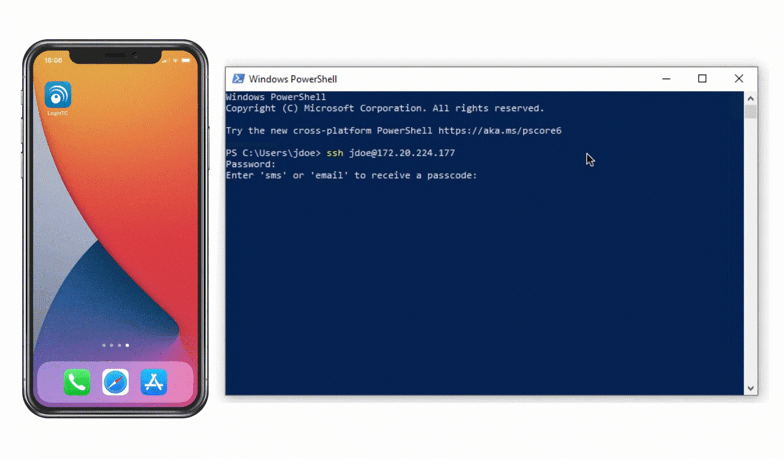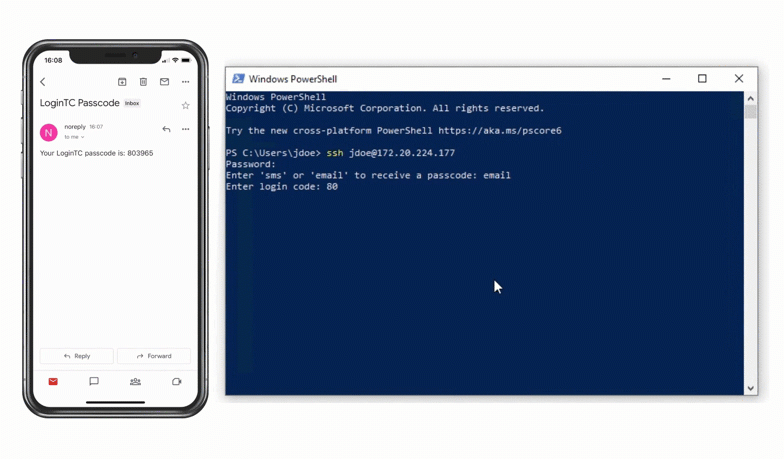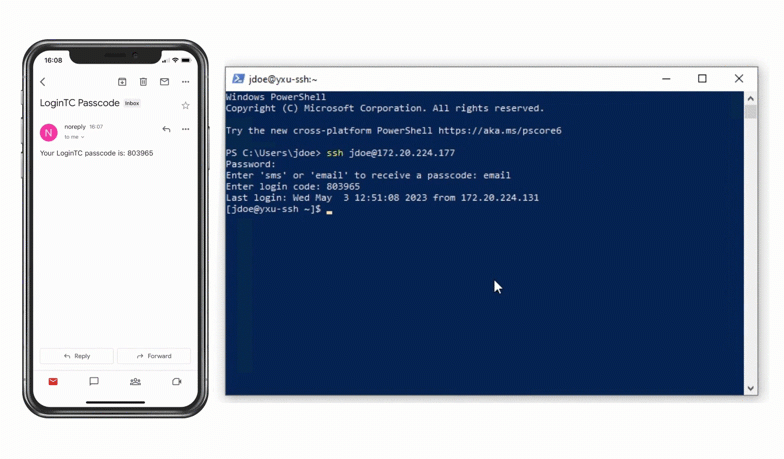
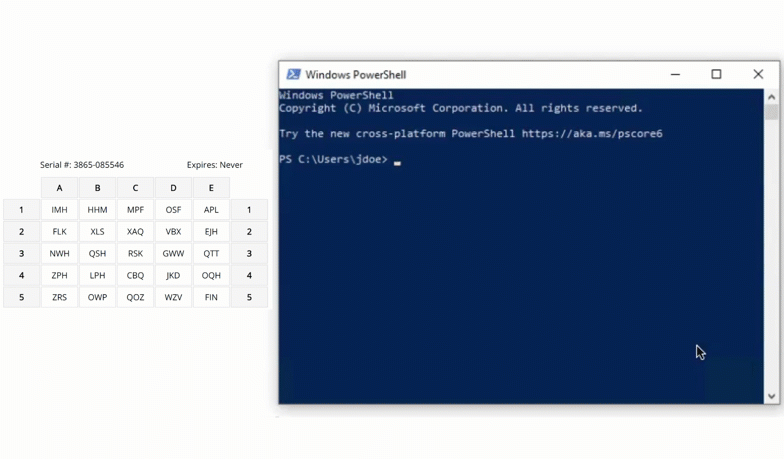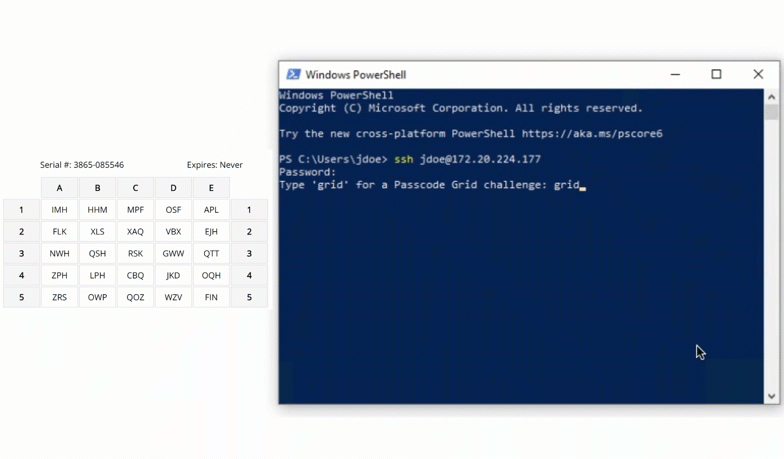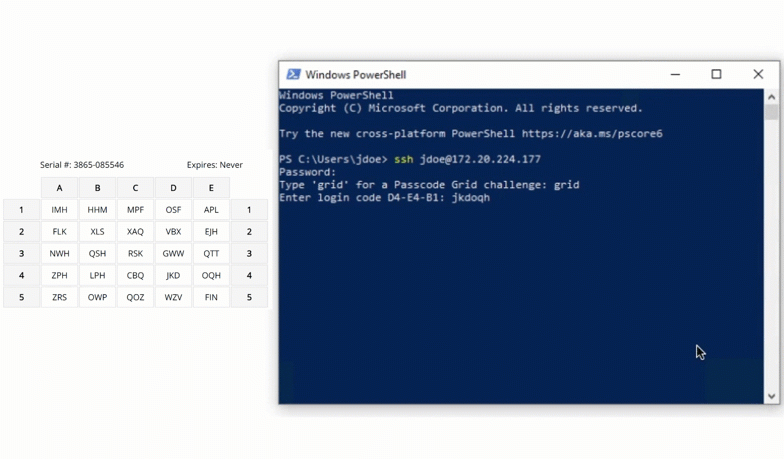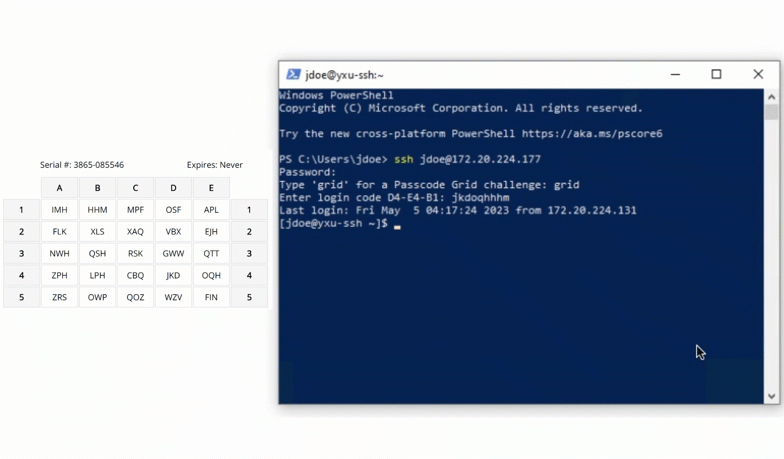
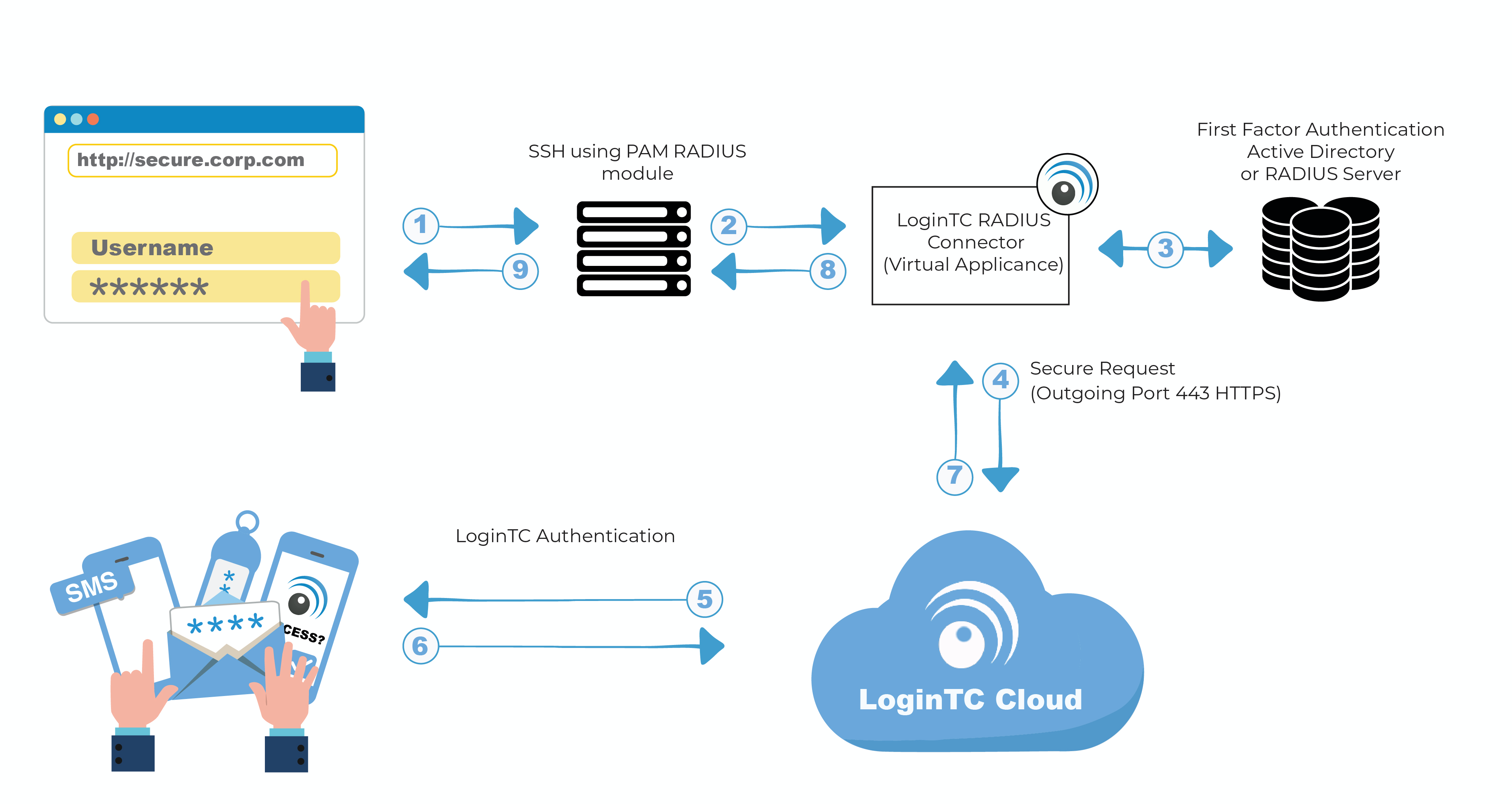
Authentication Flow
- A user attempts access with username / password
- A RADIUS authentication request is sent to the LoginTC RADIUS Connector
- The username / password is verified against an existing first factor directory (LDAP, Active Directory or RADIUS)
- An authentication request is made to LoginTC Cloud Services
- Secure push notification request sent to the user’s mobile or desktop device
- User response (approval or denial of request) sent to LoginTC Cloud Services
- The LoginTC RADIUS Connector polls until the user responds or a timeout is reached
- RADIUS Access-Accept sent back to PAM RADIUS module
- User is granted access via SSH
Prefer Reading a PDF?
Download a PDF file with configuration instructions:
Before proceeding, please ensure you have the following:
- LoginTC Admin Panel account
- Computer virtualization software such as VMware ESXi, VirtualBox, or Hyper-V
- Virtual Machine requirements:
- 1 vCPU
- 2 GiB RAM
- 8 GB disk space
Start by creating a LoginTC Application for your deployment. An Application represents a service (e.g. An application is a service (e.g., VPN or web application) that you want to protect. e) that you want to protect with LoginTC.
Create a LoginTC Application in LoginTC Admin Panel, follow Create Application Steps.
If you have already created a LoginTC Application for your deployment, then you may skip this section and proceed to Installation.
Installation- Download the latest LoginTC RADIUS Connector:
- Import the virtual appliance your computer virtualization software
- Ensure that LoginTC RADIUS CONNECTOR has a virtual network card
- Start the virtual appliance
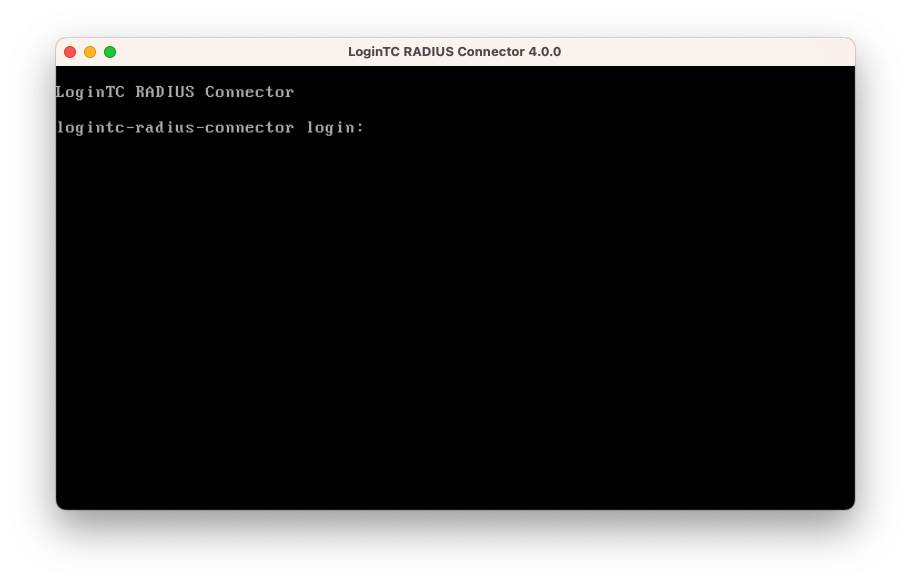
- You will be with a console prompt:
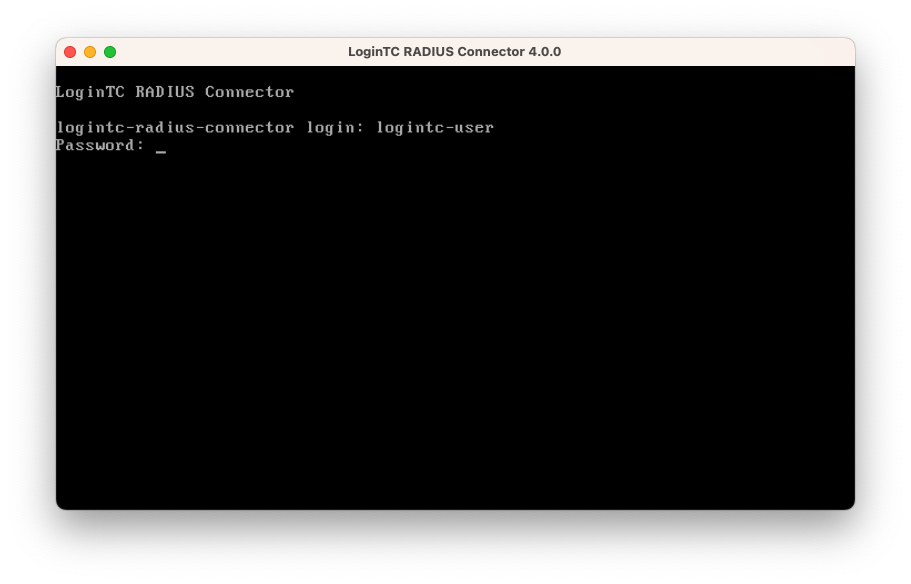
- Login using the username logintc-user and default password logintcradius:
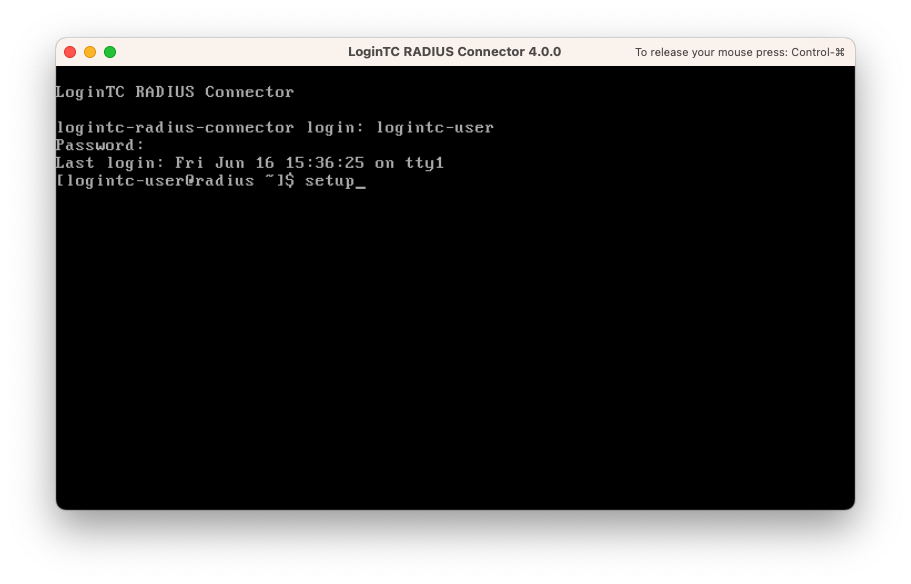
- Once logged in type setup:
- Follow the on-screen prompt to setup a new password for logintc-user:
- By default the appliance network is not configured. Manually configure the network by typing 1 and hit enter:
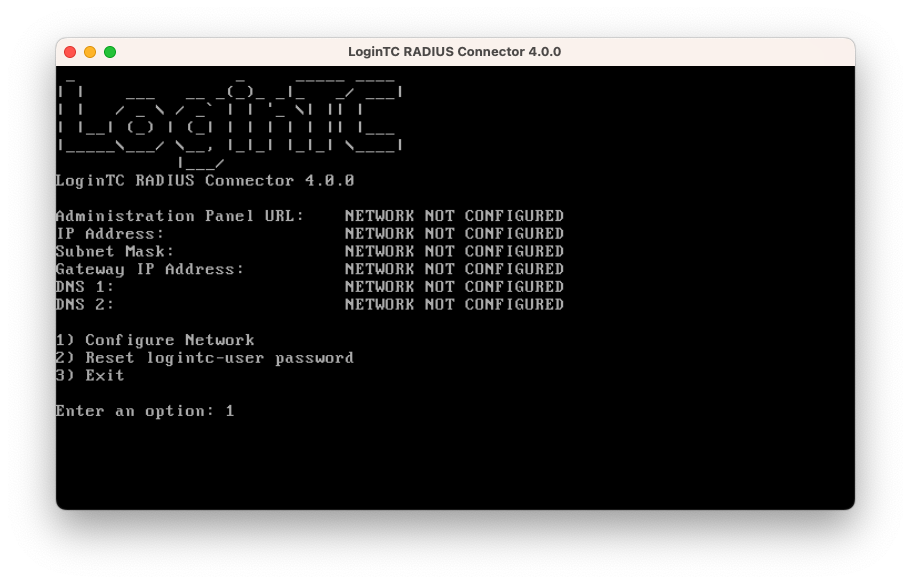
- Follow the on-screen prompts to setup the network. When done, type 1 and enter to confirm the settings:
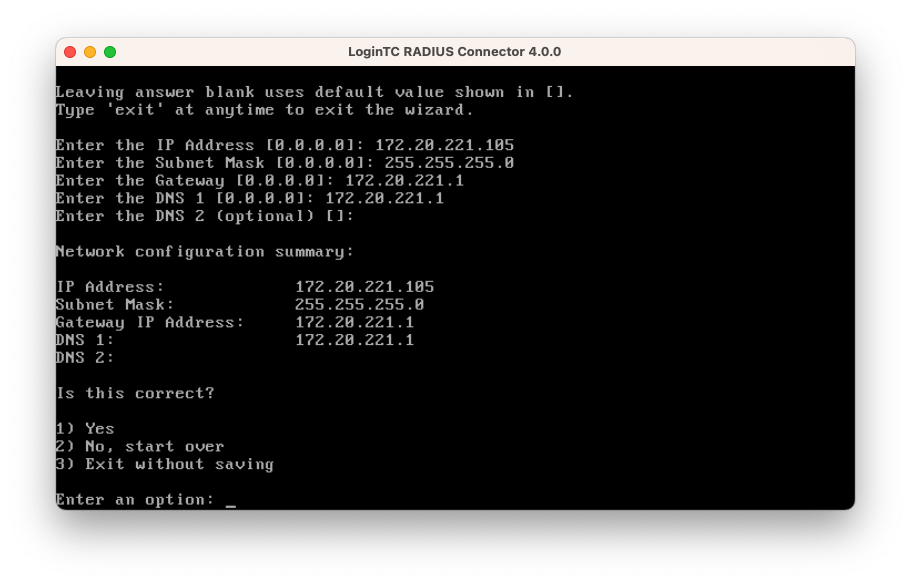
- You will be presented with the network configuration which includes the URL to connect to the appliance from a web browser (example https://172.20.221.105:8443):
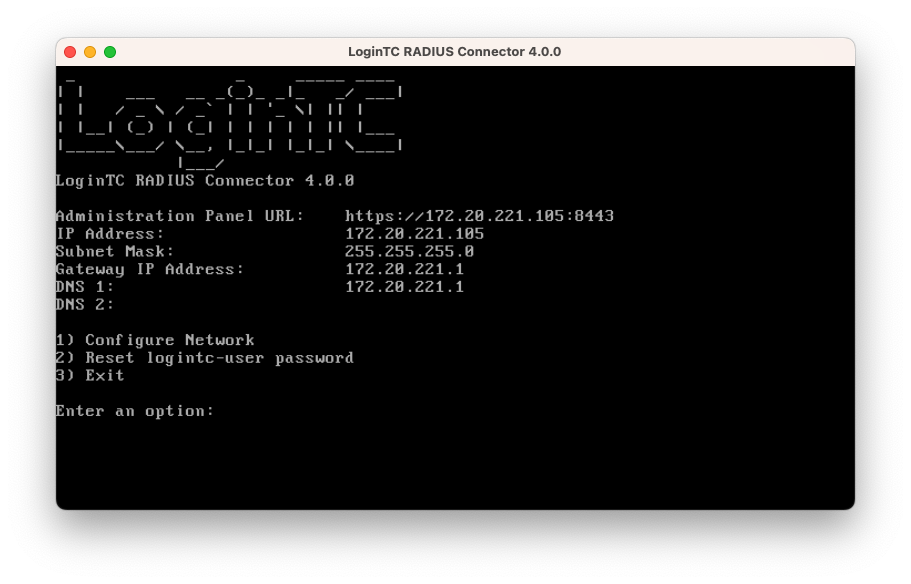
- Navigate to the URL shown in the console dashboard (example:
https://172.20.221.105:8443):
- Login using the username logintc-user and the password that was set in the initial setup:
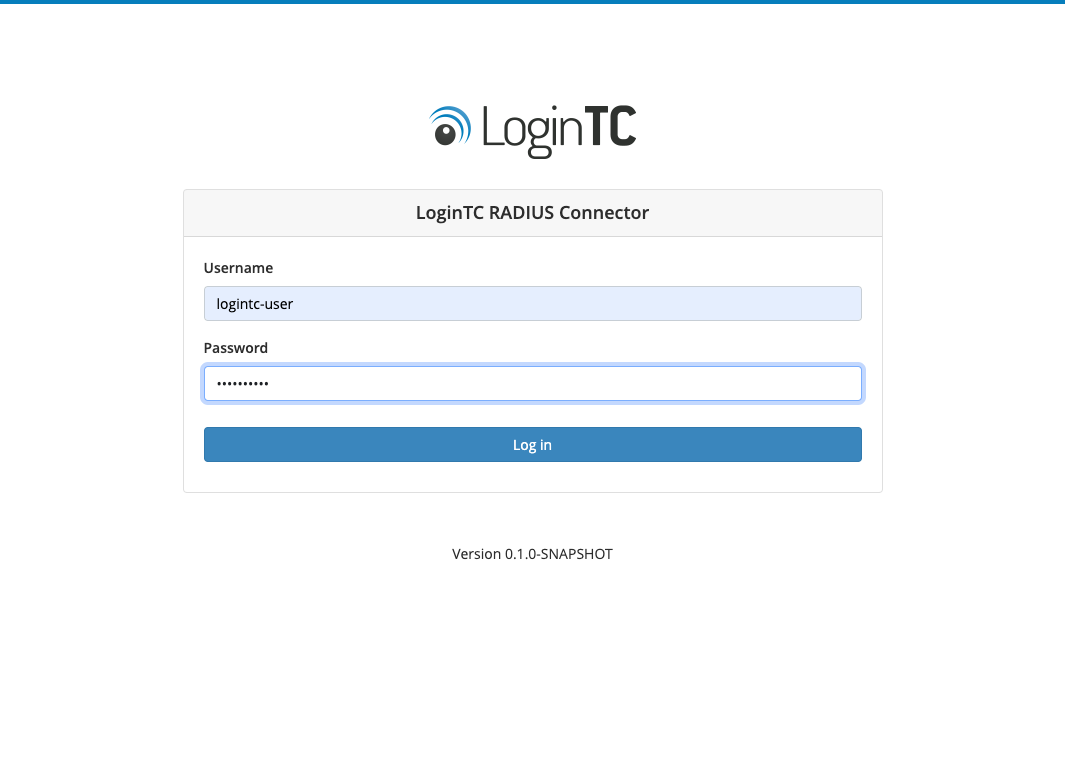
- Link to your existing LoginTC organization. The 64-character Organization API Key is found on the LoginTC Admin Panel under Settings >page API >page Click to view, also see Organization API Key:
- Confirm the LoginTC organization name and click Continue to LoginTC RADIUS Connector:
- If you have an existing LoginTC RADIUS Connector your wish to import configurations then click Yes, import configurations from an existing LoginTC RADIUS Connector, otherwise click No, continue to the adminsitration panel:

NOTE
These instructions assume a new environment. For a complete 2.X / 3.X to 4.X upgrade guide: LoginTC RADIUS Connector Upgrade Guide - Now you are ready to use the LoginTC RADIUS Connector:
| Port | Protocol | Purpose |
|---|---|---|
| 1812 | UDP | RADIUS authentication |
| 443 | TCP | API traffic |
| 8443 | TCP | Web interface |
logintc-user is used for SSH and web access. The default password is logintcradius. You will be asked to change the default password on first boot of the appliance.
Endpoints describe how the appliance will authenticate your RADIUS-speaking device with an optional first factor and LoginTC as a second factor. Each endpoint has 4 Sections:
1. LoginTC SettingsThis section describes how the appliance itself authenticates against LoginTC Admin Panel with your LoginTC Application. Only users that are part of your organization and added to the domain configured will be able to authenticate.
2. User DirectoryThis section describes how the appliance will conduct an optional first factor. Either against an existing LDAP, Active Directory or RADIUS server. If no first factor is selected, then only LoginTC will be used for authentication.
3. Challenge Strategy / PassthroughThis section describes whether the appliance will perform a LoginTC challenge for an authenticating user. The default is to challenge all users. However with either a static list or Active Directory / LDAP Group you can control whom gets challenged to facilitate seamless testing and rollout.
4. Client SettingsThis section describes which RADIUS-speaking device will be connecting to the appliance and whether to encrypt API Key, password and secret parameters.
The web interface makes setting up an endpoint simple and straightforward. Each section has a Test feature, which validates each input value and reports all potential errors. Section specific validation simplifies troubleshooting and gets your infrastructure protected correctly faster.
First Endpoint
Close the console and navigate to your appliance web interface URL. Use username logintc-user and the password you set upon initial launch of the appliance. You will now configure the LoginTC RADIUS Connector.
Create a new endpoint file by clicking + Create your first endpoint:
LoginTC Settings
A list of available Applications will be displayed from your LoginTC organization. Select which LoginTC Application to use:

Configure the application:
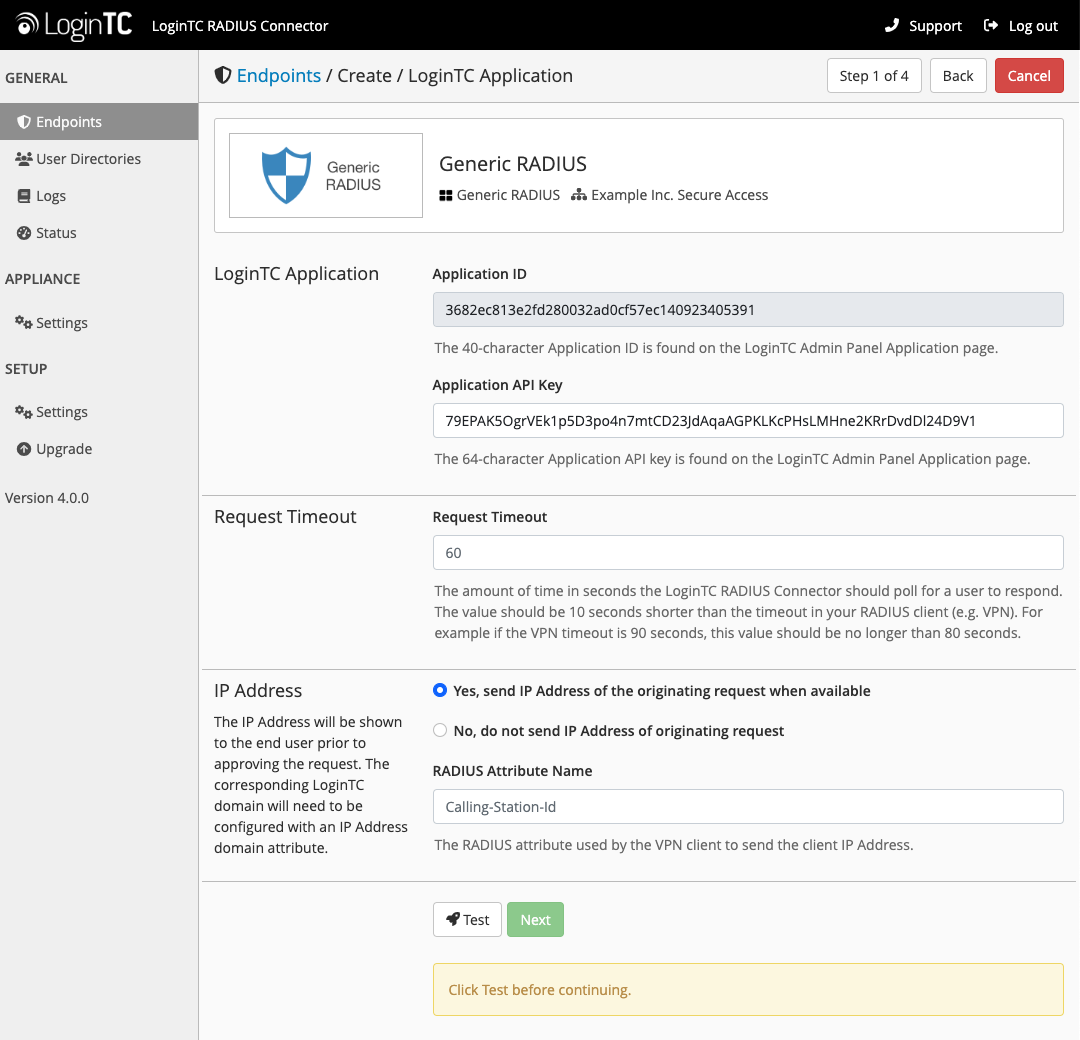
Configuration values:
| Property | Explanation |
|---|---|
Application ID |
The 40-character Application ID, retrieve Application ID |
Application API Key |
The 64-character Application API Key, retrieve Application API Key |
Request Timeout |
Number of seconds that the RADIUS connector will wait for |
The Application ID and Application API Key are found on the LoginTC Admin Panel.
Request Timeout
Make a note of what you set the Request Timeout to as you will need to use a larger timeout value in your RADIUS client. We recommend setting the Request Timeout value to 60 seconds in the LoginTC RADIUS Connector and setting the RADIUS authentication server timeout to 70 seconds in RADIUS Client. For more information see: Recommended settings for an optimal user experience for VPN access
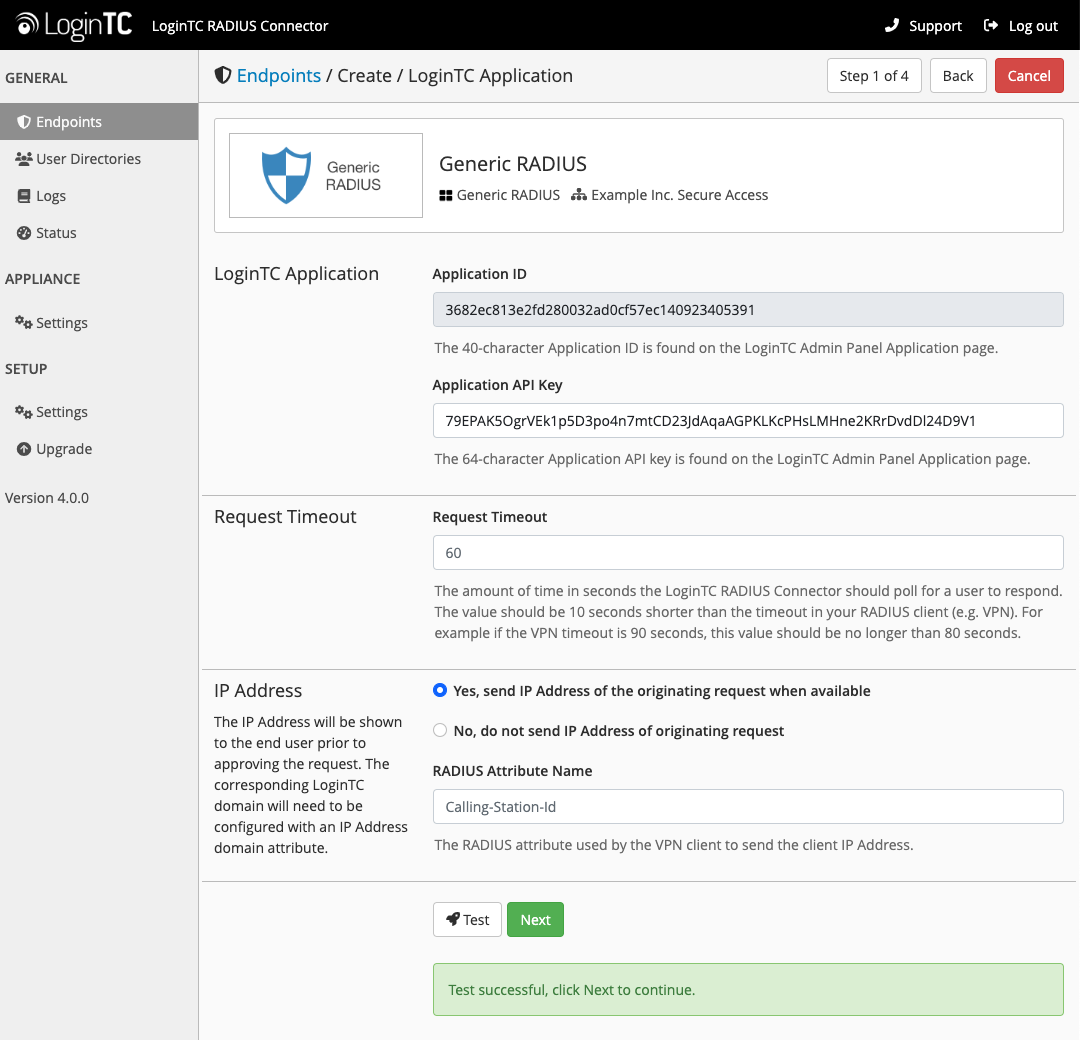
Click Test to validate the values and then click Next:
User Directory
Configure the user directory to be used for first authentication factor in conjunction with LoginTC. You may use Active Directory / LDAP or an existing RADIUS server. You may also opt not to use a first factor, in which case LoginTC will be the only authentication factor.
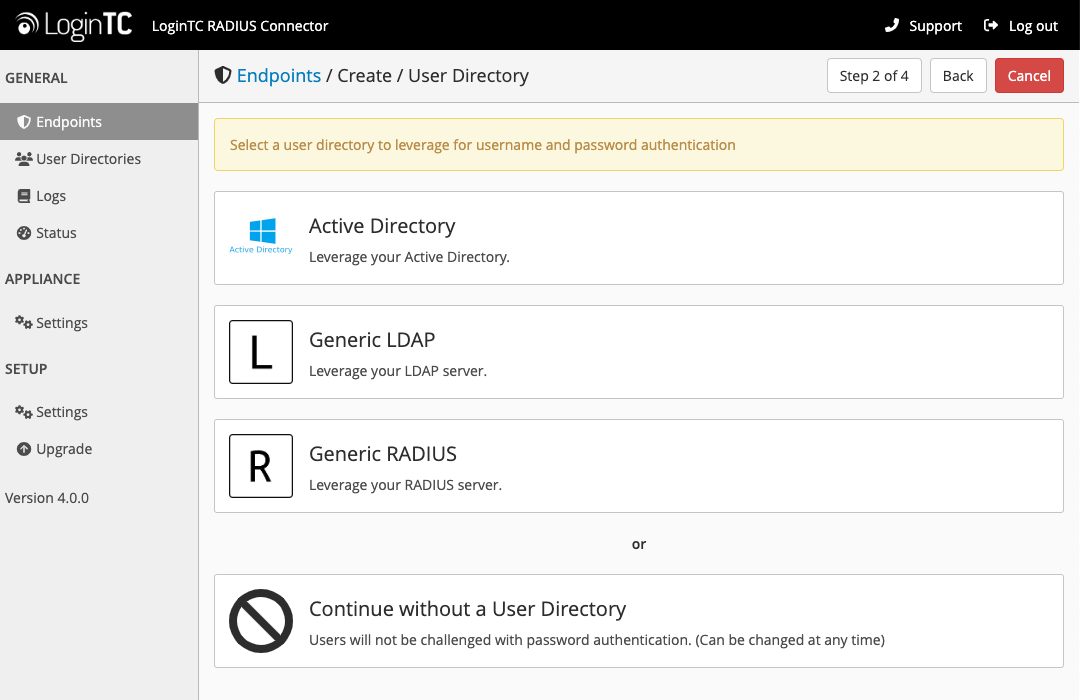
Active Directory / Generic LDAP Option
Select Active Directory if you have an AD Server. For all other LDAP-speaking directory services, such as OpenDJ or OpenLDAP, select Generic LDAP:
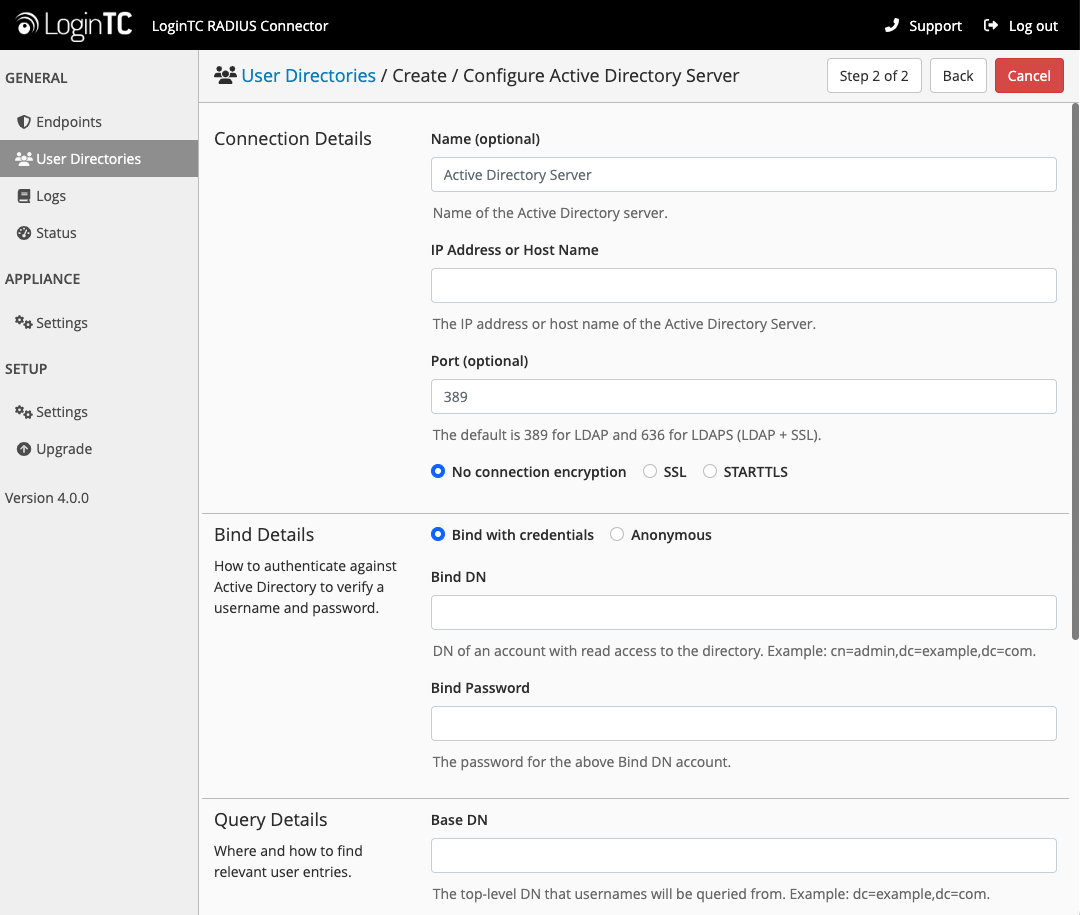
Configuration values:
| Property | Explanation | Examples |
|---|---|---|
host |
Host or IP address of the LDAP server | ldap.example.com or 192.168.1.42 |
port (optional) |
Port if LDAP server uses non-standard (i.e., 389/636) |
4000 |
bind_dn |
DN of a user with read access to the directory | cn=admin,dc=example,dc=com |
bind_password |
The password for the above bind_dn account | password |
base_dn |
The top-level DN that you wish to query from | dc=example,dc=com |
attr_username |
The attribute containing the user’s username | sAMAccountName or uid |
attr_name |
The attribute containing the user’s real name | displayName or cn |
attr_email |
The attribute containing the user’s email address | mail or email |
LDAP Group (optional) |
The name of the LDAP group to be sent back to the authenticating server. | SSLVPN-Users |
encryption (optional) |
Encryption mechanism | ssl or startTLS |
cacert (optional) |
CA certificate file (PEM format) | /opt/logintc/cacert.pem |
Click Test to validate the values and then click Next.
Existing RADIUS Server Option
If you want to use your existing RADIUS server, select RADIUS:
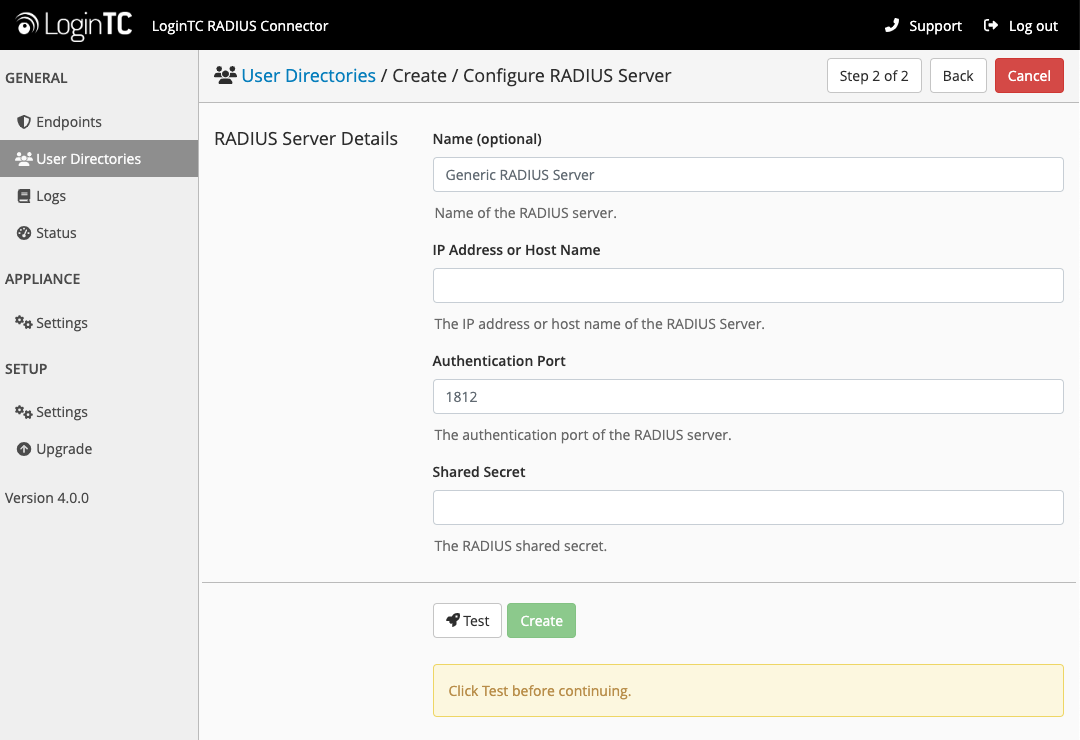
Configuration values:
| Property | Explanation | Examples |
|---|---|---|
IP Address or Host Name |
Host or IP address of the RADIUS server | radius.example.com or 192.168.1.43 |
Authentication Port (optional) |
Port if the RADIUS server uses non-standard (i.e., 1812) |
1812 |
Shared Secret |
The secret shared between the RADIUS server and the LoginTC RADIUS Connector | testing123 |
RADIUS Vendor-Specific Attributes
Common Vendor-Specific Attributes (VSAs) returned by the RADIUS server will be relayed.Click Test to validate the values and then click Next.
Challenge Strategy / Passthrough
Configure which users will be challenged with LoginTC. This allows you to control how LoginTC will be phased in for your users. This flexibility allows for seamless testing and roll out.
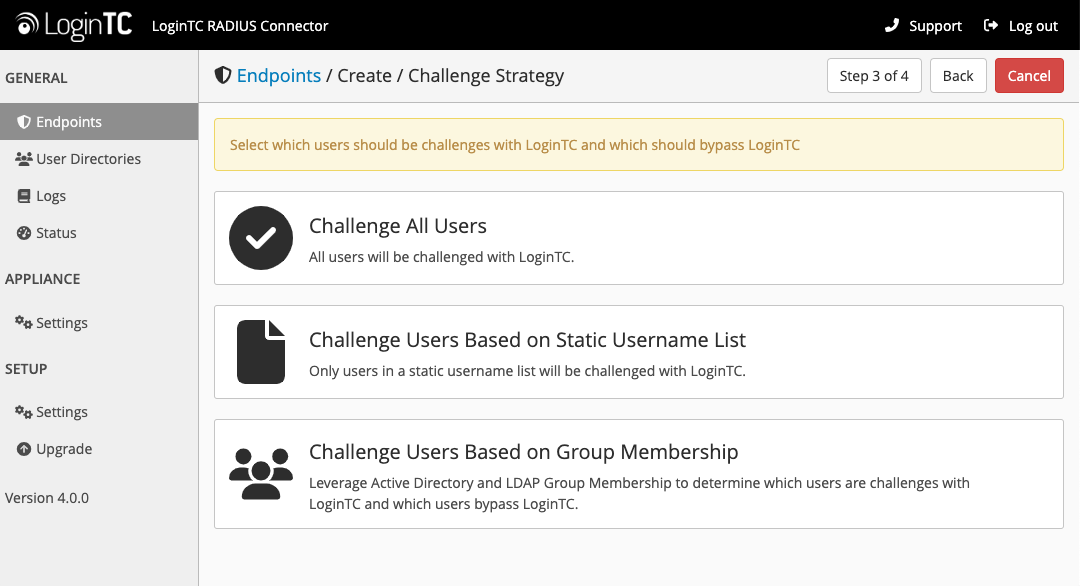
For example, with smaller or proof of concept deployments select the Static List option. Users on the static list will be challenged with LoginTC, while those not on the list will only be challenged with the configured First Authentication Factor. That means you will be able to test LoginTC without affecting existing users accessing your VPN.
For larger deployments you can elect to use the Active Directory or LDAP Group option. Only users part of a particular LDAP or Active Directory Group will be challenged with LoginTC. As your users are migrating to LoginTC your LDAP and Active Directory group policy will ensure that they will be challenged with LoginTC. Users not part of the group will only be challenged with the configured First Authentication Factor.
Challenge All Users
Select this option if you wish every user to be challenged with LoginTC.
Challenge Users Based on Static Username List
Select this option if you wish to have a static list of users that will be challenged with LoginTC. Good for small number of users.
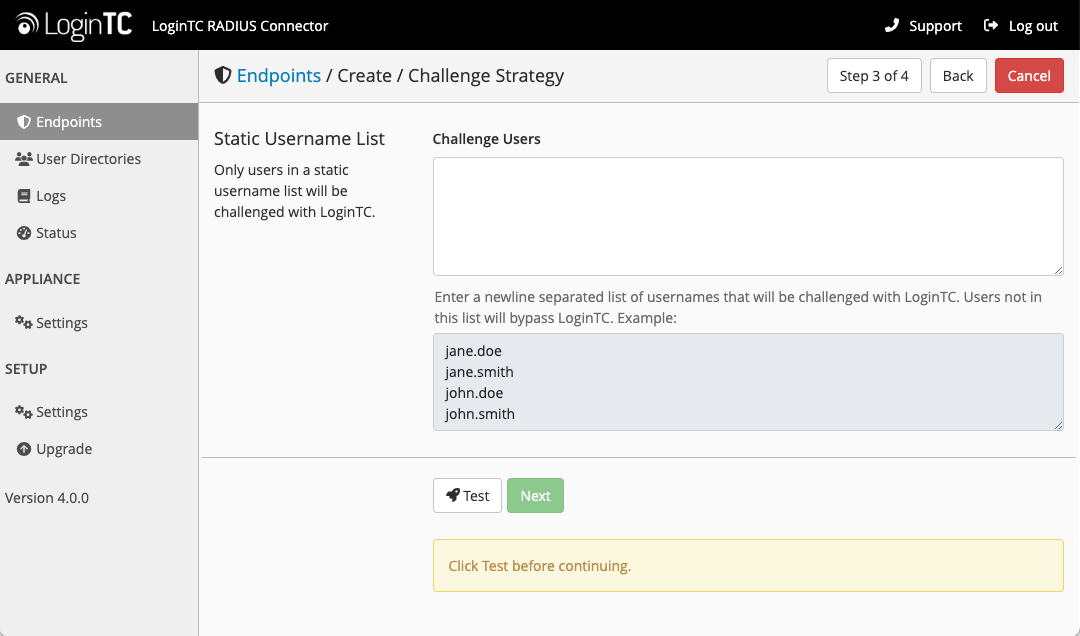
LoginTC challenge users: a new line separated list of usernames. For example:
jane.doe
jane.smith
john.doe
john.smith
Challenge Users Based on Group Membership
Select this option if you wish to have only users part of a particular Active Directory or LDAP group to be challenged with LoginTC. Good for medium and large number of users.
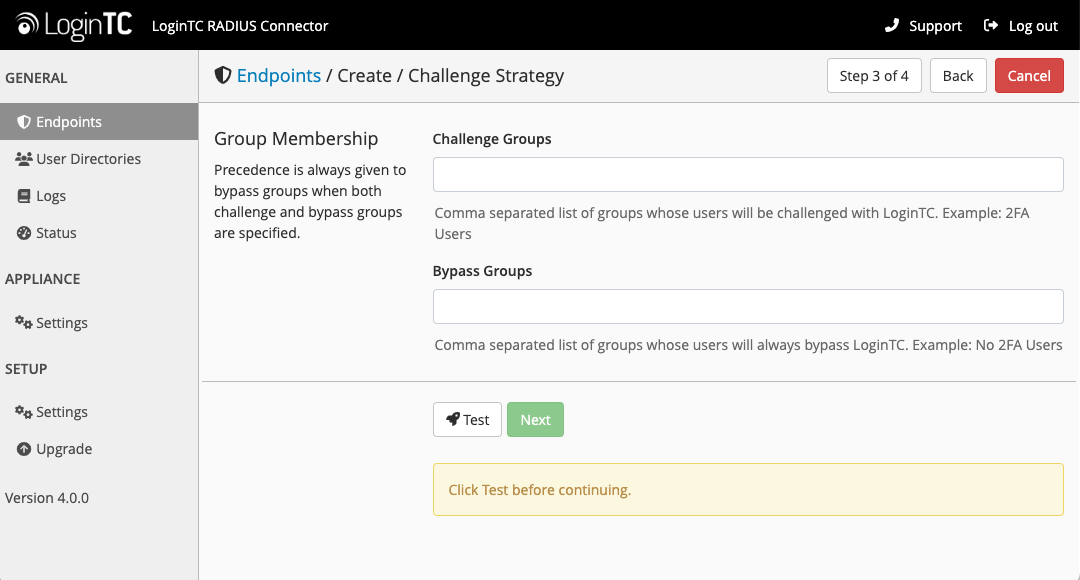
Configuration values:
| Property | Explanation | Examples |
|---|---|---|
Challenge Groups (Optional) |
Comma separated list of groups for which users will be challenged with LoginTC | SSLVPN-Users or two-factor-users |
Challenge Groups (Optional) |
Comma separated list of groups for which users will always bypass LoginTC | NOMFA-Users |
Click Test to validate the values and then click Next.
Client Settings
Configure RADIUS client (e.g. your RADIUS-speaking VPN):
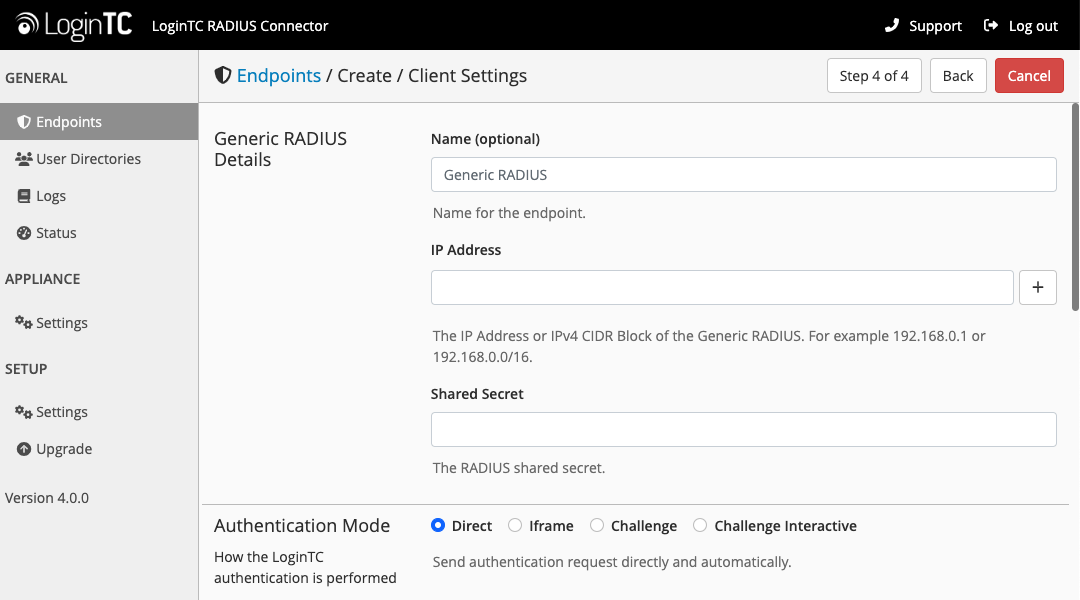
Client configuration values:
| Property | Explanation | Examples |
|---|---|---|
name |
A unique identifier of your RADIUS client | CorporateVPN |
IP Addresss |
The IP address of your RADIUS client (e.g. your RADIUS-speaking VPN). Add additional IP Addresses by clicking plus. | 192.168.1.44 |
Shared Secret |
The secret shared between the LoginTC RADIUS Connector and its client | bigsecret |
Under Authentication Mode select Challenge
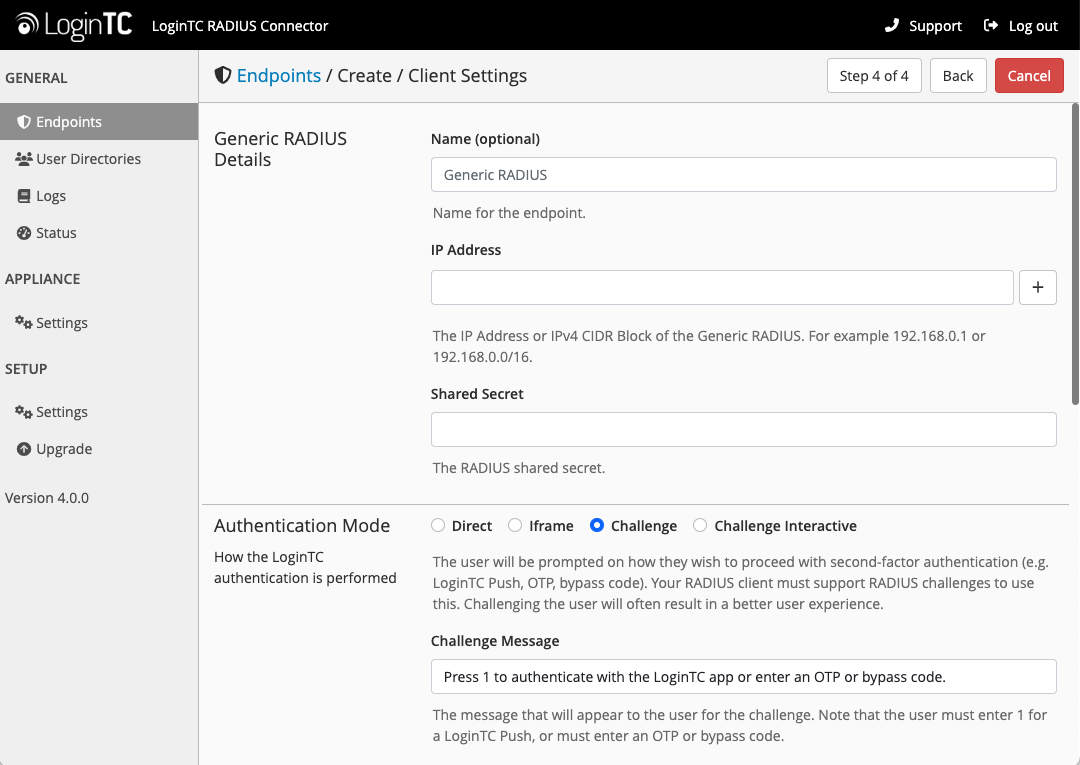
The user will be prompted on how they wish to proceed with second-factor authentication (e.g. LoginTC Push, OTP, bypass code). Your RADIUS client must support RADIUS challenges to use this. Challenging the user will often result in a better user experience. See User Experience for more information.
Click Test to validate the values and then click Save.
 Testing
Testing
When you are ready to test your configuration, create a LoginTC user (if you haven’t already done so). The username should match your existing user. Provision a token by following the steps:
- In a new tab / window log into the LoginTC Admin Panel
- Click Domains
- Click on your domain
- Click on Members
- Click Issue Token button beside your user:
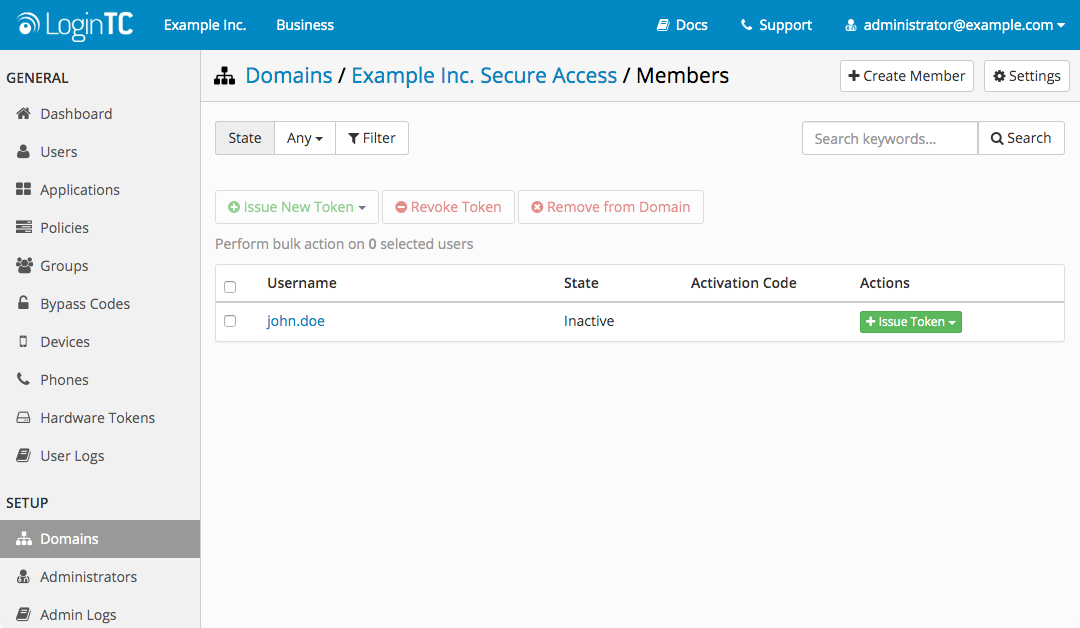
- A 10-character alphanumeric activation code will appear beside the user:
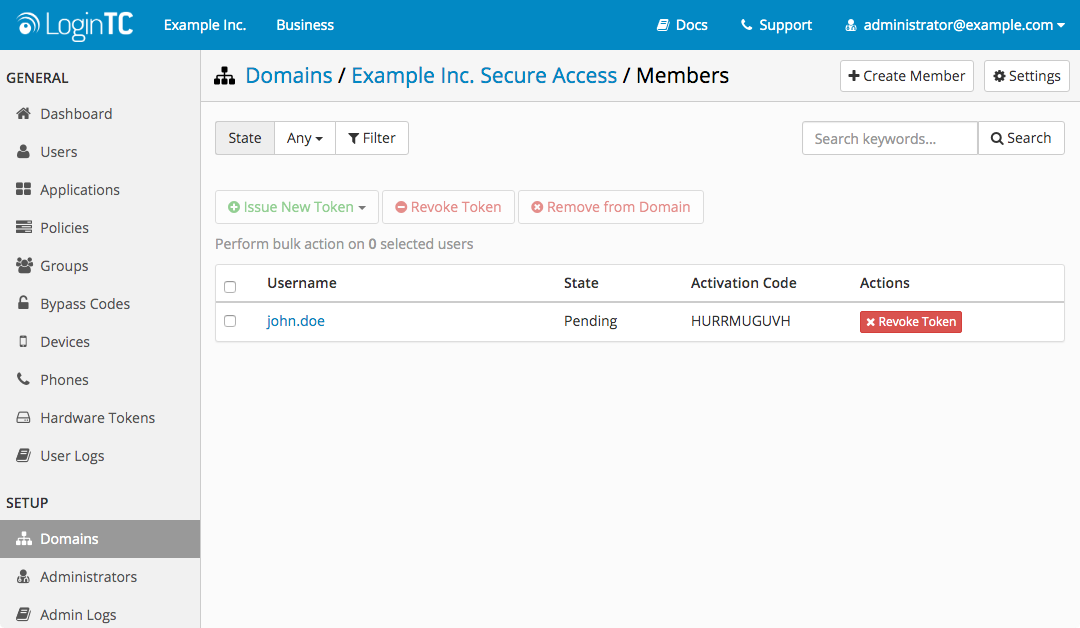
- Open the LoginTC mobile app.
- Enter the 10-character alphanumeric activation code:
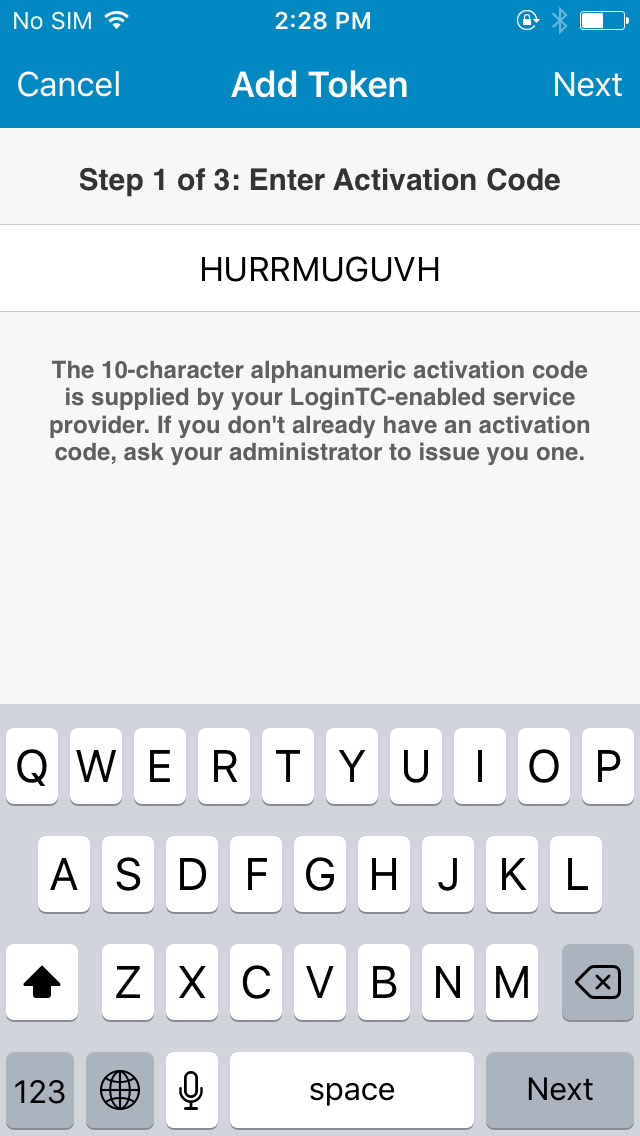
- Load the token to complete the process
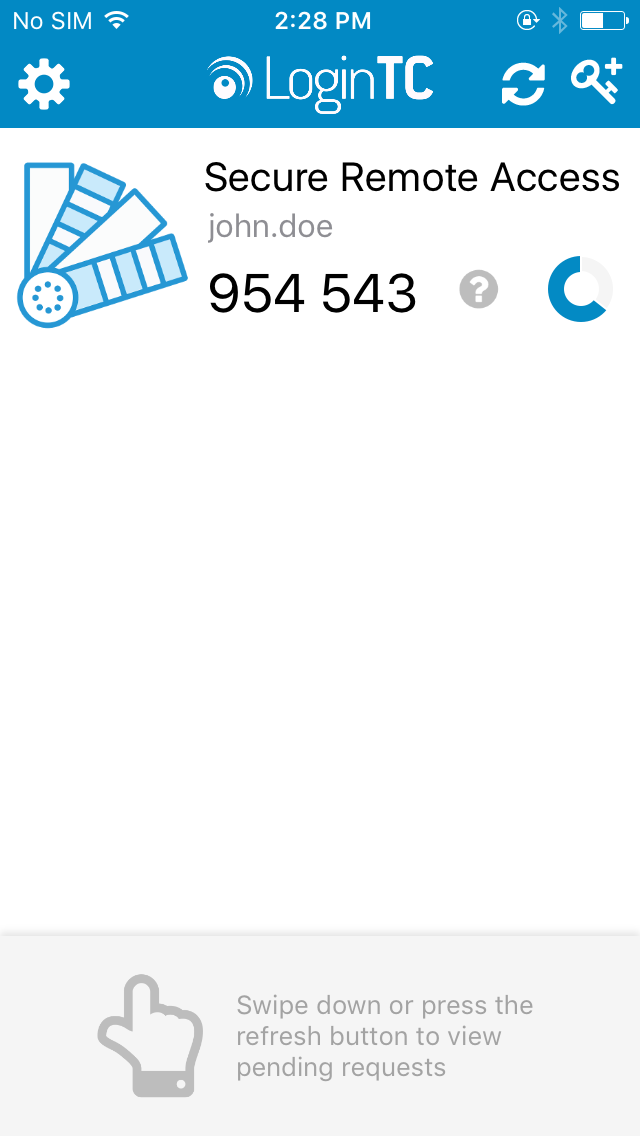
When you have loaded a token for your new user and domain, navigate to your appliance web interface URL:
Click Test Configuration:
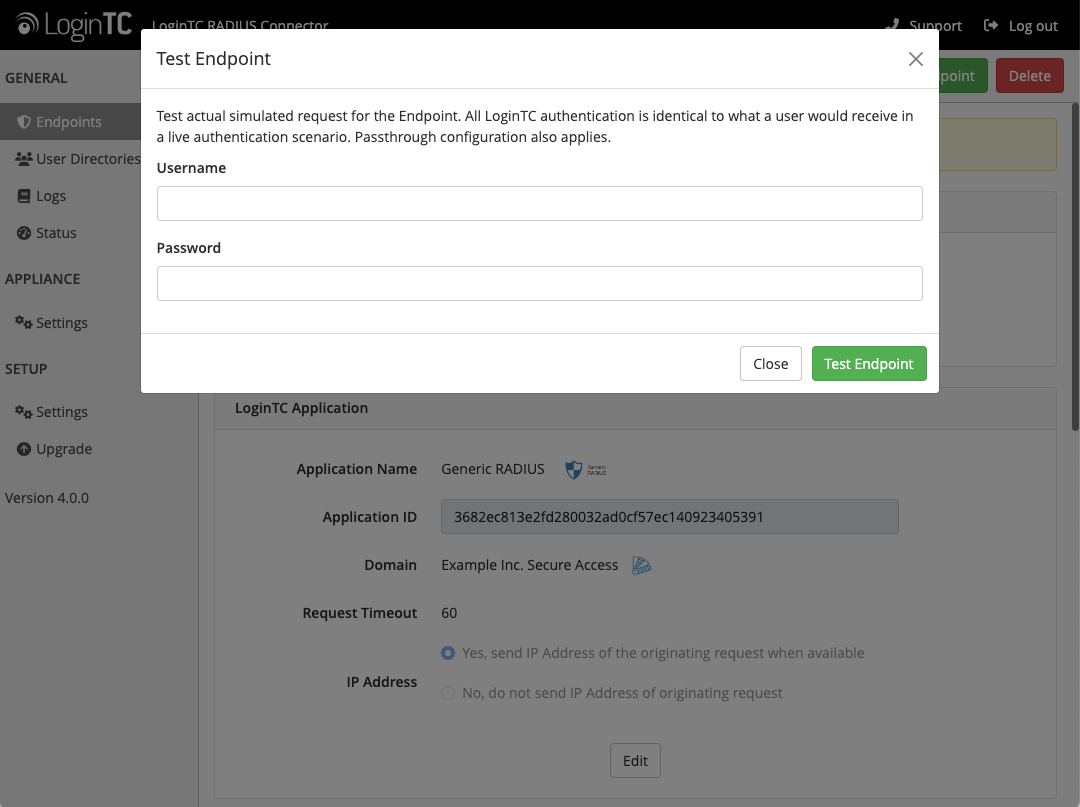
Enter a valid username and password; if there is no password leave it blank. A simulated authentication request will be sent to the mobile or desktop device with the user token loaded. Approve the request to continue:
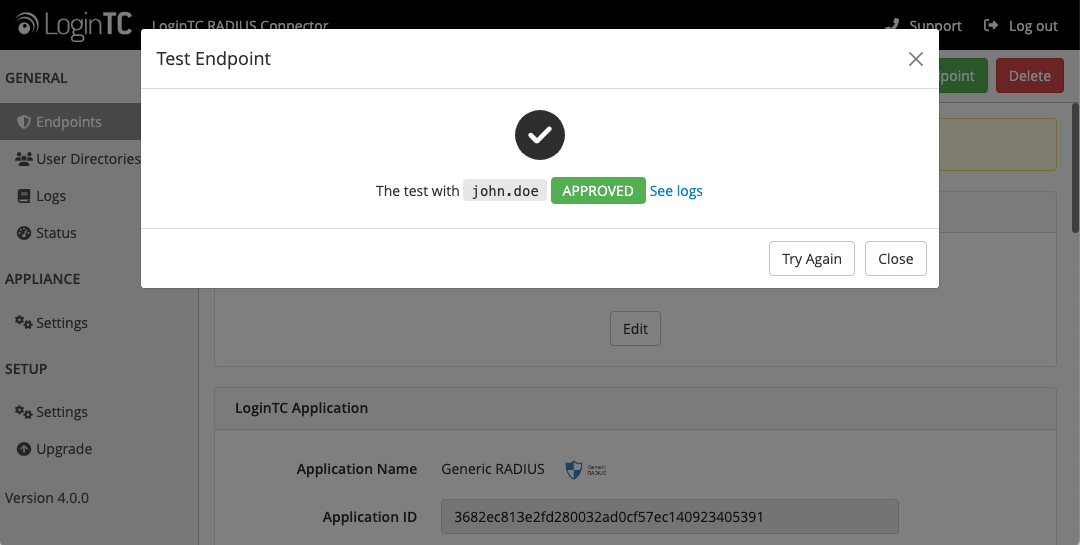
Congratulations! Your appliance can successfully broker first and second factor authentication. The only remaining step is to configure your RADIUS device!
If there was an error during testing, the following will appear:
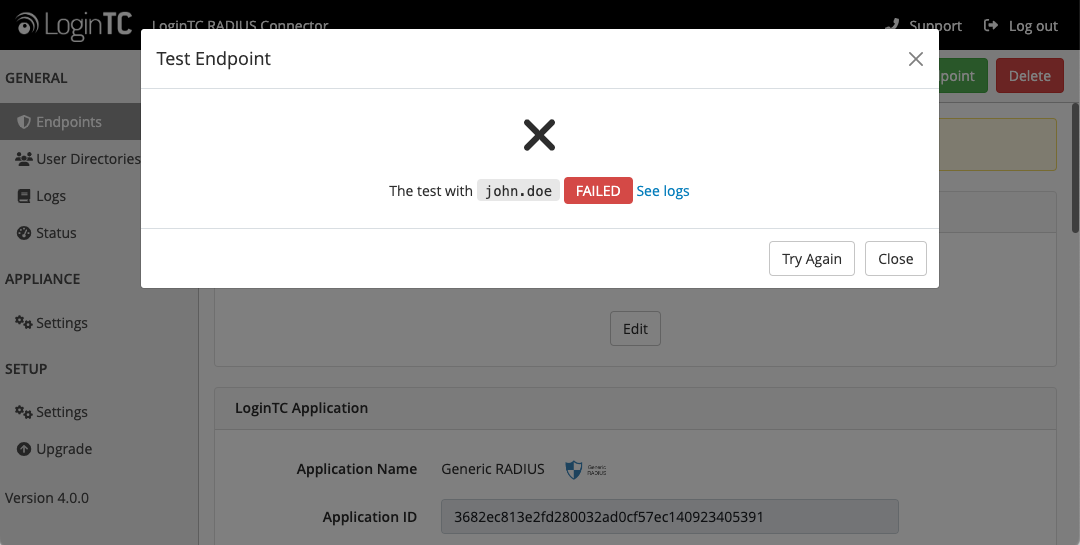
In this case, click See logs (or click the Logs section):
The PAM RADIUS module from FreeRADIUS allows the use of RADIUS to PAM authentication. It can be leverage for almost any service that supports PAM-based authentication. If your system does not have pam_radius_auth package installed you will need to do so. Below are instructions for CentOS. For more information on pam_radius_auth and installing it on your system please see: FreeRADIUS PAM Authentication and Accounting module.
Advisory
PAM RADIUS is free software. LoginTC does not take responsibility for its support.
Using Ubuntu?
Check out this knowledge base article for configuring LoginTC with PAM RADIUS on Ubuntu: Protect SSH to Ubuntu
Install PAM RADIUS on CentOS / RedHat
Step 1: Developer tools:
$ sudo yum install wget gcc pam pam-devel make -yStep 2: Build PAM RADIUS module pre:
$ cd /tmp
$ sudo wget https://github.com/FreeRADIUS/pam_radius/archive/release_3_0_0.tar.gz
$ sudo tar xvzf pam_radius-release_3_0_0.tar.gz
$ cd pam_radius-release_3_0_0
$ sudo ./configure
$ sudo make
Note: PAM RADIUS module version
For updates please see: FreeRADIUS PAM Authentication and Accounting module.
Step 3: Copy shared object library to appropriate folder
32-bit
$ sudo cp pam_radius_auth.so /lib/security/64-bit
$ sudo cp pam_radius_auth.so /lib64/security/The PAM RADIUS library is installed and ready to be configured.
Configure SSH
Step 1: Create or edit the /etc/raddb/server file to point to your LoginTC RADIUS Connector:
$ sudo mkdir -p /etc/raddb
$ sudo vi /etc/raddb/server
# server[:port] shared_secret timeout (s)
# Example server (change to fit your needs):
192.168.1.40 bigsecret 60The server should match the IP Address of your LoginTC RADIUS Connector, while the shared_secret should match to one configured in the LoginTC RADIUS Connector. The corresponding settings are configured in Client and Encryption portion of the LoginTC RADIUS Connector.
Note: Timeout
We recommend the maximum timeout of 60 seconds allowed by the PAM RADIUS module.
Step 2: Edit /etc/pam.d/sshd (NOTE: recommend making a backup of `/etc/pam.d/sshd` prior to editing):
$ sudo vi /etc/pam.d/sshdOption 1: Use only LoginTC RADIUS Connector for authentication:
#%PAM-1.0
#auth substack password-auth
auth required pam_radius_auth.so
auth include postlogin
account required pam_sepermit.so
account required pam_nologin.so
account include password-auth
password include password-auth
# pam_selinux.so close should be the first session rule
session required pam_selinux.so close
session required pam_loginuid.so
# pam_selinux.so open should only be followed by sessions to be executed in the user context
session required pam_selinux.so open env_params
session required pam_namespace.so
session optional pam_keyinit.so force revoke
session optional pam_motd.so
session include password-auth
session include postlogin
Option 2: Use local password authentication AND LoginTC RADIUS Connector for authentication:
#%PAM-1.0
auth substack password-auth
auth required pam_radius_auth.so
auth include postlogin
account required pam_sepermit.so
account required pam_nologin.so
account include password-auth
password include password-auth
# pam_selinux.so close should be the first session rule
session required pam_selinux.so close
session required pam_loginuid.so
# pam_selinux.so open should only be followed by sessions to be executed in the user context
session required pam_selinux.so open env_params
session required pam_namespace.so
session optional pam_keyinit.so force revoke
session optional pam_motd.so
session include password-auth
session include postlogin
Challenge Mode
Client Settings Authentication Mode should be set to Challenge.

Challenge Message: Press 1 to authenticate with LoginTC Push or enter an OTP or bypass code:
Also ensure /etc/ssh/sshd_config has ChallengeResponseAuthentication yes set.
Step 3: Restart sshd:
$ sudo service sshd restartYou are now ready to test two-factor authentication with SSH.
Testing
There are many flavours of Linux, RHEL, CentOS and we recommend extensive testing prior to applying these configurations in a production environment. Console login should be accessible during testing as a fallback.
Test by accessing SSH. The username of the UNIX user must match the username of the user created in your organization and added to the domain you have configured to authenticate against.
$ ssh john.doe@192.168.0.30You will be prompted for a password and then challenged with LoginTC.
User ManagementThere are several options for managing your users within LoginTC:
- Individual users can be added manually in LoginTC Admin Panel
- Bulk operations using CSV Import
- Programmatically manage user lifecycle with the REST API
- One-way user synchronization of users to LoginTC Admin is performed using User Sync Tool.
Step 1: Revert the changes made to /etc/pam.d/sshd in Step 2 of Configure SSH
$ sudo vi /etc/pam.d/sshdStep 2: Restart sshd:
$ sudo service sshd restartLogs can be found on the Logs tab:

PAM RADIUS Module
For troubleshooting related to the PAM RADIUS module please refer to: FreeRADIUS PAM Authentication and Accounting module.
Not Authenticating
If you are unable to authenticate, navigate to your appliance web interface URL and click Status:
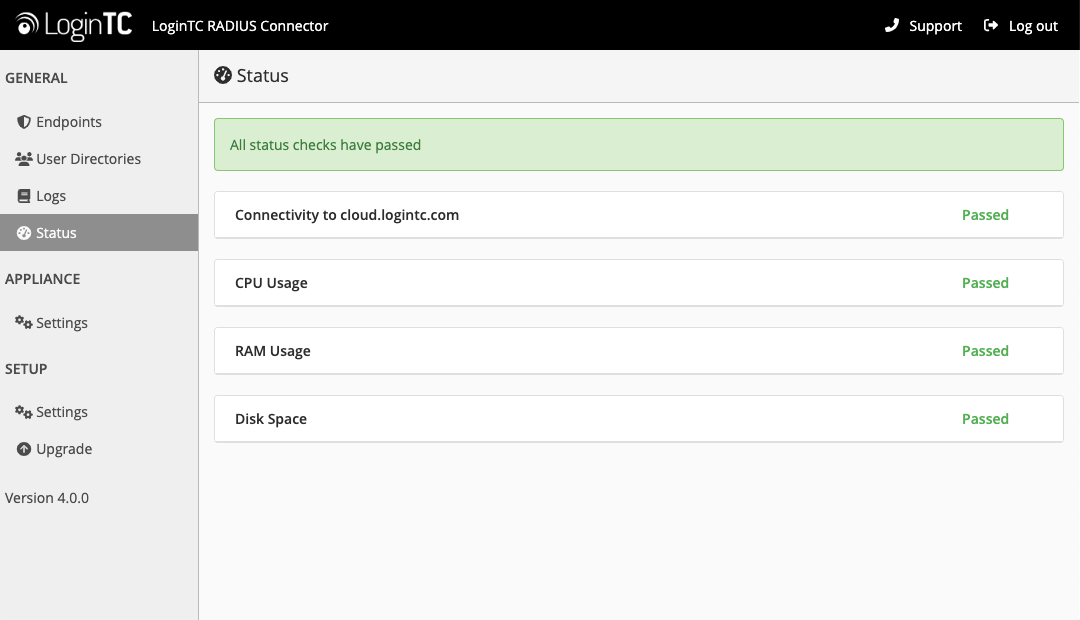
Ensure that all the status checks pass. For additional troubleshooting, click Logs:

Also make sure to check the secure logs on the Linux machine hosting SSH (/var/log/secure).
Email Support
For any additional help please email support@cyphercor.com. Expect a speedy reply.
From 4.X
The latest LoginTC RADIUS Connector upgrade package can be downloaded here: Download RADIUS Connector (Upgrade)- Navigate to SETUP > Upgrade:
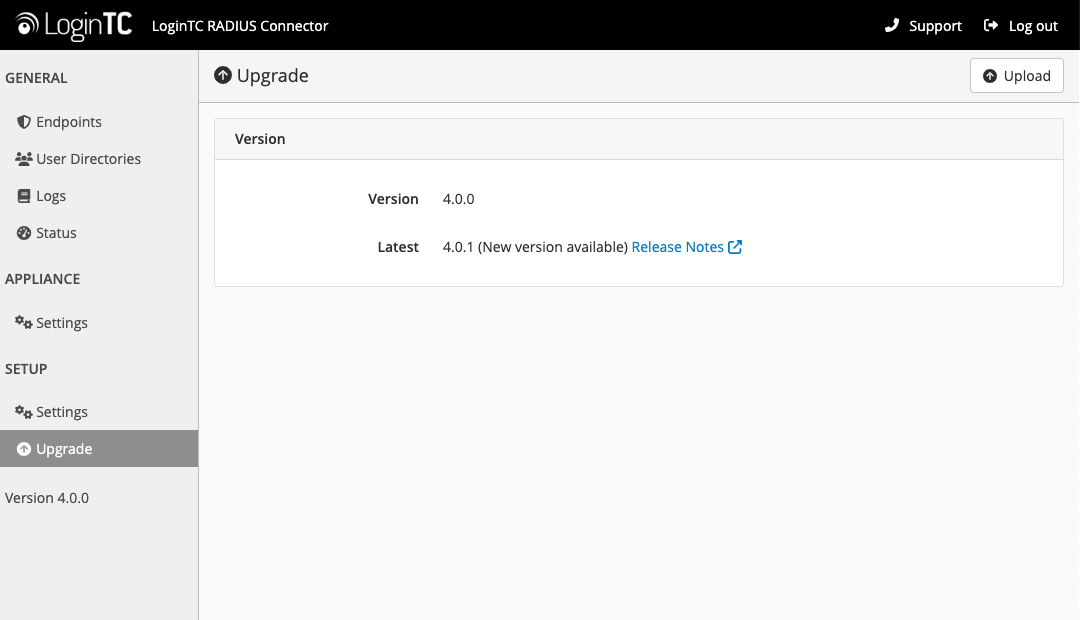
- Click Upload and select your LoginTC RADIUS Connector upgrade file:
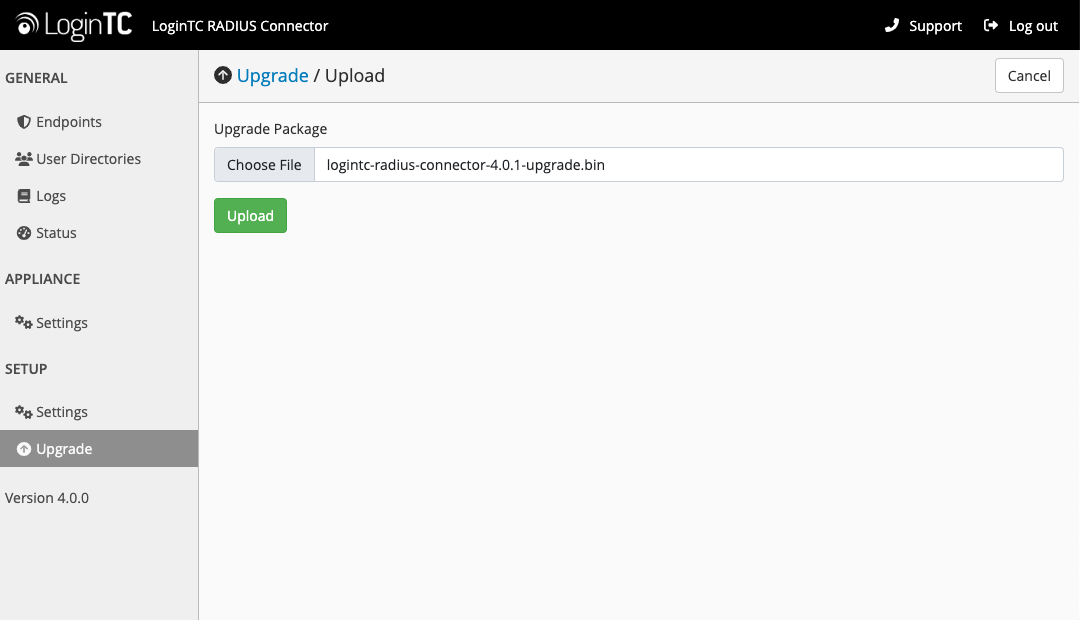
- Click Upload and do not navigate away from the page:
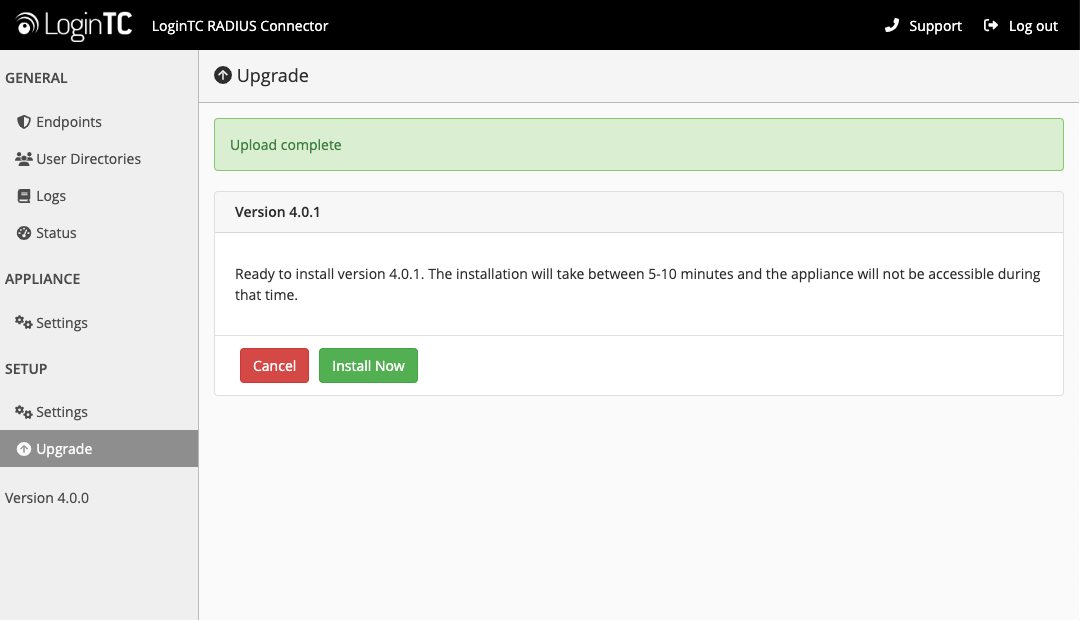
- Once upload is complete upgrade by clicking Install Now:
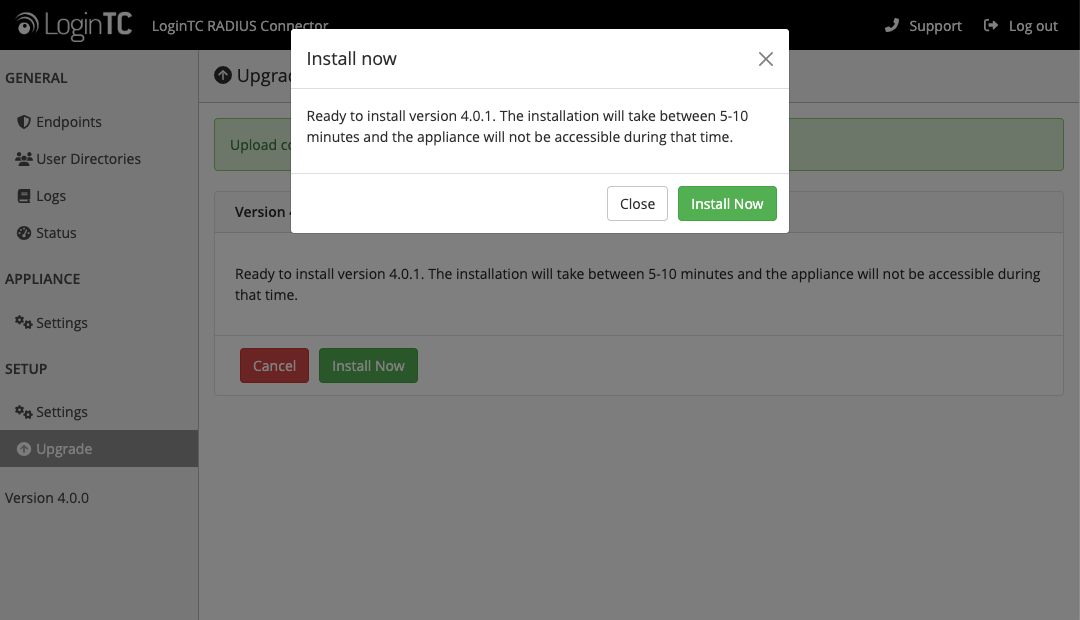
- Wait 10-15 minutes for upgrade to complete:
NOTE: Upgrade time
Upgrade can take 10-15 minutes, please be patient.
From 3.X
Important: LoginTC RADIUS Connector 3.X End-of-life
The LoginTC RADIUS Connector 3.X virtual appliance is built with CentOS 7.9. CentOS 7.X is End of Lifetime (EOL) June 30th, 2024. Although the appliance will still function it will no longer receive updates and nor will it be officially supported.
New LoginTC RADIUS Connector 4.X
A new LoginTC RADIUS Connector 4.X virtual appliance has been created. The Operating System will be supported for many years. Inline upgrade is not supported. As a result upgrade is deploying a new appliance. The appliance has been significantly revamped and although the underlying functionality is identical, it has many new features to take advantage of.
Complete 3.X to 4.X upgrade guide: LoginTC RADIUS Connector Upgrade Guide