Use hardware tokens offline and restrict bypass code settings in LoginTC’s newest product update
February 29, 2024 •
The latest product update from LoginTC offers a new offline authentication method, and gives Super Administrators more control over bypass code settings.
Building on our previous product update, which improved the management of FIDO2 tokens and Passcode Grid, LoginTC continues to build features that put control back in the hands of administrators.
Keep reading to learn all about this latest update.
Hardware Tokens offline
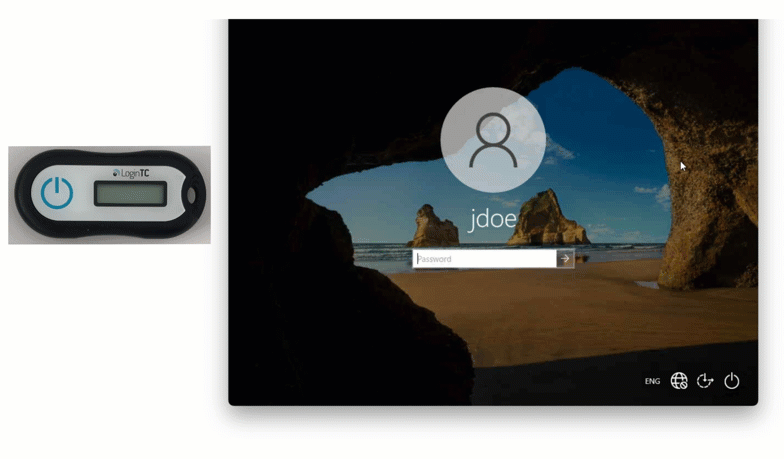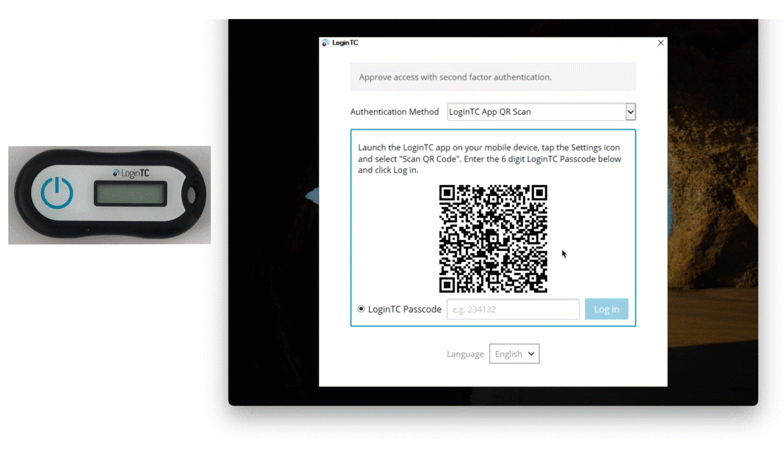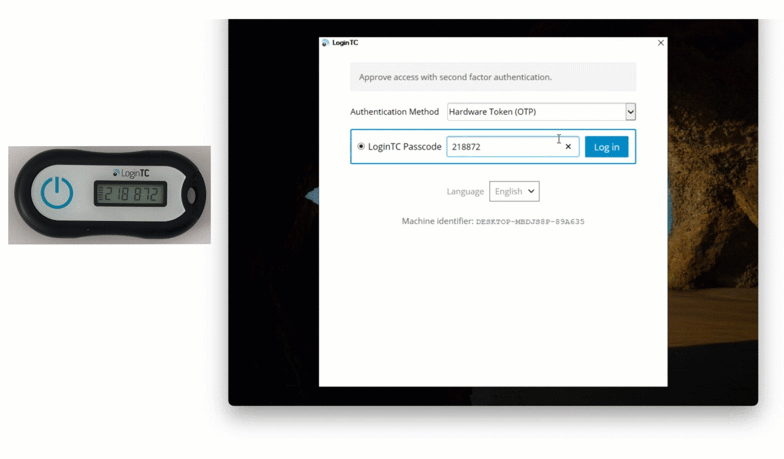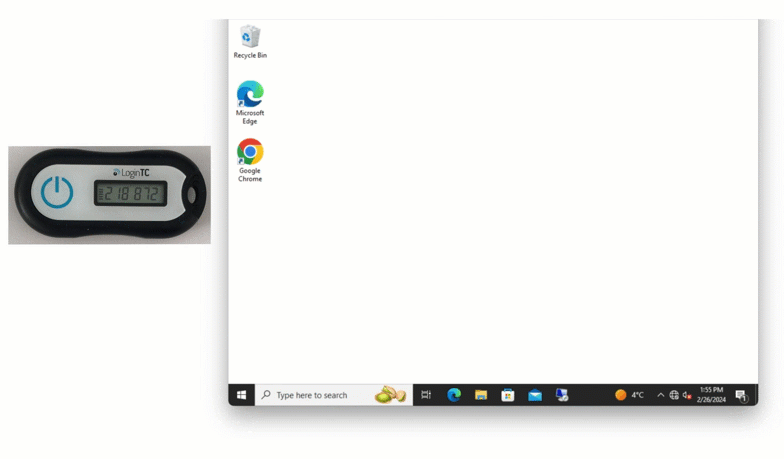
LoginTC Administrators can now leverage an additional authentication method offline: Hardware Tokens.
How it works
If your users need to securely login to Windows Logon or RDP, you can’t always rely on an authentication method that needs external communication with the internet.
That’s where offline authentication comes in handy.
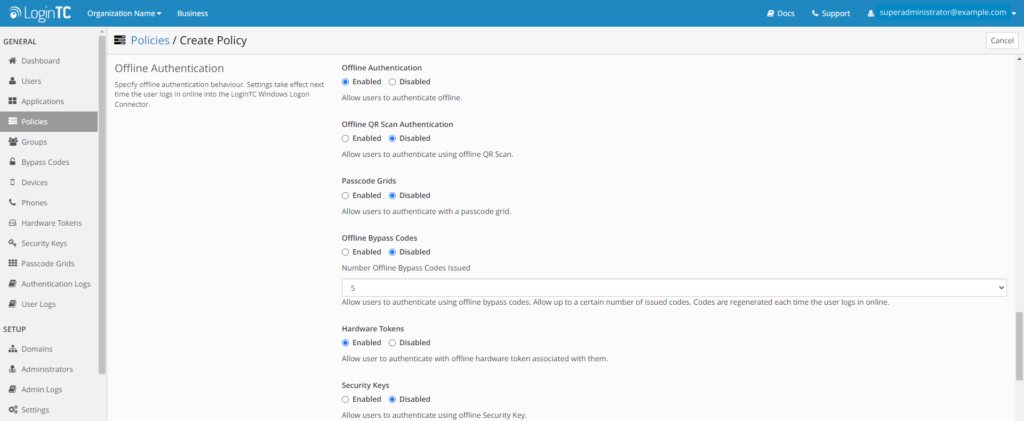
Offline authentication allows users to login to Windows with MFA before they connect to the internet. LoginTC allows administrators to choose from a variety of offline authentication methods, including Security Key, QR Scan, Passcode Grid, and now Hardware Token.
Hardware token authentication allows users to generate one time passcodes on a physical device. This method is simple for end users, cost-effective for organizations, and with the new offline capabilities, offers comprehensive coverage for all your services and applications.
Offline and On-premises
With this latest update, offline Hardware Token authentication is also available in our on-premises product, LoginTC Managed.
LoginTC Managed offers administrators full control over their MFA operations. There are six available authentication methods, five of which can be leveraged for offline authentication.
Learn more about on-premises MFA
Bypass Code Settings
Our latest product update also includes a new security feature for Super Administrators called Bypass Code Settings.
Bypass Codes are an authentication method that allows for emergency authentication in specific cases. They are an excellent tool to keep end users logged in and productive when all other authentication methods have failed. Super Administrators, Account Managers, and Help Desk Administrators are able to generate bypass codes for users in LoginTC.
Learn more about administrator roles in LoginTC
In response to customer feedback, LoginTC has introduced the ability for Super Administrators to limit the bypass code settings for codes created by Account Managers and Help Desk Administrators.
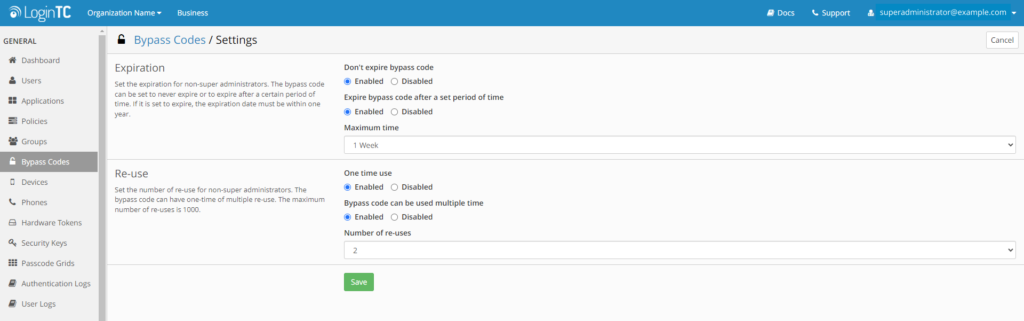
Super Administrators now see a Settings button in the top right corner of the Bypass Codes page. From there they can choose whether to set a Maximum expiration time and Maximum number of reuses of bypass codes created by Account Managers and Help Desk Administrators.
In the example below, the Super Administrator has set the bypass codes settings to a maximum one week expiration time, and the number of reuses to 2.
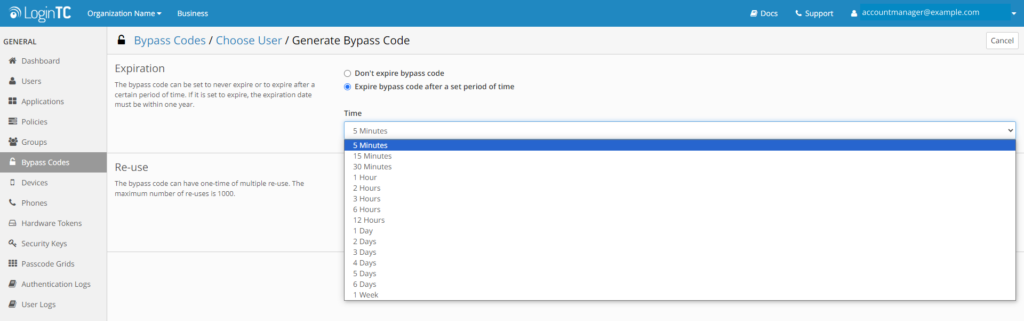
Now as an Account Manager in the same organization, when creating a bypass code for a user, 1 Week is the maximum amount of time available to select, and if multiple use is enabled, the maximum number of reuses can only be set to 2.
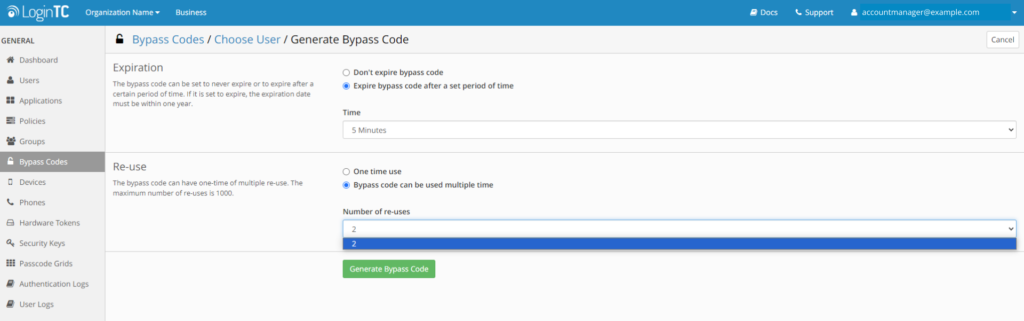
This gives Super Administrators greater oversight over the settings that bypass codes are being created with, ensuring that this useful tool doesn’t become misused.
Stay tuned for more
LoginTC Administrators can take advantage of these newest product updates right away in the LoginTC Admin Panel.
There’s lots more to come from LoginTC, including more security features and new authentication methods. If you want to see how LoginTC can improve the security of your organization, start a free trial today.