The Ultimate Guide to MFA for Cyber Essentials Certification
November 07, 2023 •

Introduction
The Cyber Essentials Certification is a comprehensive program for businesses who want to improve their cybersecurity posture. As with recent updates to data privacy legislation, the requirements of the Cyber Essentials Certification can be confusing, especially when it comes to the specifics of cybersecurity tools and technology required to meet the certification.
In this blog post, we break down the specific requirements in the Cyber Essentials Certificate related to Multi-factor Authentication (MFA). We’ll unpack why this requirement has been introduced, what types of MFA meet the certification standards, and other MFA considerations to think through.
Let’s dive in!
What is the Cyber Essentials Certification?
The Cyber Essentials certification is a cybersecurity program run by the government of the United Kingdom. It helps businesses in the UK and around the world become more cyber secure.

Organizations can complete the certification program by following all the requirements and then completing a self-assessment. Alternatively, with Cyber Essentials Plus, organizations are audited by a cybersecurity expert to ensure requirements are correctly followed.
A Cyber Essentials Certificate is required for organizations to bid on UK Government contracts. Additionally, it can help you better understand your organization’s risk level. A Cyber Essentials certificate can also set your business apart from competitors, and make your business more trustworthy.
What are the MFA requirements for Cyber Essentials Certification?
Version 3 of the Cyber Essentials program, which came fully into effect in April 2023, includes requirements for implementing Multi-factor Authentication (MFA) in your organization.
As a refresher, MFA requires users to provide more than one identity factor when logging into an account. There are three identity dimensions:
- Something you know (like a password);
- Something you have (such as a physical token);
- Something you are (biometric information, for example, a fingerprint).
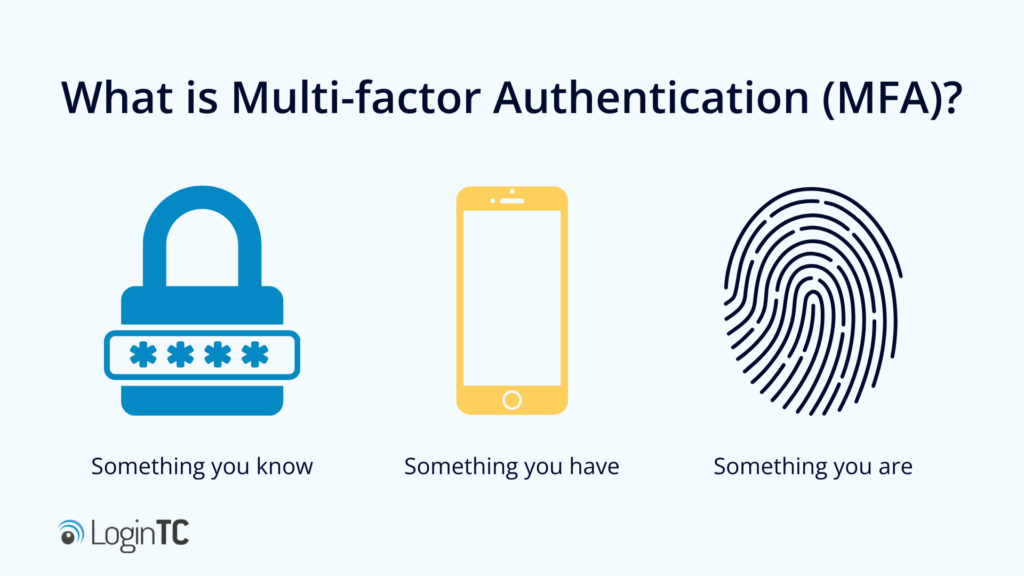
By combining two or more of these identity dimensions, authentication is made significantly more secure than when only using a password.
The Cyber Essentials Certification requires MFA under the following circumstances:
As well as providing an extra layer of security for passwords that aren’t protected by the other technical controls, you should always use multi-factor authentication to give administrative accounts extra security, and accounts that are accessible from the internet.
The requirement also includes a minimum password length provision, if a password is used as one of the identity dimensions. Passwords must be at least 8 characters, with no limit on their maximum length.
Why has MFA been introduced as a requirement for Cyber Essentials Certification?
With the increasing frequency and sophistication of cyber attacks, passwords — even strong ones — simply aren’t enough to keep out attackers. With every data breach, more passwords are leaked, making it easier for attackers to brute-force accounts, and use stolen credentials to break into systems.
Adding more than one identity dimension to logins ensures that passwords are not your last line of defense. Like we discussed in a previous blog post about the problem with passwords, a hacker might be able to steal a million passwords, but it’s useless if they don’t also steal the corresponding smartphones used for authentication.
Cyber Essentials Authentication Methods
The Cyber Essentials guidelines recommend administrators consider four types of authentication methods to provide the second identity dimension. Below, we’ll break down these four categories of authentication methods, including some practical examples of each.

1. Managed devices
One way to enforce a second factor of authentication is to require logins from exclusively managed devices. To implement this method of authentication, a user is assigned a specific device and a certificate is installed on that device to tie it directly to the user.
When logging into an online service, the program will first look for the verified certificate. If found, access will be granted. In this way, the certified device acts as the second factor of authentication. This is considered a form of Single-Sign-On authentication.
2. Authenticator apps
The second category of authentication method is to use an app on a trusted device for authentication. Authenticator apps can be downloaded onto a mobile device, tablet, or computer, and registered to a user. When a user inputs their first factor credentials, they’re prompted to input a six or eight digit code from the app on their registered device.
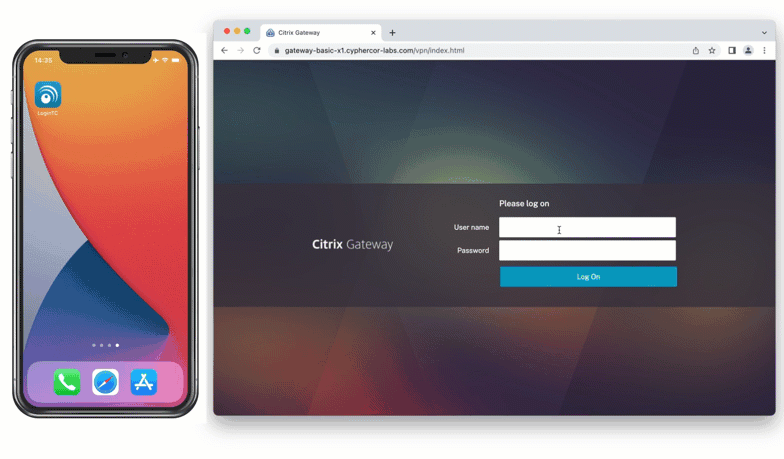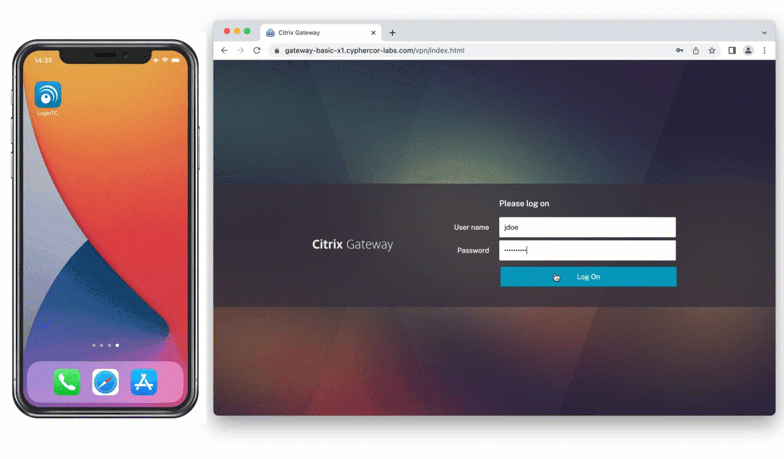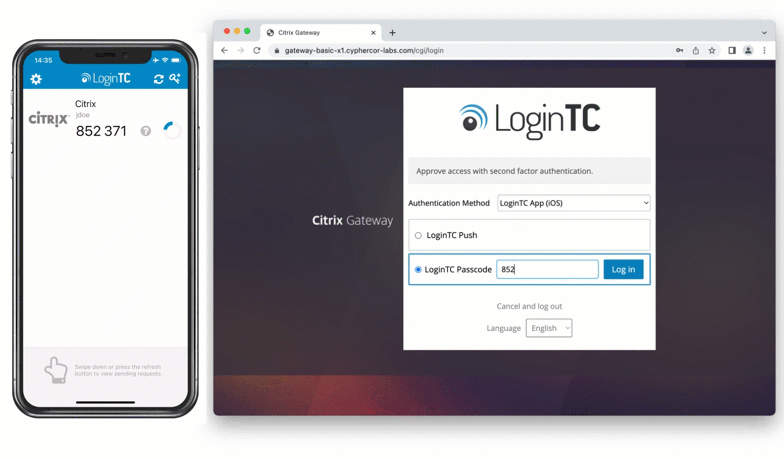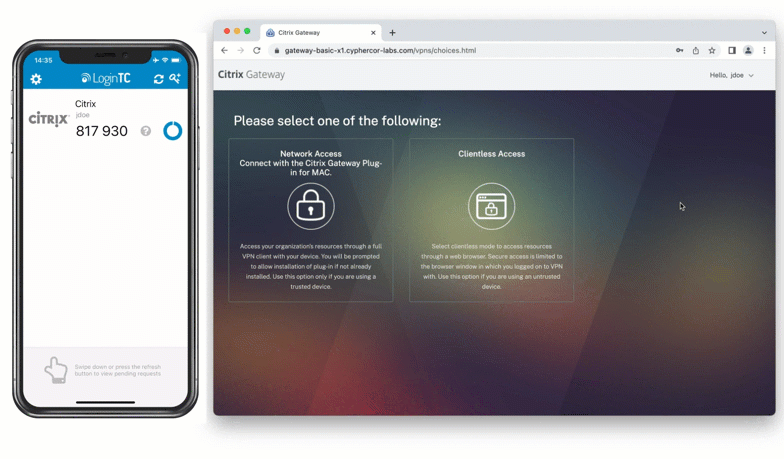
These codes are most commonly time-based, and devices receive new codes every 30 or 60 seconds.
Authenticator apps can also be used to leverage push authentication. After users input their first factor, a notification is sent to their registered device with a prompt to accept or deny authentication. Push authentication can be made more secure with number matching and requiring a pin or password to confirm login.
Authenticator apps are a good authentication option for organizations with BYOD policies in place, or where employees are given corporate devices.
3. Physical authentication tokens
Physical authentication tokens can come in many forms. An older but still secure form of physical authentication is the hardware token. Similar to an authenticator app, hardware tokens are registered to a specific user using unique seeds, and generate codes based on time.
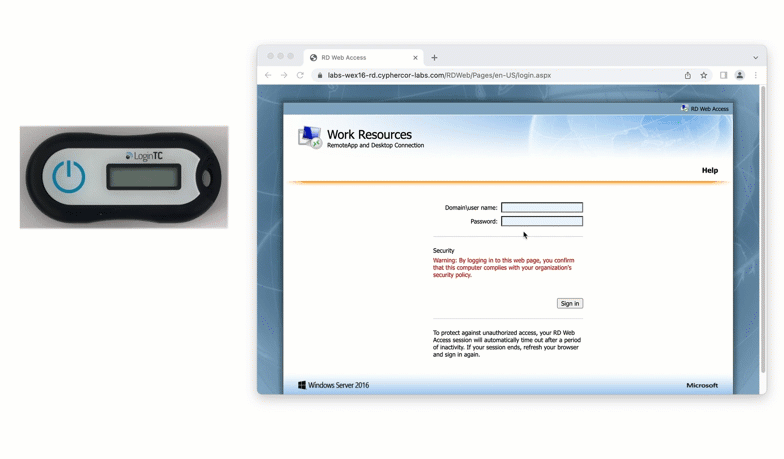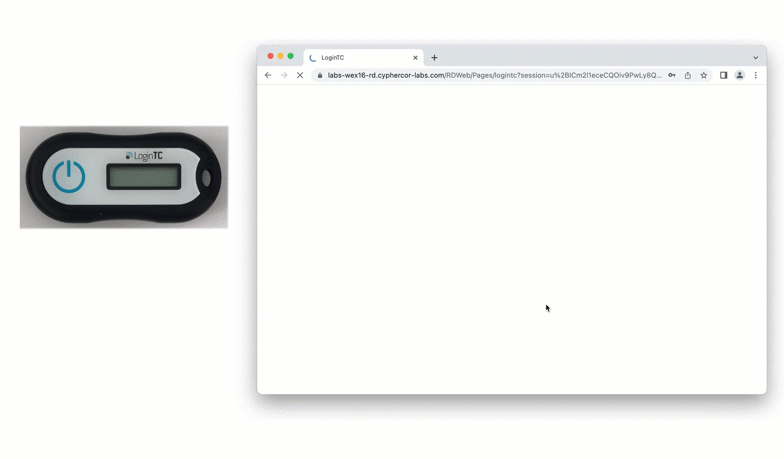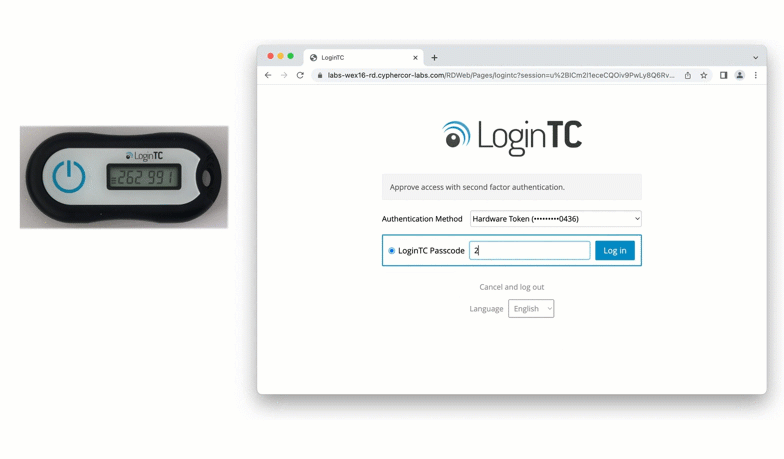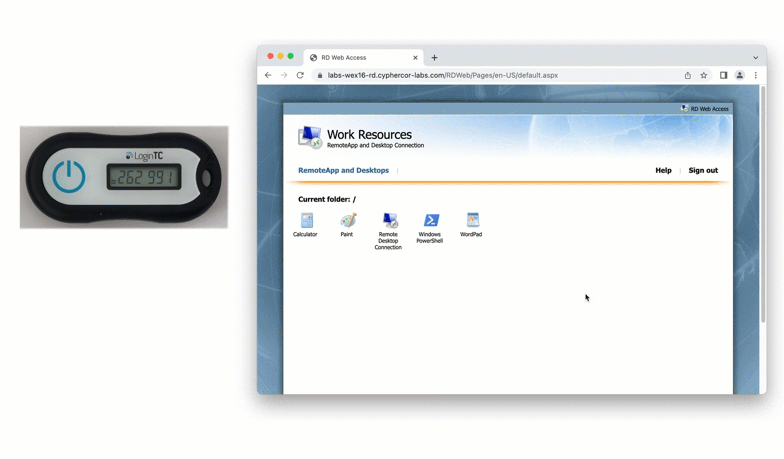
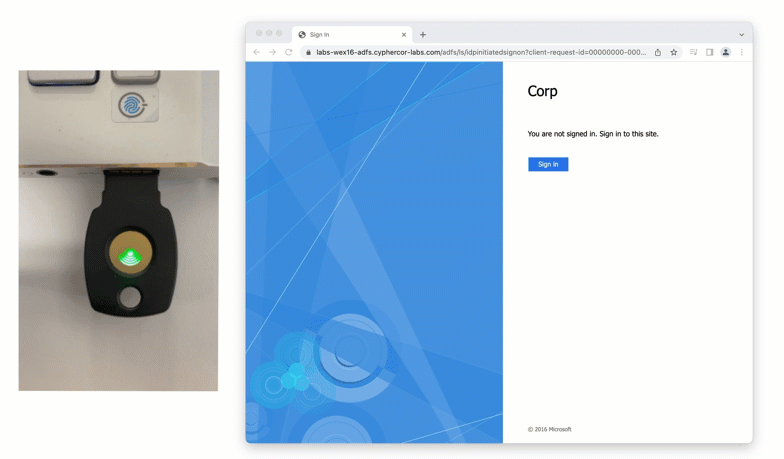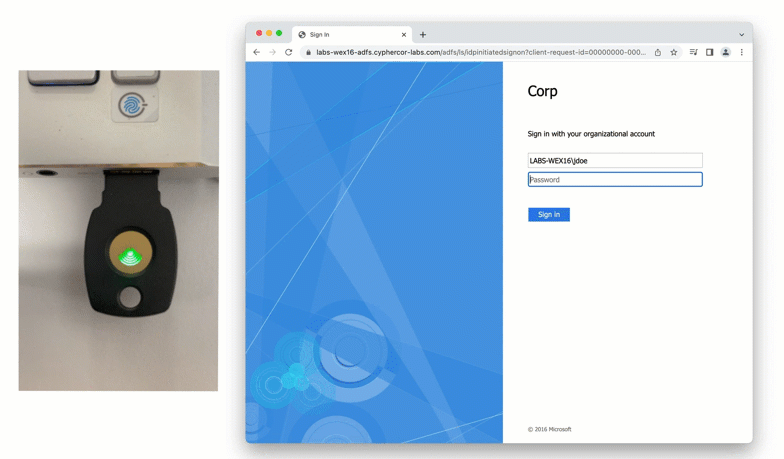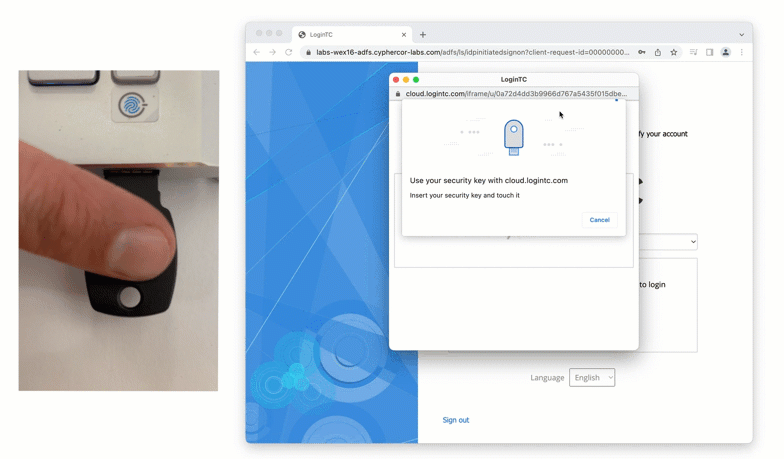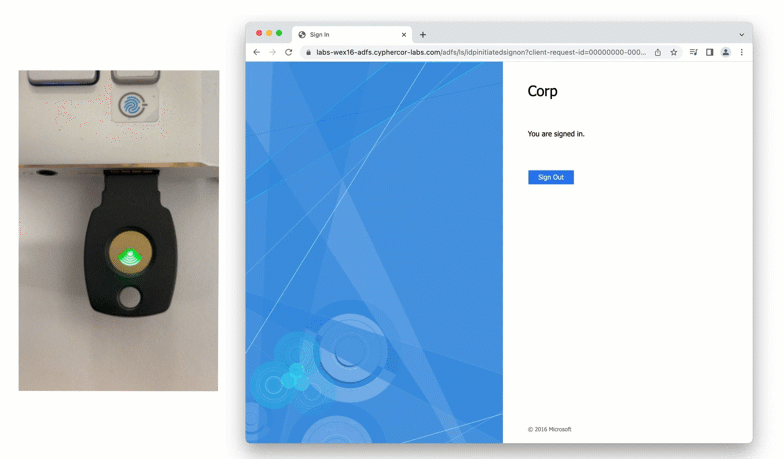
A newer form of a physical token is a FIDO2 token. FIDO2 tokens are considered “phishing-resistant” as they leverage domain certificates in a browser to confirm that a user is logging into the correct website, as well as authenticating the correct user account.
Another example of a physical authentication token is the passcode grid. A passcode grid is a 5×5 square grid containing 3 characters in each box. Each passcode grid is registered to a specific user. When prompted for second factor authentication, a user is asked to input the 3 characters in a series of boxes. Here is an example of a passcode grid authentication:
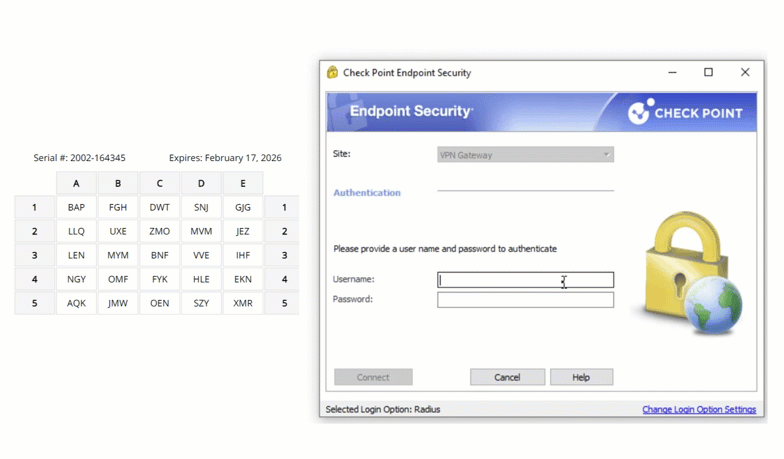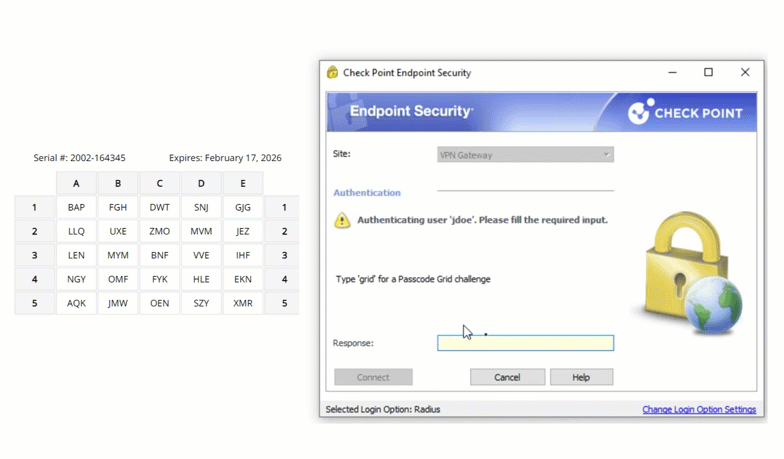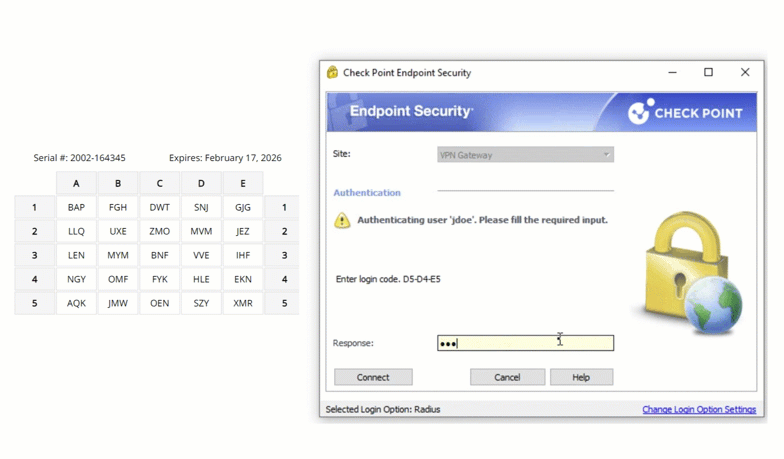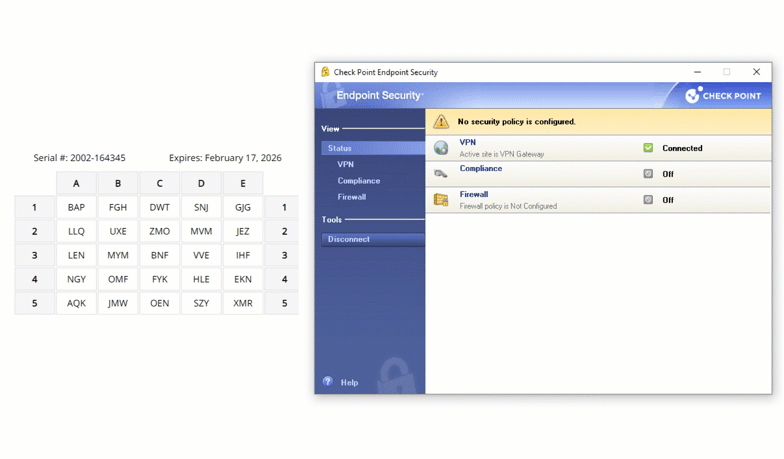
As seen in the animation, the user is asked for the characters in A5, B3, and C4. Providing the correct set of characters grants the user entry.
Lastly, a bypass code can also be considered a form of physical authentication. Bypass codes are generated upon registration or by an IT administrator and can provide access for a set amount of time to a user. Bypass codes are most commonly used as a back-up option if users are otherwise locked out of their account.
4. Trusted account authentication
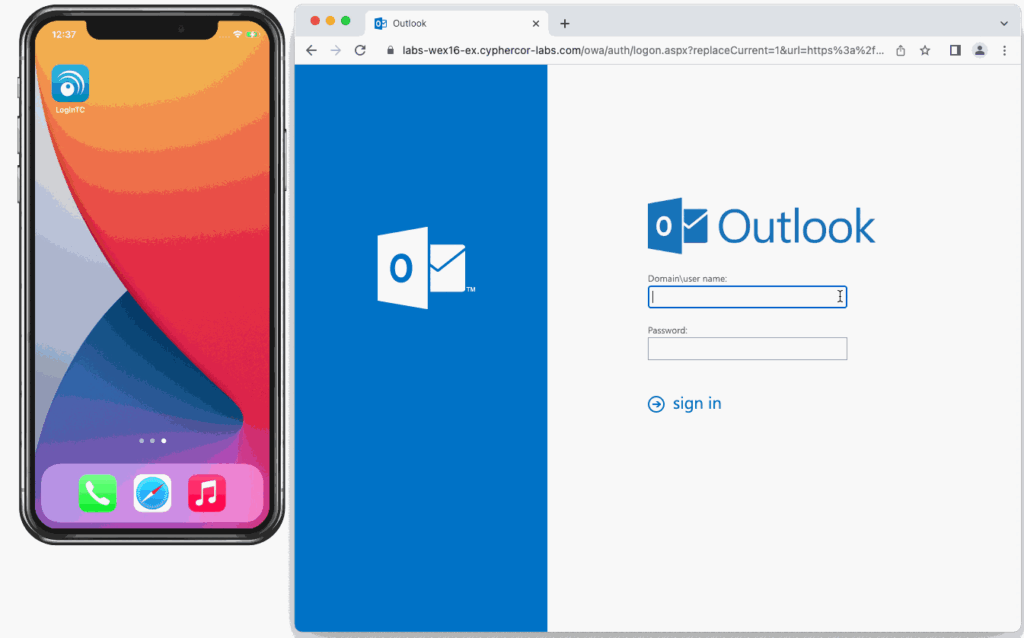
Trusted account authentication allows you to receive a code or login link to an existing trusted account. The most popular forms of this method are email, SMS, and phone call authentication.
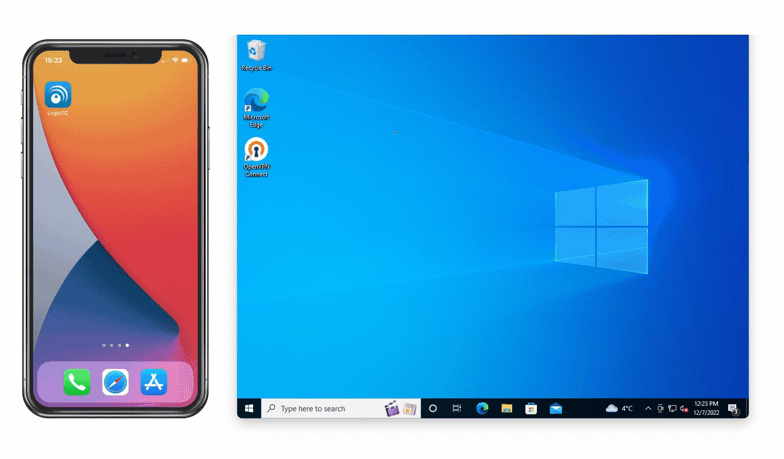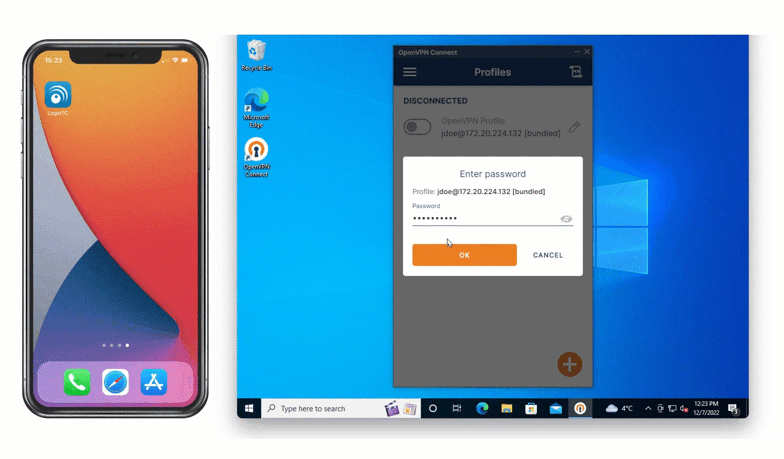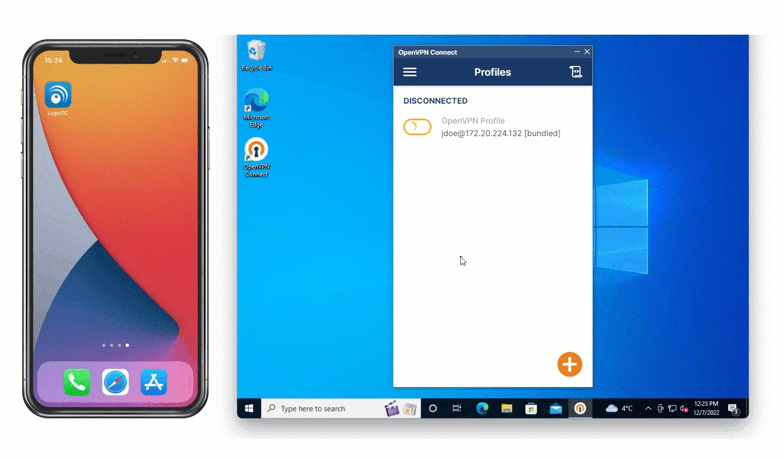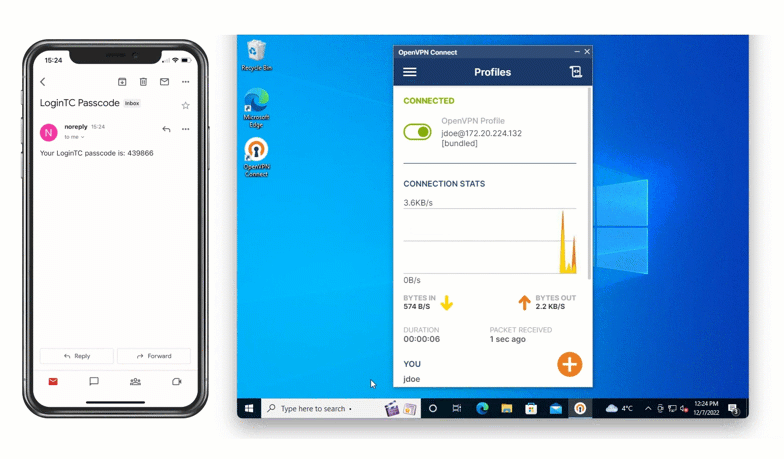
With email authentication, a user’s registered email address is sent an email containing a one-time login code. Below is an example of email authentication in action.
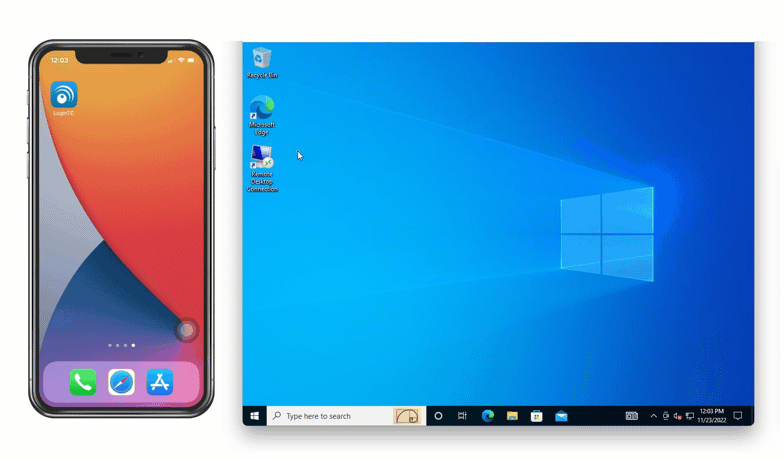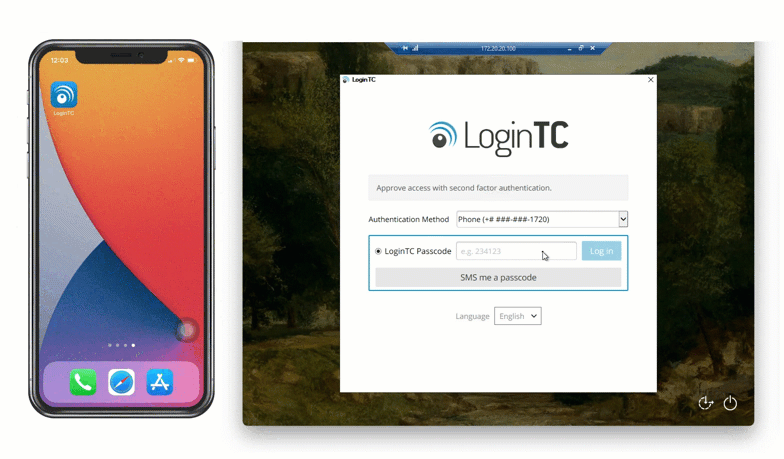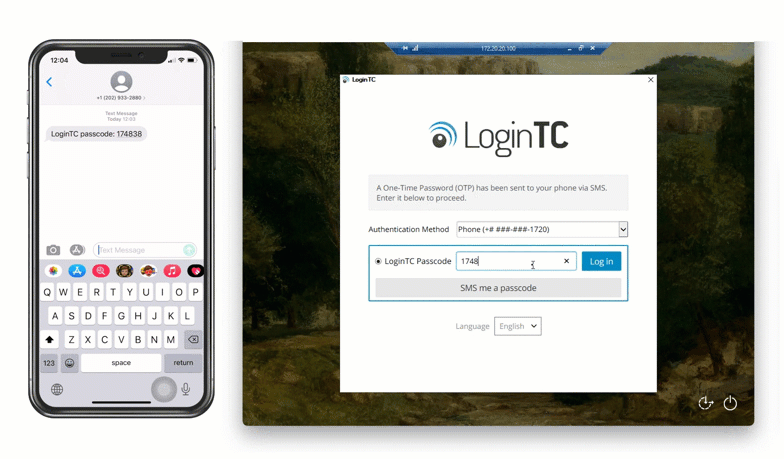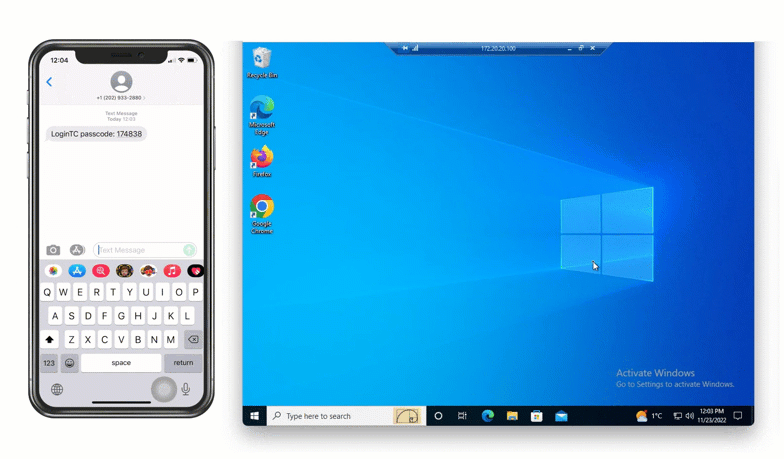
SMS can also be used to receive authentication codes. Users are sent a one-time code as a text message to their registered phone number.
Finally, registered phone numbers can also be used to receive an authentication request via a phone call. With this method, users receive a phone call and are asked to press a key to confirm authentication, or are given a code over the phone, and must input that code to complete authentication.
Additional MFA considerations for Cyber Essentials certification
Beyond specific authentication methods, the Cyber Essentials program also encourages administrators to consider a number of factors when it comes to implementing MFA at their organization.

1. Usability
Logging into our accounts and services is a daily task. While making logins secure, you want to ensure that you’re not adding too much friction into the process. That’s why usability is a key consideration when implementing an MFA process that’ll work for your company. When it comes to usability, you want to make sure that you’re choosing a solution that connects seamlessly across many different integrations, and offers a wide variety of authentication options that can work for a range of end user needs.
2. Help desk workload
Before choosing an MFA solution, consider the resource capabilities of your IT department or help desk. If you’re a small team, you’ll want to ensure that your MFA solutions are easy to manage and troubleshoot if an end-user runs into any issues. For a deeper look at this issue, check out our blog post on the true cost of a bad MFA deployment.
3. Authentication logging
Keeping your end-users well informed is a critical component of cybersecurity education — but so is keeping your administrator informed. With authentication logging, administrators get a birds-eye-view of every authentication attempt that occurs at the organization. This way, they can flag and investigate any suspicious activity and take preventative measures before it becomes a problem.
4. Policy-based authentication
Finally, consider choosing an MFA solution that offers policy-based authentication. This allows administrators to control for variables like geo-location, geo-velocity, or time of day, and to deny authentication if an authentication attempt falls outside of normal bounds.
How to get started with MFA for Cyber Essentials Certification?
Now that you’re familiar with the details of the MFA requirements to meet the Cyber Essentials Certification, it’s time to find an MFA solution that works for your organization.
LoginTC meets all the MFA needs of the Cyber Essentials program and more. With a wide variety of authentication methods, 10,000+ use cases, and comprehensive policies to manage every part of your MFA deployment, LoginTC is ready to protect your accounts and services with simple, secure MFA.
Start a free trial today to begin your journey to a more cyber secure future.
