How to deploy MFA for Microsoft Exchange Server On-Premises
August 12, 2025 •
As cyberattacks targeting email systems grow in sophistication, organizations running Microsoft Exchange Server on-premises are increasingly looking to implement multi-factor authentication (MFA) to protect sensitive communications, accounts, and administrative access.
Whether you’re hosting Exchange in a regulated environment, repatriating infrastructure from the cloud, or simply looking to close critical security gaps, you can deploy MFA for your Exchange environment on your terms.
Below are three real-world scenarios where organizations have successfully implemented MFA for Exchange Server.
Scenario 1: Securing Outlook Web App (OWA) Access
An accounting firm’s legal team frequently accessed email remotely via Outlook Web App (OWA). After a phishing attack exposed credentials, the organization sought a simple way to add MFA to OWA access without moving to Microsoft 365 or relying on third-party email gateways.
Solution: AD FS integration with Push Number Matching
MFA was integrated directly into Outlook Web App (OWA) using the LoginTC OWA Connector. After users entered their AD password via the OWA login page, they’re then challenged with an MFA request.
Since all the employees at the accounting firm have a company-issued smartphone, the IT team implemented Push Number Matching authentication to use with OWA.
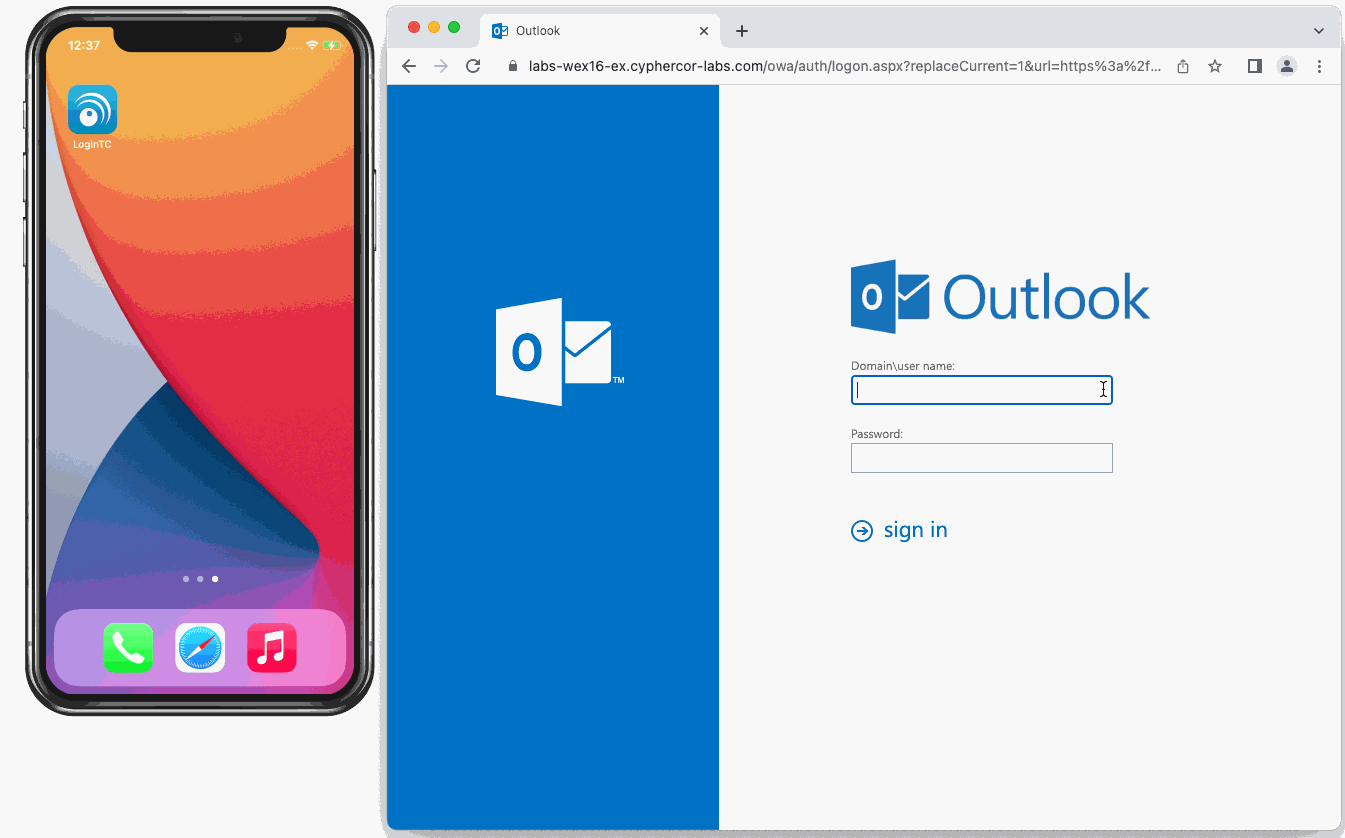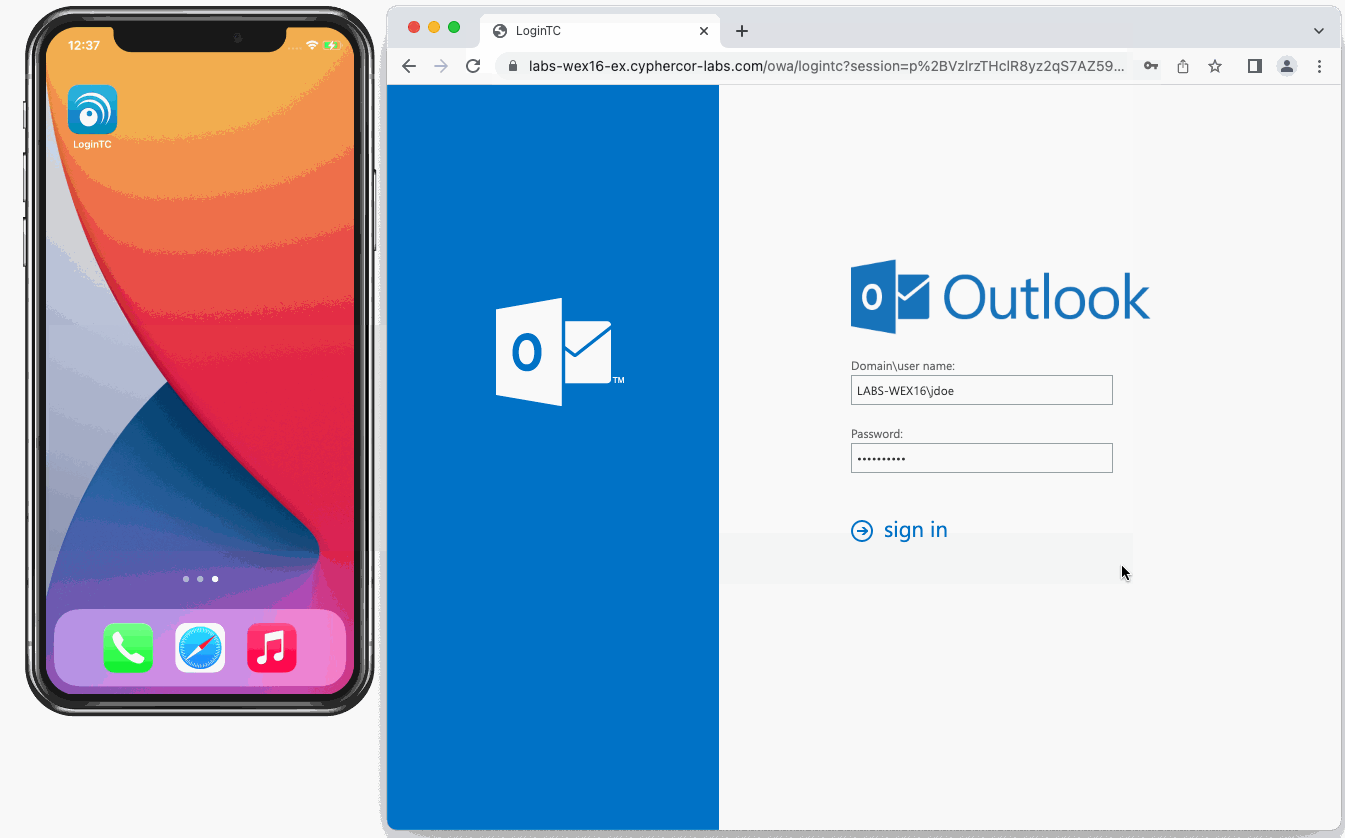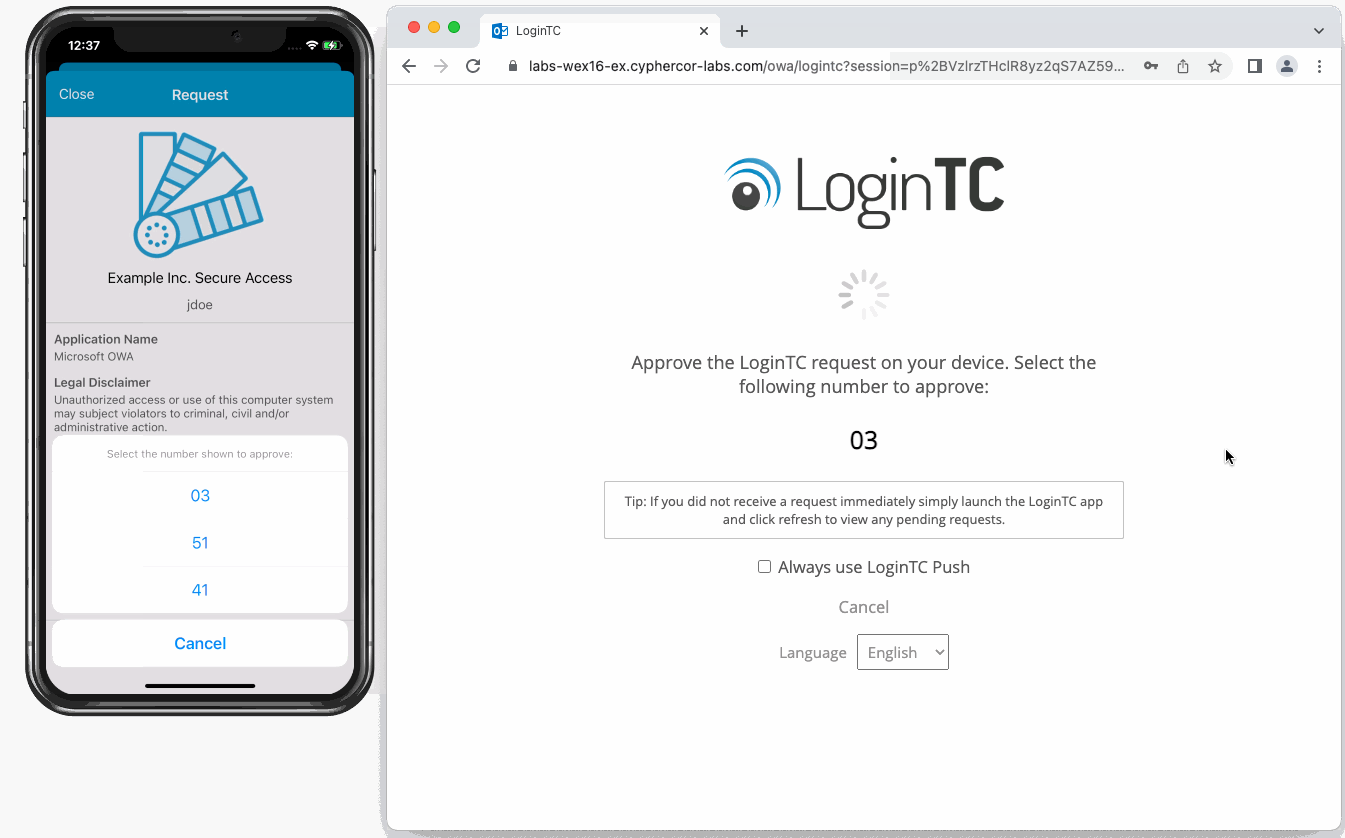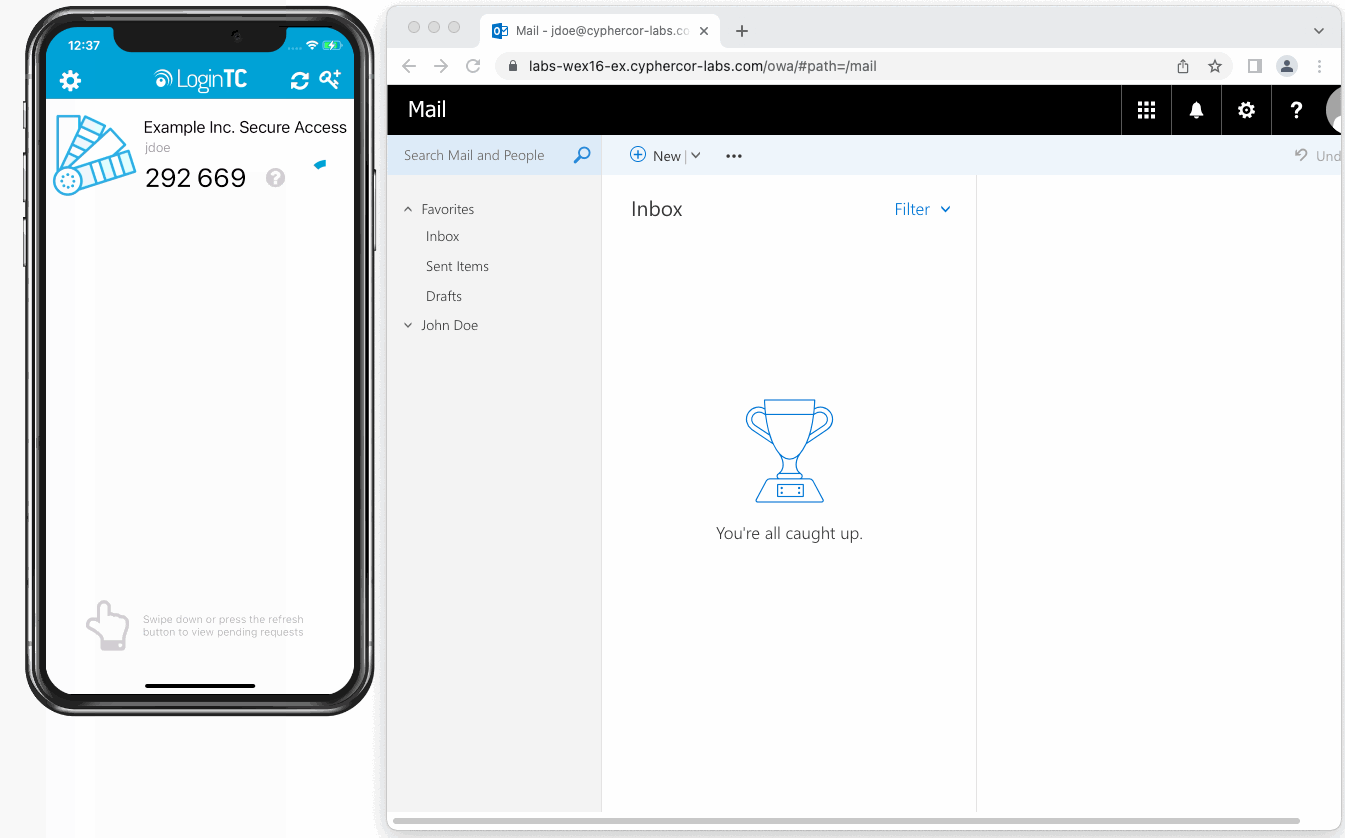
This approach required zero changes to the existing Exchange configuration, ensuring a smooth deployment with minimal disruption. End users enjoyed a seamless login experience through their browser, while administrators retained full compatibility with both Exchange 2016 and 2019. Most importantly, the organization maintained complete control over its identity infrastructure, keeping all authentication processes in-house.
Scenario 2: MFA for Exchange Admin Center (EAC) in a Hybrid Setup
A municipal government’s IT department had configured Exchange Hybrid to support both on-prem and Microsoft 365 mailboxes. However, the Exchange Admin Center (EAC) was still hosted on-prem and only protected by single-factor AD credentials, posing a major risk if exposed.
Solution: Hybrid MFA with FIDO2 Security Keys
MFA was enabled for EAC via the same AD FS integration, ensuring administrators were prompted for a second factor when accessing the admin portal.
The IT department issued FIDO2 security keys to all employees with administrator access to the EAC, ensuring the most secure, phishing-resistant authentication possible.
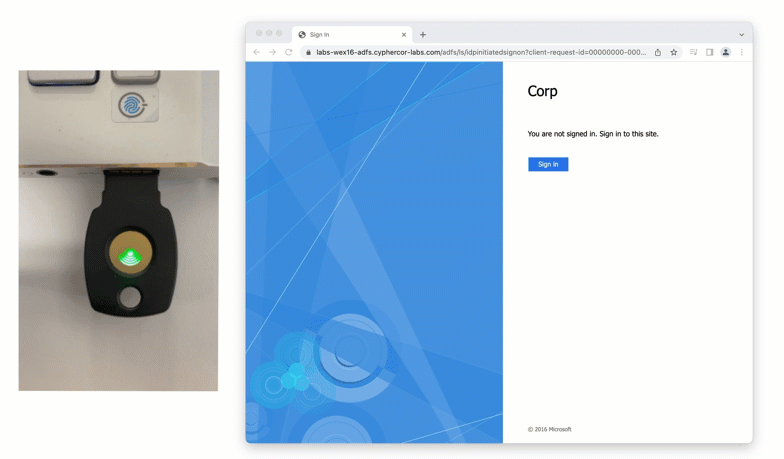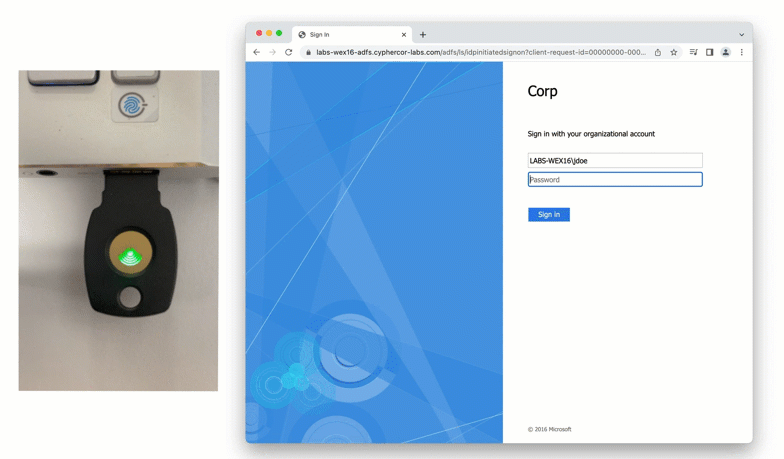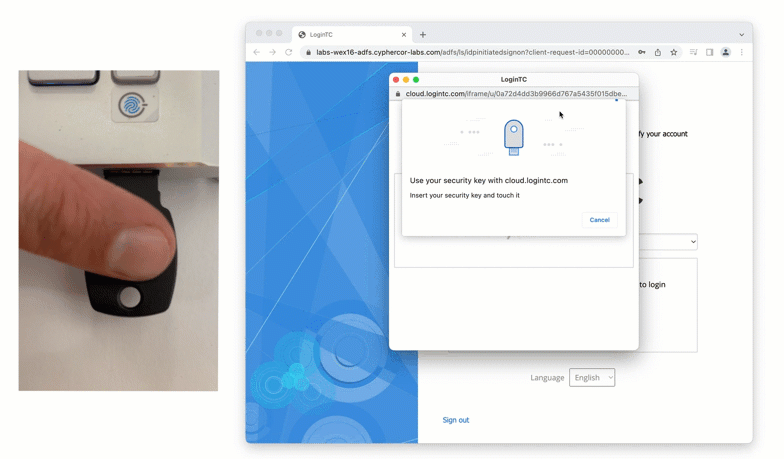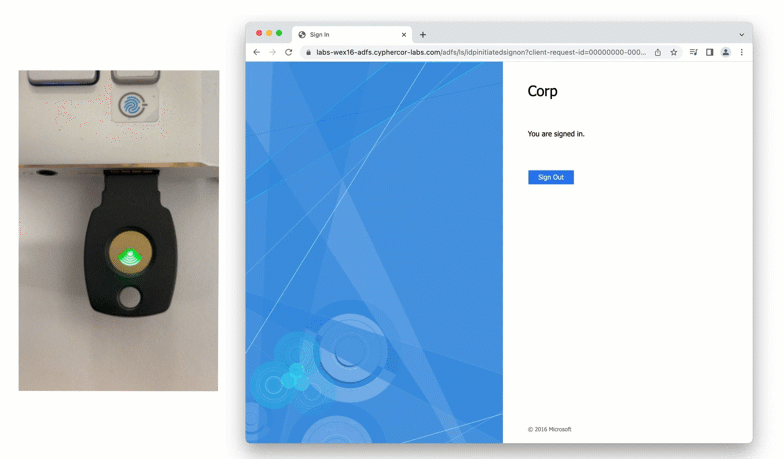
The solution delivered unified MFA coverage for both Exchange and Office 365 access, simplifying administration and ensuring consistent security across platforms. Administrators could choose from strong authentication methods that suited their preferences and operational requirements, all without the need for costly third-party cloud brokers or gateways.
Scenario 3: Air-Gapped Network with On-Prem Exchange
A utility company operating critical infrastructure ran a completely air-gapped network, including its Exchange mail system and Active Directory. No internet-based MFA solution could be used and security policies mandated two-factor authentication for all administrative access.
Solution: On-Premises MFA with Passcode Grid
MFA was deployed using LoginTC Managed, a fully on-prem MFA platform. Offline-capable passcode grid authentication was distributed to Exchange admins, enabling simple, no additional cost, no-hardware needed authentication directly within the secure environment.
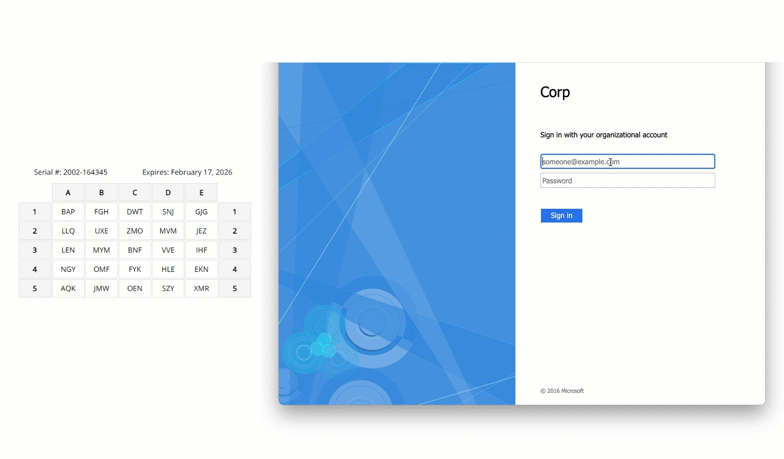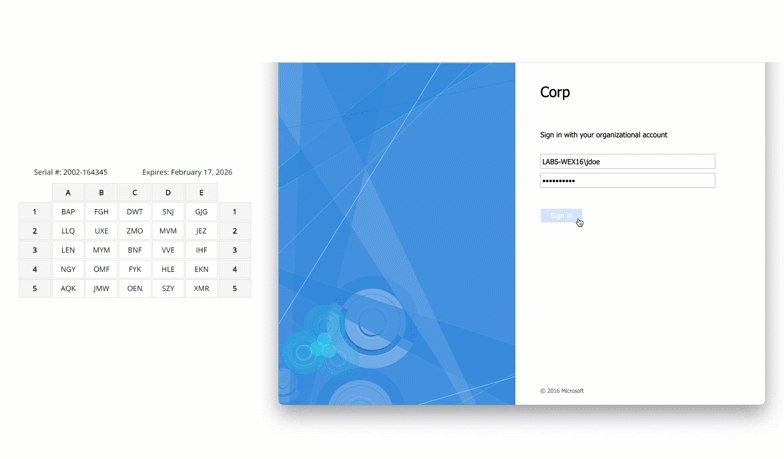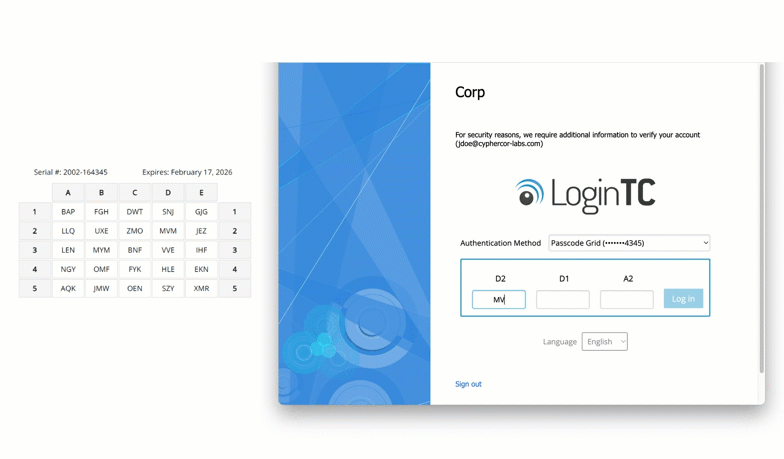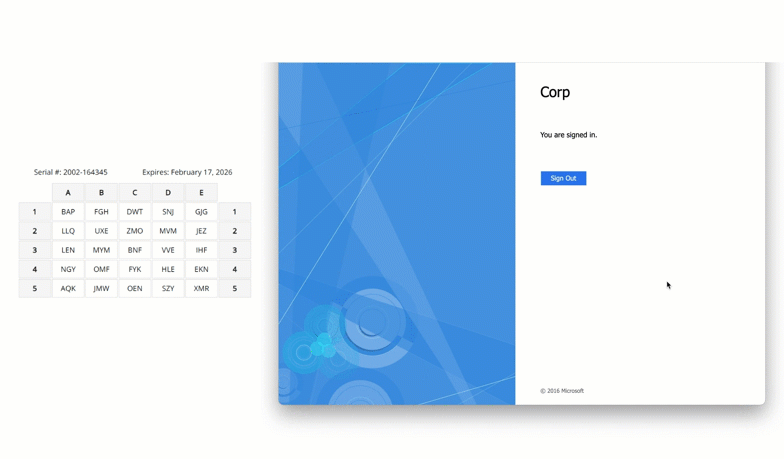
The deployment operated fully offline with no internet dependencies, ensuring maximum isolation from external threats. All MFA services were hosted entirely within the organization’s private network, and both Exchange and Active Directory remained untouched from a configuration standpoint, preserving the integrity of the existing environment.
What You’ll Need to Get Started
To deploy MFA for Microsoft Exchange Server on-premises with LoginTC, you’ll typically need:
- Microsoft Active Directory
- AD FS configured for federated authentication
- A LoginTC account
- LoginTC AD FS Connector (software download)
- Optional: LoginTC Managed for fully offline or air-gapped environments
Prefer to watch a video? Check out our install video for integrating AD FS with LoginTC MFA
Reach out to us to get started.
MFA for Exchange without the cloud
Whether your organization is managing sensitive government communications, running a hybrid Microsoft 365 environment, or protecting critical infrastructure in a disconnected network, LoginTC delivers flexible, secure MFA tailored to Microsoft Exchange Server on-premises.
No cloud dependency required, it works with Exchange 2016, 2019, and hybrid setups and is simple for users, while being strong for security teams.
To learn more about MFA for Microsoft Exchange On-Premises, continue reading below.
Overview of Microsoft Exchange On-Premises Security Risks
Microsoft Exchange On-Premises is a widely utilized email and calendaring server that organizations of all sizes depend on for their daily communication needs. However, its popularity makes it a significant target for cyber attackers. The risks associated with Exchange On-Premises primarily stem from its accessibility and the valuable data it processes. Unpatched vulnerabilities, phishing attacks, and brute-force attempts are common threats that can compromise the integrity of an Exchange server. These risks are exacerbated by the fact that email is a primary vector for malware distribution and credential theft.
In recent years, several high-profile breaches have highlighted the importance of securing Exchange On-Premises environments. Attackers have exploited zero-day vulnerabilities, gained unauthorized access to sensitive information, and disrupted business operations. The implications of such breaches are far-reaching, including financial losses, reputational damage, and legal repercussions. Organizations can no longer rely solely on traditional security measures, such as firewalls and antivirus software, to protect their email systems.
To effectively mitigate these risks, a multi-layered security approach is essential. One of the most effective strategies is implementing Multi-Factor Authentication (MFA). MFA adds an extra layer of security by requiring users to provide multiple forms of verification before accessing their accounts. This significantly reduces the likelihood of unauthorized access, even if an attacker obtains a user’s password. By understanding the specific security risks associated with Exchange On-Premises and the limitations of traditional measures, organizations can better appreciate the value of MFA in fortifying their defenses.
What is Multi-Factor Authentication (MFA)
Multi-Factor Authentication (MFA) is a security mechanism that requires users to present two or more independent credentials to verify their identity. These credentials fall into three categories: something you know (e.g., a password or PIN), something you have (e.g., a smartphone or hardware token), and something you are (e.g., a fingerprint or facial recognition). By combining multiple factors, MFA provides a higher level of assurance that the person attempting to access a system is indeed who they claim to be.
The concept of MFA is not new, but its adoption has accelerated in response to the increasing frequency and sophistication of cyber attacks. Traditional single-factor authentication, which relies solely on a password, is vulnerable to various attacks, including phishing, brute-force, and credential stuffing. MFA addresses these vulnerabilities by adding layers that are more difficult for attackers to bypass. For example, even if a cybercriminal manages to steal a user’s password, they would still need access to the second factor (e.g., a one-time code sent to the user’s phone) to gain entry.
Implementing MFA involves integrating additional verification steps into the authentication process. These steps can vary depending on the organization’s needs and the tools available. Common MFA methods include SMS-based verification, authenticator apps, hardware tokens, and biometric verification. Each method has its strengths and weaknesses, and choosing the right combination of factors is crucial for achieving a balance between security and user convenience. Understanding the fundamentals of MFA is the first step toward leveraging its benefits to protect your Microsoft Exchange On-Premises environment.
Importance of MFA for Microsoft Exchange On-Premises
The importance of implementing MFA for Microsoft Exchange On-Premises cannot be overstated. Exchange servers are treasure troves of sensitive information, including emails, contacts, and calendar data, making them prime targets for cybercriminals. Without adequate security measures, unauthorized access to this data can lead to severe consequences such as data breaches, intellectual property theft, and compromised business communications. MFA acts as a critical line of defense, significantly reducing the risk of such incidents.
One of the primary reasons MFA is vital for Exchange On-Premises is its ability to protect against credential-based attacks. Passwords alone are no longer sufficient to safeguard accounts, as they can be easily compromised through various means. MFA mitigates this risk by requiring an additional verification factor, making it exponentially harder for attackers to gain unauthorized access. This added layer of security is especially crucial for administrators and users with elevated privileges, who are often targeted by attackers due to their access to sensitive information.
Moreover, regulatory compliance is another compelling reason to implement MFA. Many industries are subject to stringent data protection regulations that mandate the use of robust security measures to protect sensitive information. Implementing MFA helps organizations meet these requirements and avoid potential fines and penalties. Additionally, MFA enhances overall security posture, fostering trust among clients, partners, and stakeholders by demonstrating a commitment to safeguarding their data. In today’s threat landscape, the importance of MFA for Microsoft Exchange On-Premises cannot be ignored, as it plays a pivotal role in ensuring the security and integrity of your email system.
Steps to Prepare for MFA Implementation
Before diving into the technical aspects of implementing MFA for Microsoft Exchange On-Premises, it is essential to prepare adequately to ensure a smooth and effective deployment. The preparation phase involves several critical steps, including assessing your current security posture, identifying stakeholders, and selecting the appropriate MFA solution. By taking a methodical approach, you can address potential challenges and set the stage for a successful implementation.
The first step in preparing for MFA implementation is to conduct a thorough assessment of your existing security measures and identify any gaps that MFA can address. This assessment should include an inventory of all user accounts, their access levels, and the current authentication methods in place. Understanding the specific needs and vulnerabilities of your organization will help you tailor the MFA solution to your unique requirements. Additionally, this assessment can highlight areas where additional security measures may be needed, ensuring a comprehensive approach to safeguarding your Exchange On-Premises environment.
Next, it is crucial to identify and engage key stakeholders who will be impacted by the MFA implementation. This includes IT administrators, security teams, and end-users. Communicating the importance of MFA and the benefits it brings can help garner support and cooperation from all parties involved. Stakeholders should be informed about the changes in the authentication process, the rationale behind them, and the steps they need to take to comply with the new security protocols. Providing clear and consistent communication can alleviate concerns and facilitate a smoother transition.
Finally, selecting the right MFA solution and methods is a critical decision that can significantly impact the success of your implementation. There are various MFA methods available, each with its advantages and limitations. Consider factors such as ease of use, compatibility with your existing infrastructure, and the level of security provided. It is also essential to evaluate the scalability of the solution to ensure it can accommodate future growth and evolving security needs. By carefully preparing and addressing these key considerations, you can lay a solid foundation for a successful MFA implementation for Microsoft Exchange On-Premises.
Configuring MFA in Microsoft Exchange On-Premises
Configuring MFA for Microsoft Exchange On-Premises involves a series of technical steps that require careful planning and execution. The process begins with selecting an MFA solution that integrates seamlessly with your Exchange environment. Microsoft offers several options for implementing MFA, including utilizing Azure MFA, third-party solutions, or on-premises MFA servers. Each option has its own setup requirements and configuration steps, so it is essential to choose the one that best aligns with your organization’s needs and capabilities.
Once you have selected your MFA solution, the next step is to configure the necessary infrastructure and settings to enable MFA for your Exchange On-Premises environment. This typically involves installing and configuring the MFA server or service, integrating it with your Active Directory, and setting up the required policies and authentication methods. For example, if you are using LoginTC MFA, you will need to configure your Active Directory settings to integrate with LoginTC, synchronize your on-premises Active Directory with LoginTC, and enable MFA for the desired user accounts. Detailed documentation and guides can assist you in navigating these configuration steps.
After configuring the infrastructure, it is crucial to test the MFA setup thoroughly to ensure it functions as expected. This includes verifying that the MFA prompts are triggered correctly during the authentication process, checking that the selected authentication methods work seamlessly, and ensuring that users can complete the MFA steps without issues. Conducting pilot tests with a small group of users can help identify and resolve any potential problems before rolling out MFA to the entire organization. Additionally, it is important to establish a support plan to assist users who may encounter difficulties during the initial implementation phase. By following these steps and addressing any challenges that arise, you can successfully configure MFA for Microsoft Exchange On-Premises and enhance your organization’s email security.