What is Grid Card Authentication and what are the benefits?
September 04, 2025 •
This comprehensive guide takes a look at the details of grid card authentication, illustrating how it works and why it stands out in the crowded landscape of authentication methods. From no-additional costs, to enabling authentication edge cases, there are many benefits to adopting grid card authentication at your organization.
Let’s take a look at the potential of this authentication method and walkthrough its implementation.
What is Grid Card Authentication?
Grid card authentication is a multi-factor authentication (MFA) method that operates by leveraging a physical or digitally saved grid card. This card, typically a small, wallet-sized piece of plastic or paper, contains a matrix of alphanumeric characters, also called “tuples”.
How does Grid Card Authentication work?
During the authentication process, users are prompted to enter specific characters from their grid card, corresponding to randomly selected coordinates. This method ensures that even if a malicious actor gains access to a user’s password, they would still require the physical grid card to complete the authentication process, significantly reducing the risk of unauthorized access.
The process begins with the user logging into the system using their standard username and password. Upon successful entry, the system then prompts the user to input specific characters, or “tuples”, from their grid card.
Below is a step-by-step walkthrough of how grid card authentication works.
Step 1: Print out or save your grid card for ease of access.
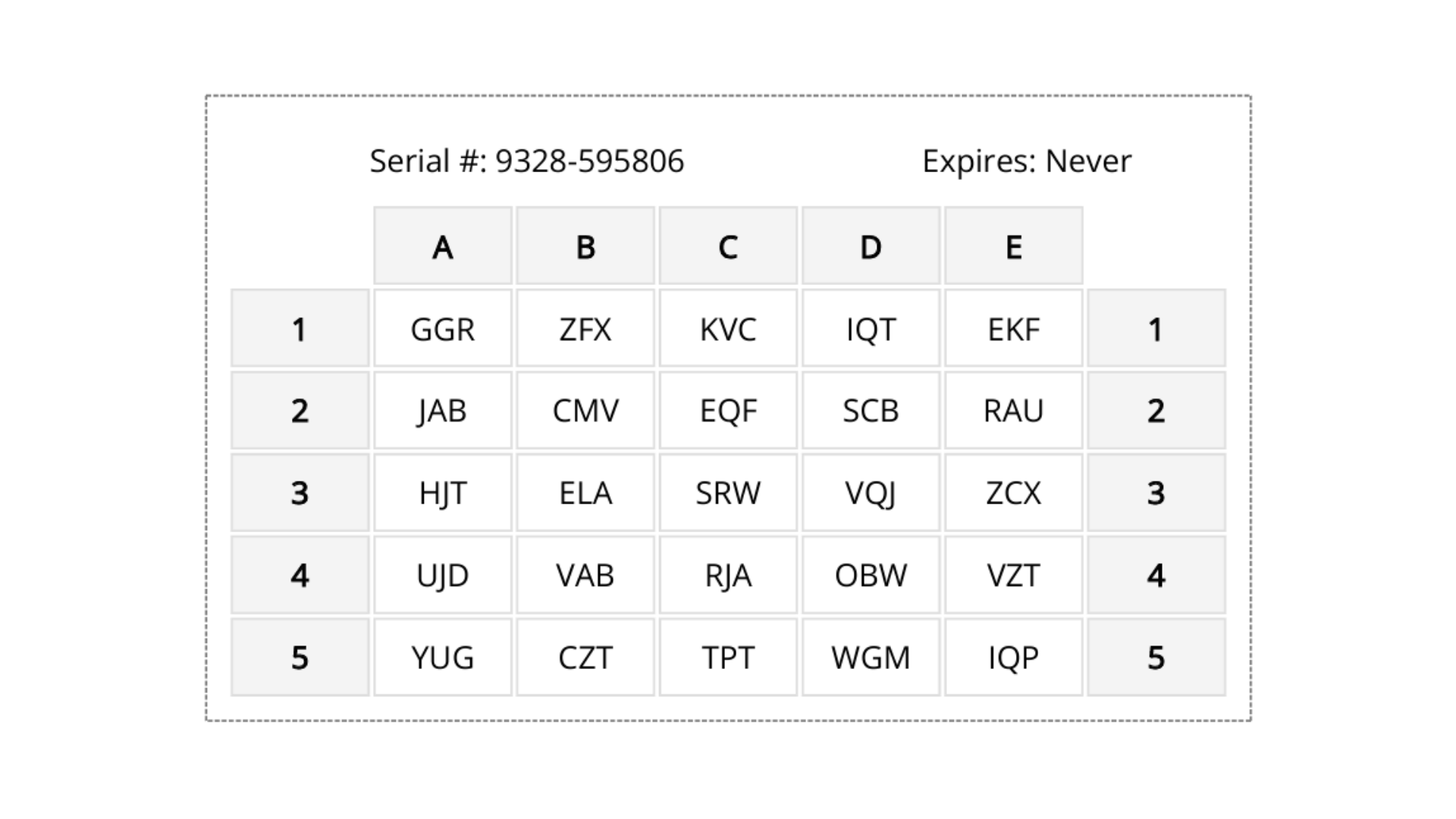
Step 2: Review the coordinates needed for authentication.
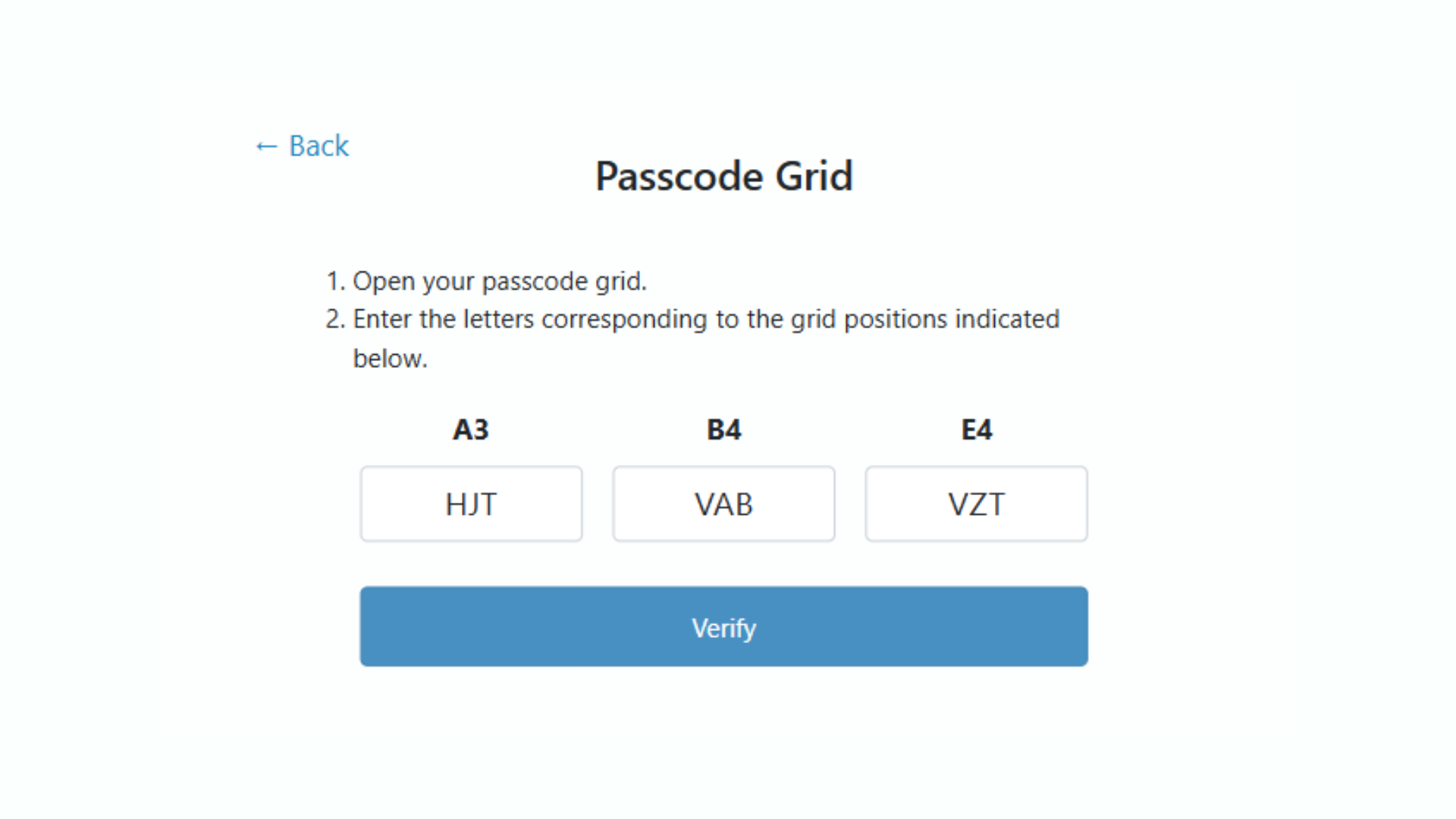
In this case, the user is being asked for the tuples located at A3, B4, and E4.
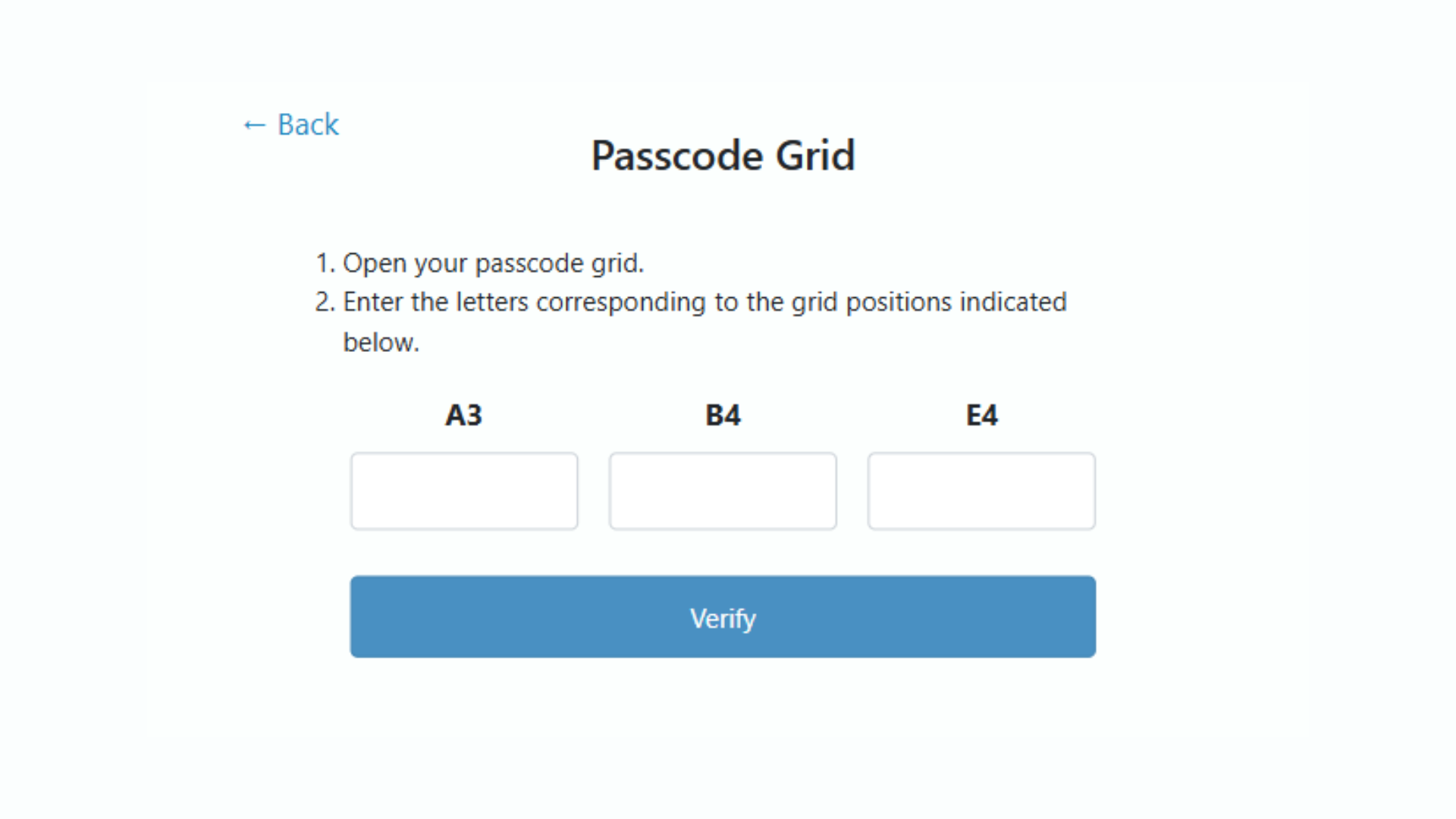
Step 3: Locate the requested coordinates on your personal grid.
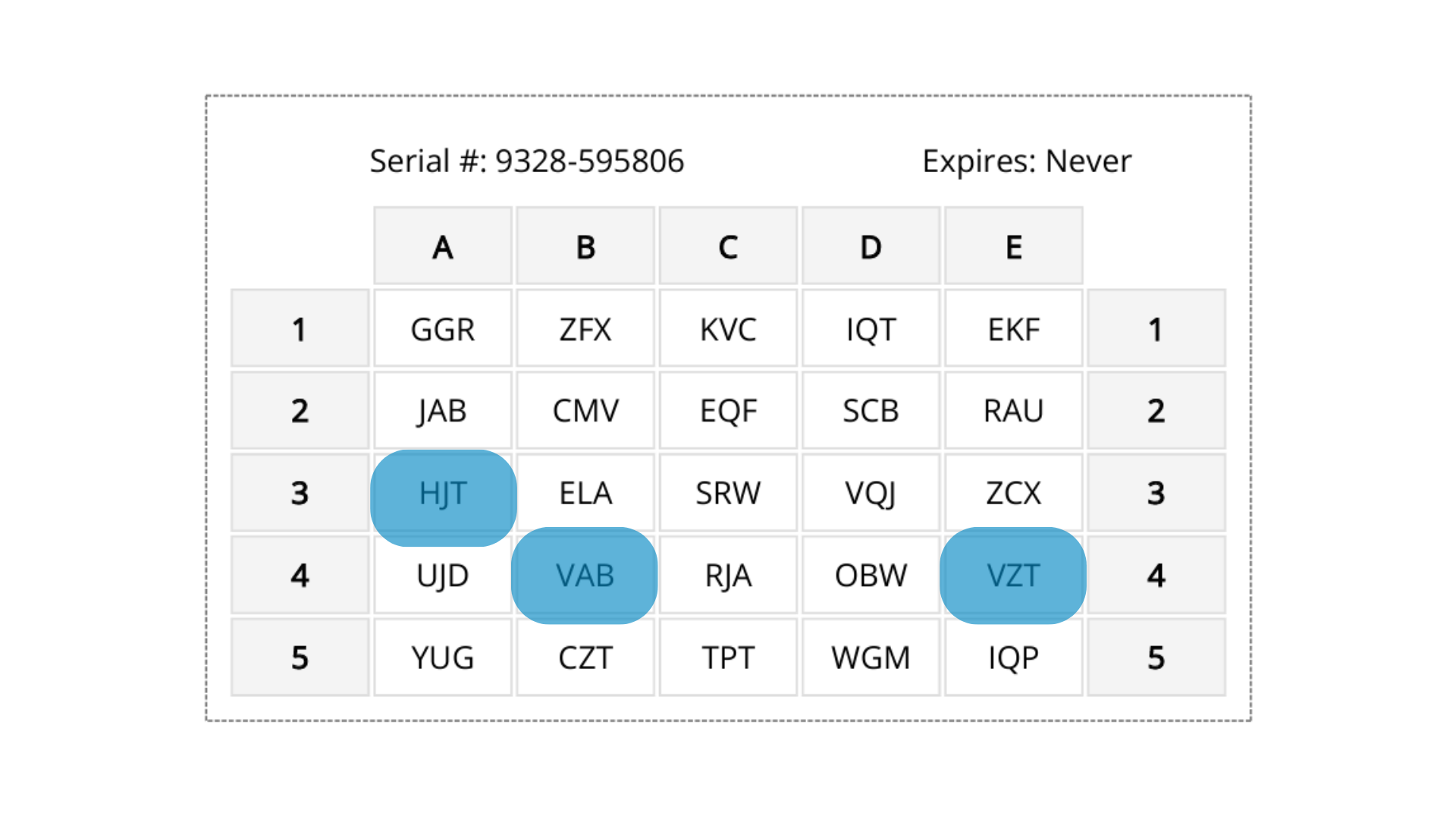
In this case, the coordinates correspond to the tuples “HJT”, “VAB”, and “VZT”.
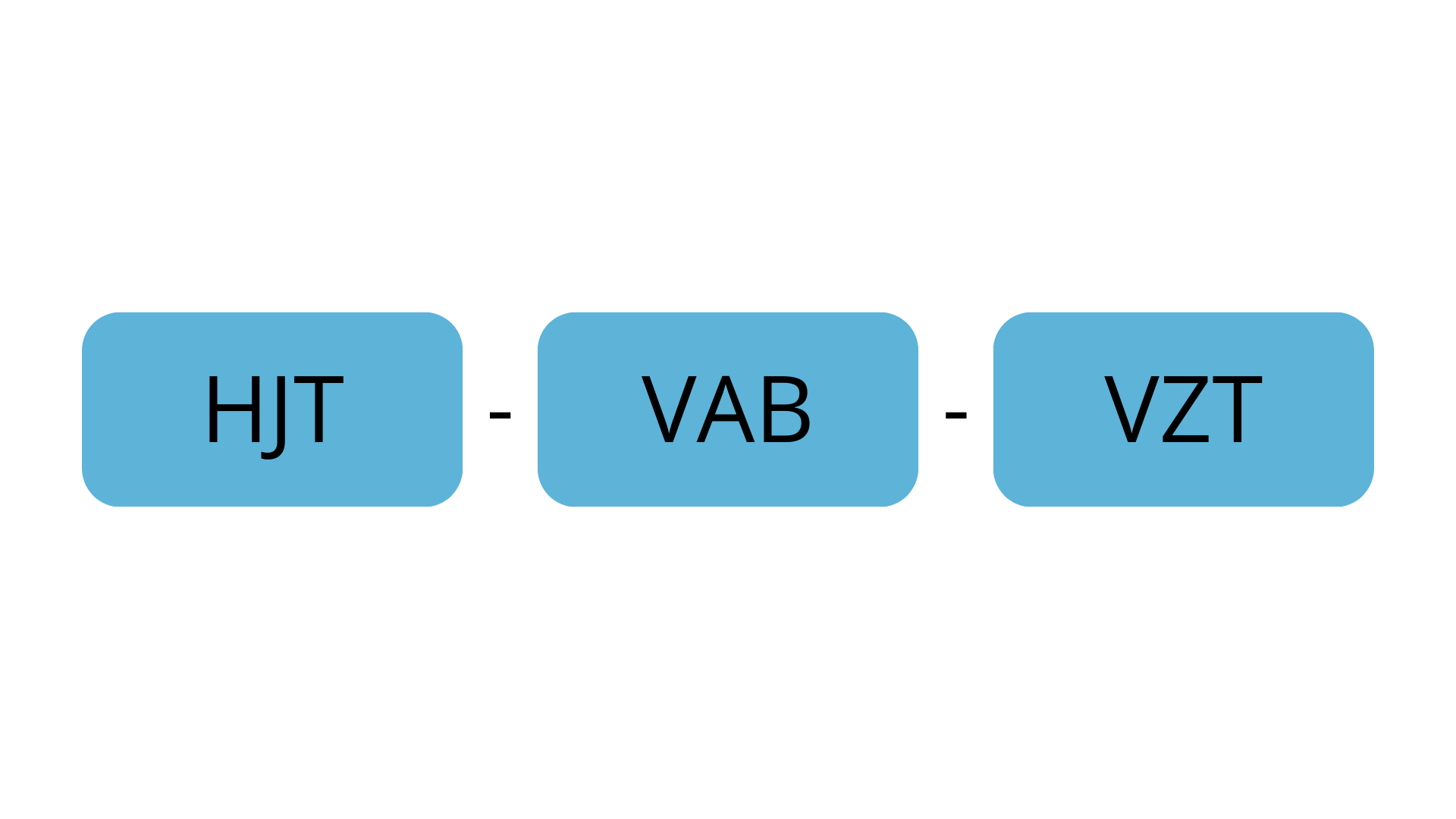
Step 4: Input the tuples requested into the space provided.
Step 5: Successfully login to your grid-card protected application
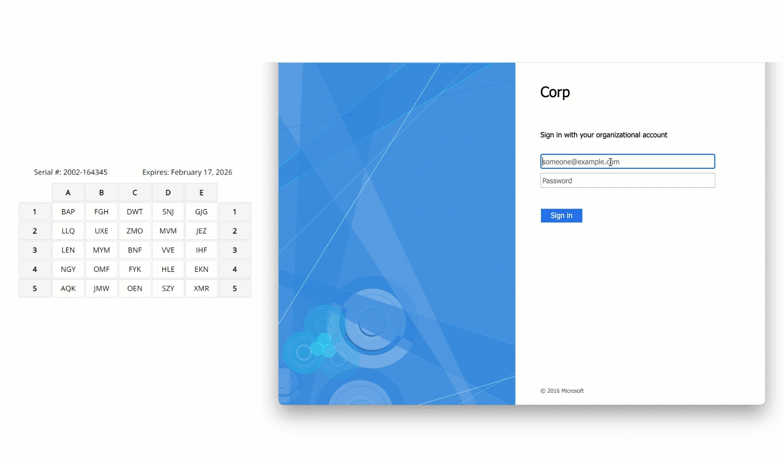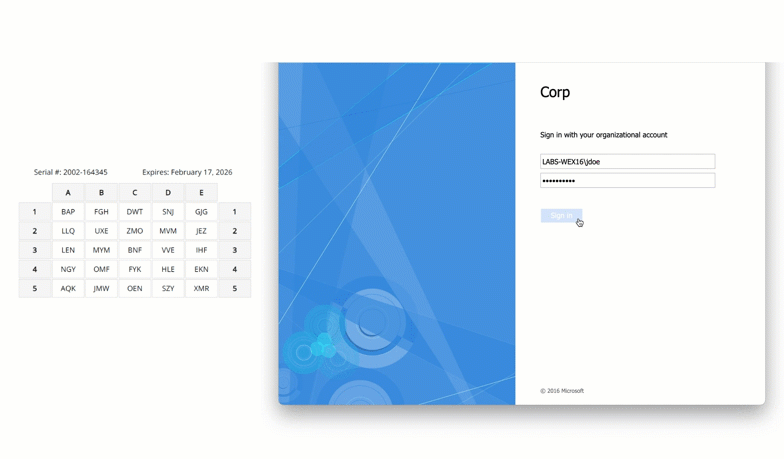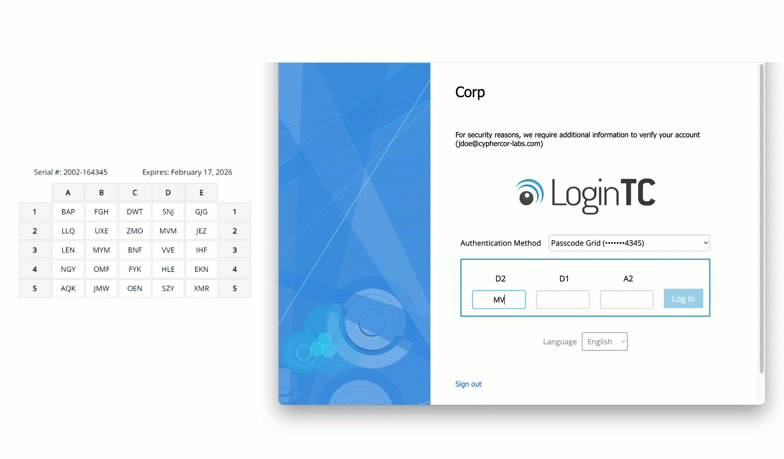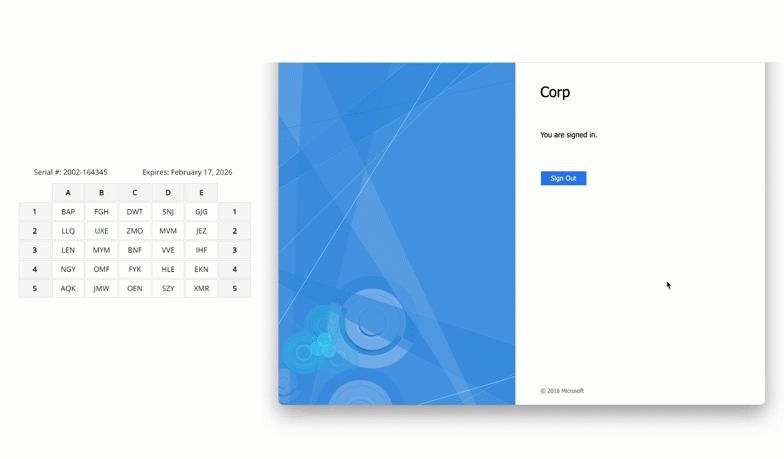
Here is a real world full example. In this case, the user is logging into Windows Remote Desktop and being asked for the characters located at coordinates B4, A2 and E5.
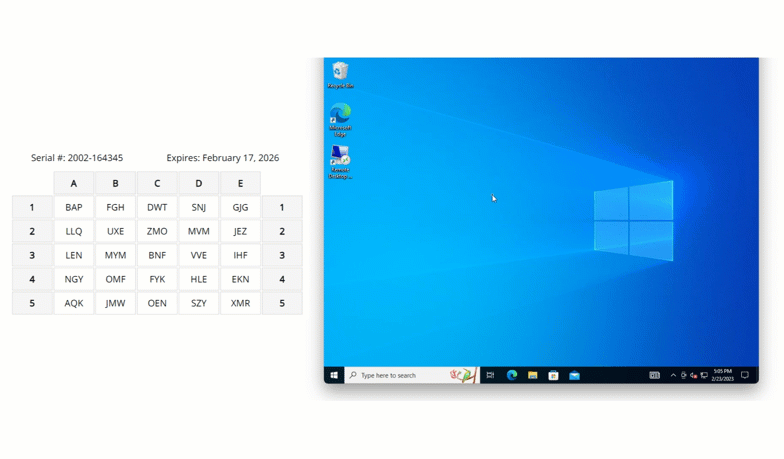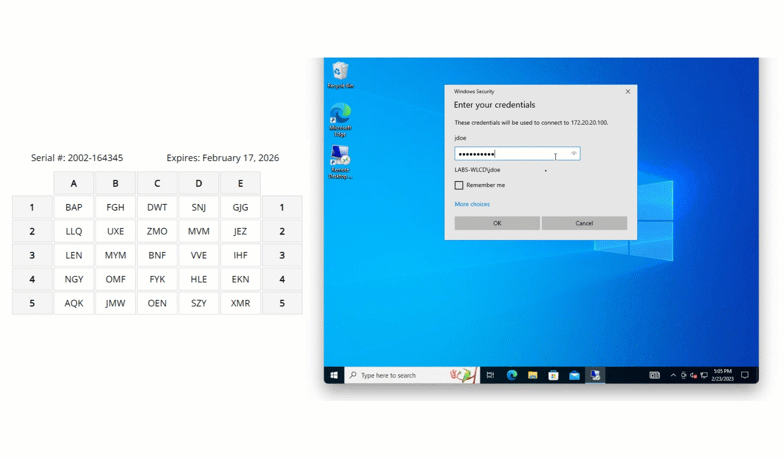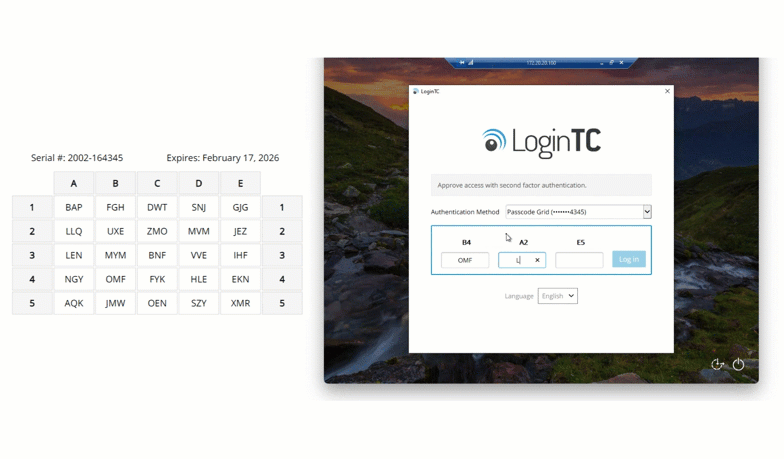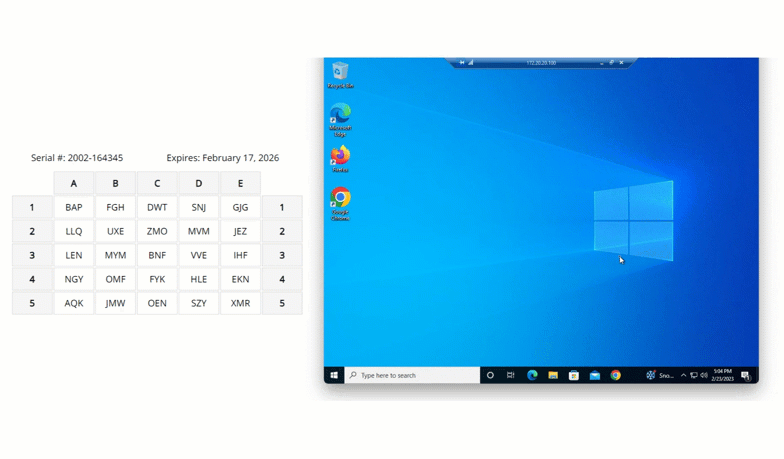
The user would then refer to their grid card, locate these coordinates, and enter the corresponding characters into the system. This step introduces an additional layer of security, as the specific authentication challenge changes with each login attempt, making it exceedingly difficult for attackers to predict or replicate.
Curious if this would work at your organization? Book a call with our team to see it in action.
Key benefits of using Grid Card Authentication
There are several core benefits to grid card authentication that your organization should consider when implementing a multi-factor authentication (MFA) solution:
- No hardware requirement: Grid card authentication is particularly advantageous because it does not rely on digital tokens or software-based solutions, which can be susceptible to hacking or malware. Instead, it uses a tangible, offline component that an attacker would need physical possession of to bypass.
- Simple distribution: Grid cards are simple for administrators to distribute to end users in a variety of use cases. Cards can be handed out like hardware tokens, or self-enrolled like authenticator apps. No matter what distribution mechanisms are available to your organization, grid cards can match it.
- Cost effective: Grid card authentication also offers a cost-effective solution for organizations looking to enhance their security posture. The production and distribution of grid cards are relatively inexpensive compared to other authentication technologies, such as biometric systems or sophisticated hardware tokens. Additionally, because grid cards do not require ongoing maintenance or updates, they represent a low-cost, low-maintenance option for long-term security. This affordability makes grid card authentication an attractive option for organizations of all sizes, from small businesses to large enterprises.
Grid Cards vs. other authentication methods
When it comes to multi-factor authentication, there’s no one-size-fits-all approach. Each method has its strengths, and grid cards fill a unique role that other factors can’t always cover.
- Mobile push notifications: These are convenient and familiar, but not every workplace allows phones on the job. Factory floors, call centers, and high-security facilities often have strict no-device policies. Grid cards provide a reliable alternative without loosening security requirements.
- Hardware tokens: Tokens offer strong protection but come with costs, including purchasing, distributing, and replacing them at scale. A passcode grid is cheaper to roll out, and easier to replace.
- SMS or phone calls: While widely used, these methods rely on cellular connectivity, which can be spotty or unavailable for some sites. A grid card works anywhere, even offline, making it better suited for field staff and contractors.
- Biometrics: Fingerprint or facial recognition can be highly secure, but they demand specialized hardware and raise privacy concerns. Grid cards deliver strong authentication without needing extra infrastructure or storing sensitive biometric data.
- Authenticator app: While common authenticator apps, like Google Authenticator and Microsoft Authenticator, are growing in popularity, they don’t work for every use case. When end users aren’t able to use a smartphone, grid cards might be a better no-cost alternative.
- Security Keys: FIDO2-based Security Keys are considered the strongest authentication method available, but for organizations with simple requirements that don’t have the budget for expensive security tokens, a grid card can be a good alternative for those needing strong but inexpensive security.
- Email OTP: While Email OTP is often a good authentication method for organizations looking to save money and use existing devices, Email OTP isn’t always an option for every application. For example, protecting that email account! Organizations can use grid cards as an additional method to compliment Email OTP.
In short, grid card authentication isn’t meant to replace every method, but it can be useful to fill the gaps. For organizations that can’t rely on phones, tokens, or constant connectivity, grid cards provide an affordable, secure, and user-friendly option.
Implementing Grid Card Authentication at your organization
Any successful deployment of MFA software at your organization requires some degree of planning how the implementation will occur. Consider these steps when implementing grid card authentication to your users.
Step 1: Evaluate existing infrastructure
Implementing grid card authentication in your organization begins with a thorough assessment of your current security posture and identifying areas where additional protection is needed. Start by evaluating the sensitivity of the data you handle and the potential risks associated with unauthorized access. This will help you determine the appropriate level of security and whether grid card authentication is the right solution for your needs.
Need help with this step? Book a call with our team:
Step 2: Design a roll-out plan
The implementation process should include a comprehensive rollout plan that covers user training, how you want to distribute the grid cards, and integration with your existing authentication systems. Decide on a small group of users who will begin using grid card MFA first, with a gradual rollout strategy to slowly get everyone on board.
Begin by educating your employees or users on the importance of grid card authentication and how it works. Provide clear instructions on how to use the grid cards and address any questions or concerns they may have.
This step is crucial for ensuring user acceptance and compliance, which are key to the success of your grid card authentication program.
Step 3: Complete technical integration
Finally, integrate grid card authentication into your existing systems. This may involve working with your IT team or a third-party provider to ensure seamless integration and functionality. Test the system thoroughly to identify and resolve any potential issues before full deployment. Once the system is live, continue to monitor its performance and make necessary adjustments to optimize security and user experience. Regularly review and update your grid card authentication procedures to keep pace with evolving security threats and maintain the highest level of protection for your organization.
How to use grid cards to protect applications and services
By combining Grid Cards with an MFA service like LoginTC, they can be easily applied across a wide range of environments, making them a versatile option for securing critical systems.
Here are some of the most common ways organizations use grid card authentication with LoginTC MFA:
Windows Logon
Add an extra layer of protection to local, domain, remote, or UAC Windows logins. With grid card MFA, users enter their credentials as usual, then provide the requested tuples from their card before gaining access.
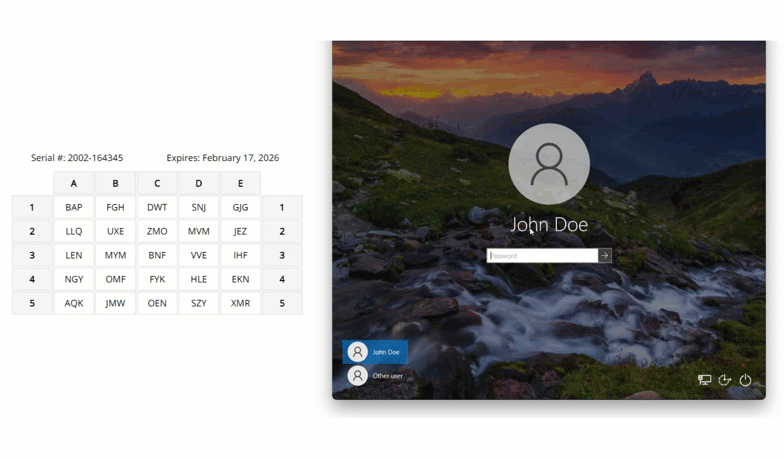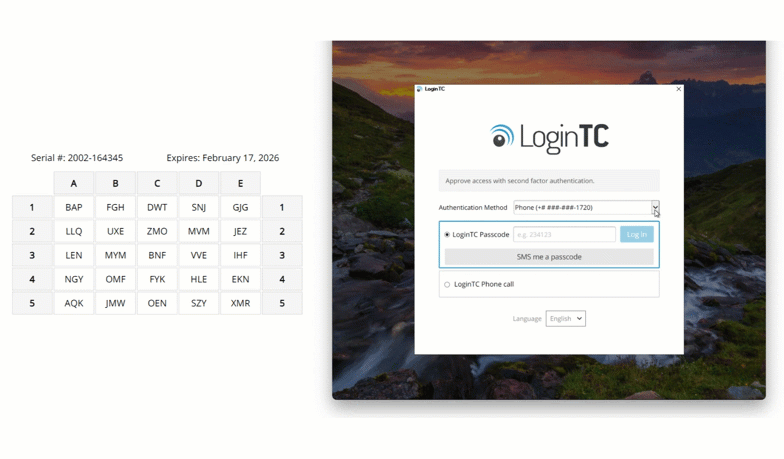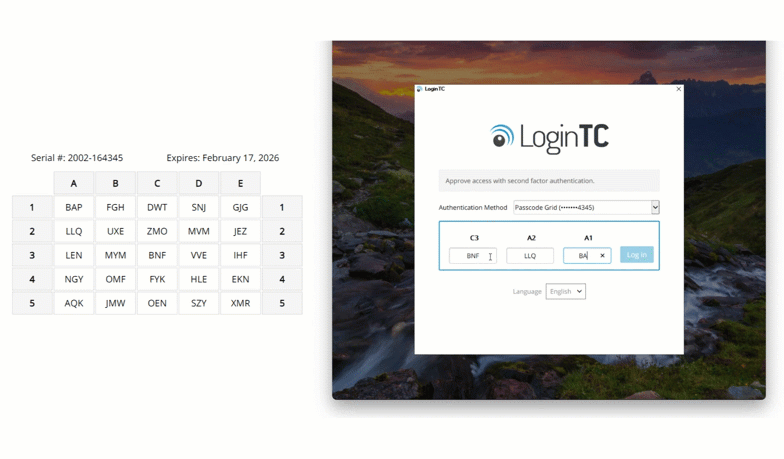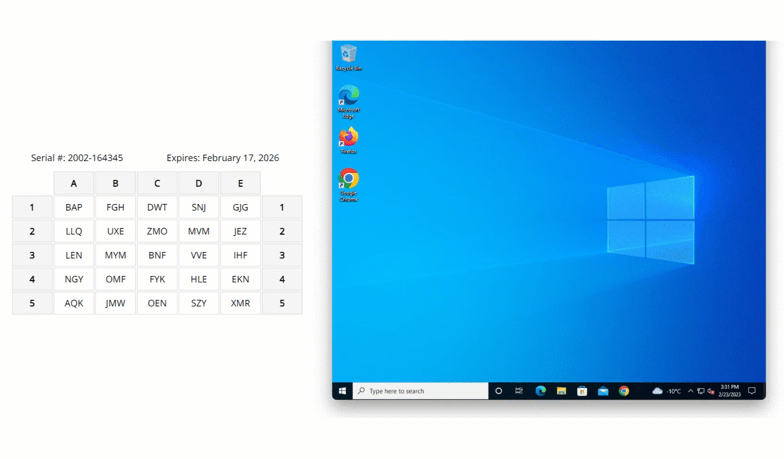
Entra ID
Secure your Microsoft Entra ID logins with grid card MFA. This adds strong authentication to cloud services like Microsoft 365 without requiring users to carry a phone or token, enhancing Entra ID’s native capabilities.
Citrix
Protect virtual apps and desktops by enabling grid card authentication on Citrix. This ensures that only verified users can connect to critical virtualized environments.
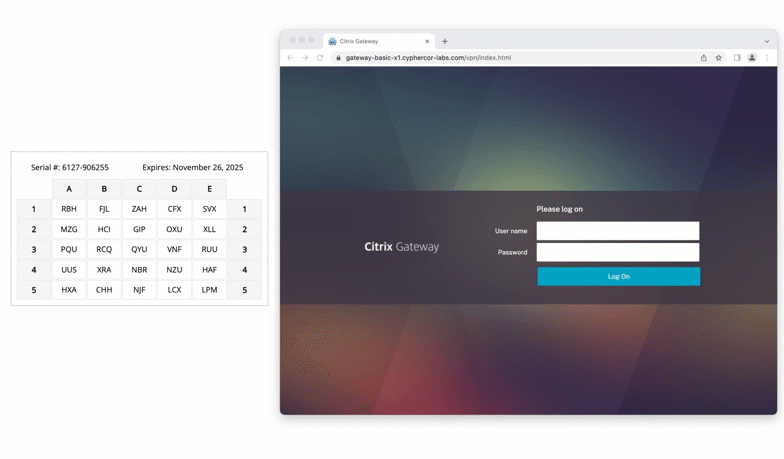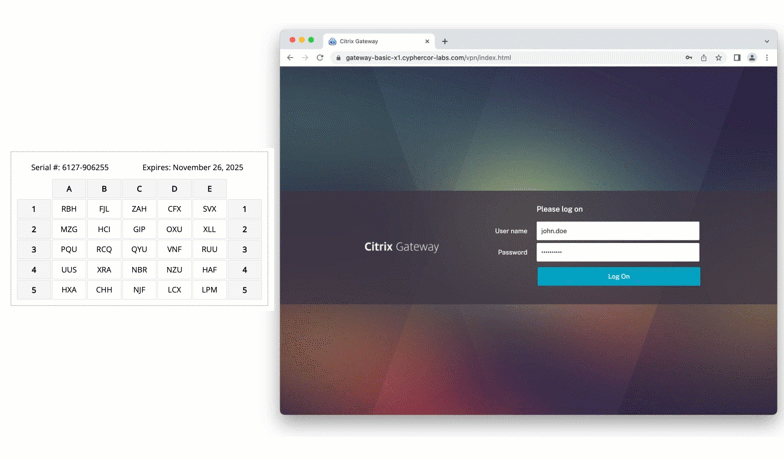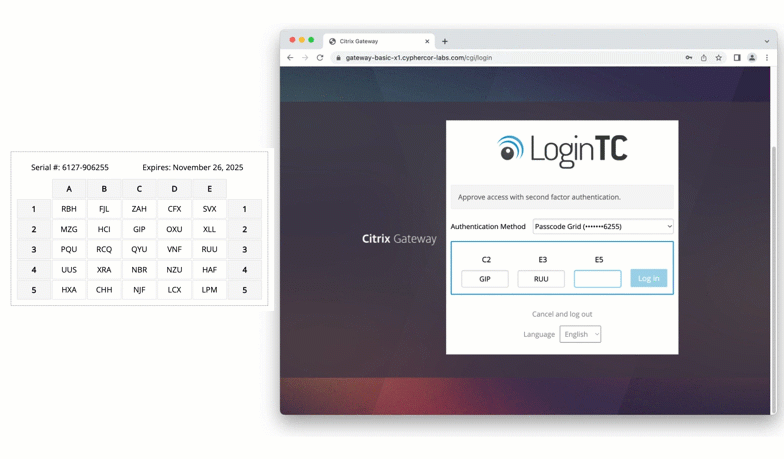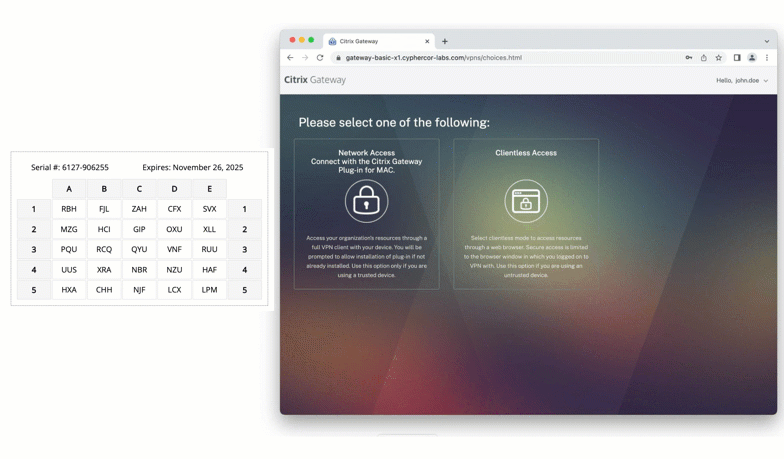
Cisco ASA
Extend grid card MFA to Cisco ASA VPNs, keeping remote access secure for employees connecting from outside the office. Even if a password is stolen, the VPN remains protected.
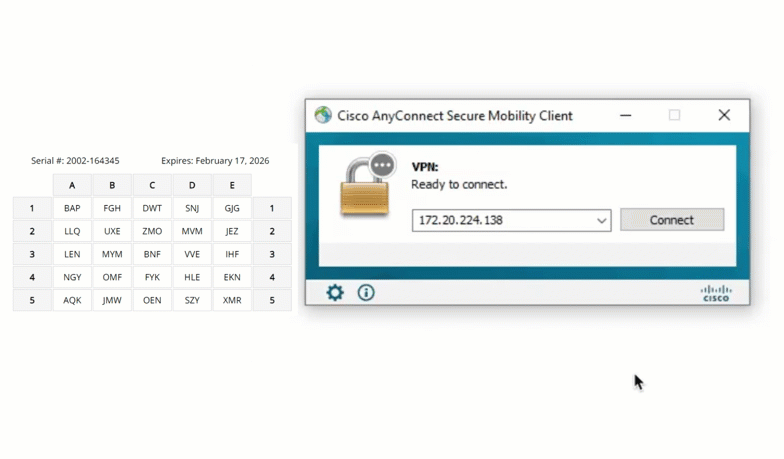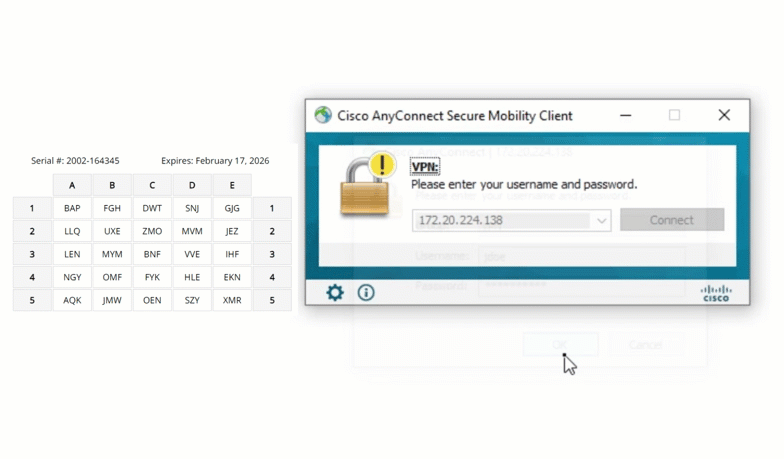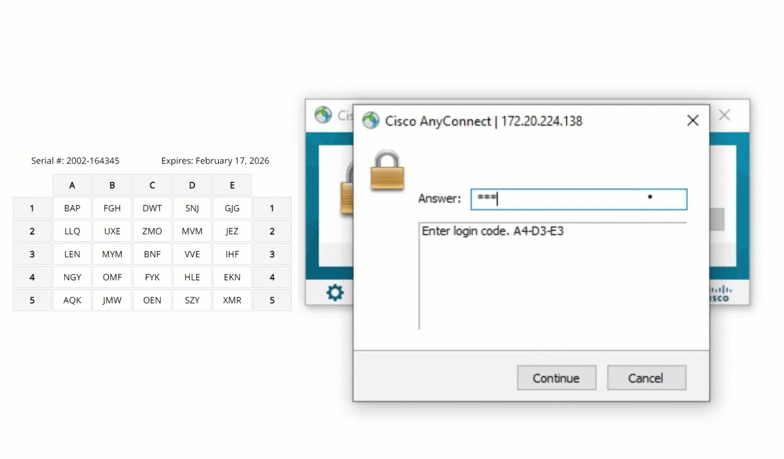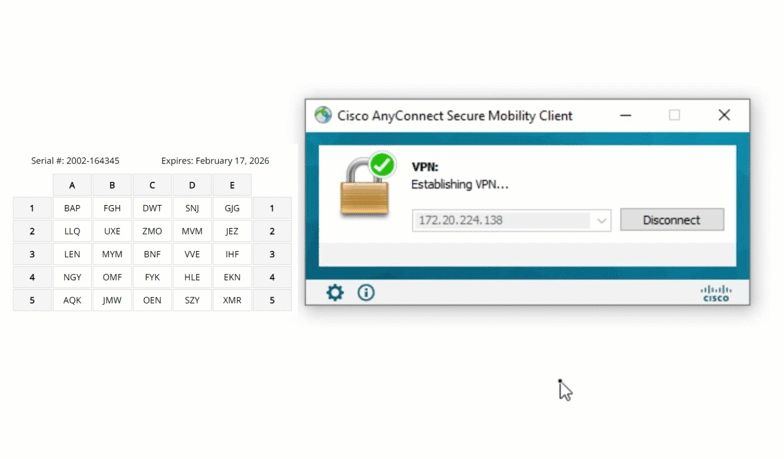
Fortinet FortiGate
Fortinet firewalls and VPNs can be also secured with grid card MFA, giving organizations a reliable way to defend network perimeters against credential-based attacks.
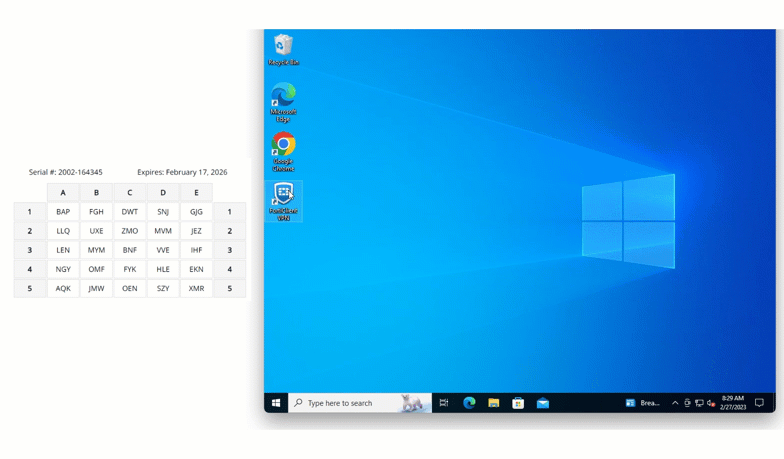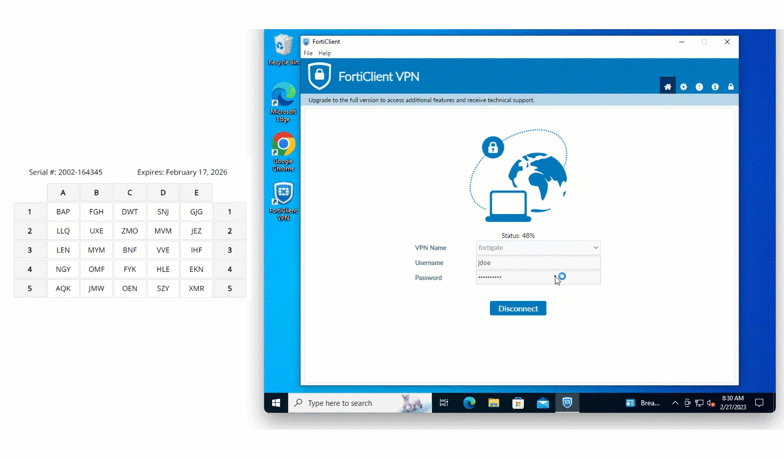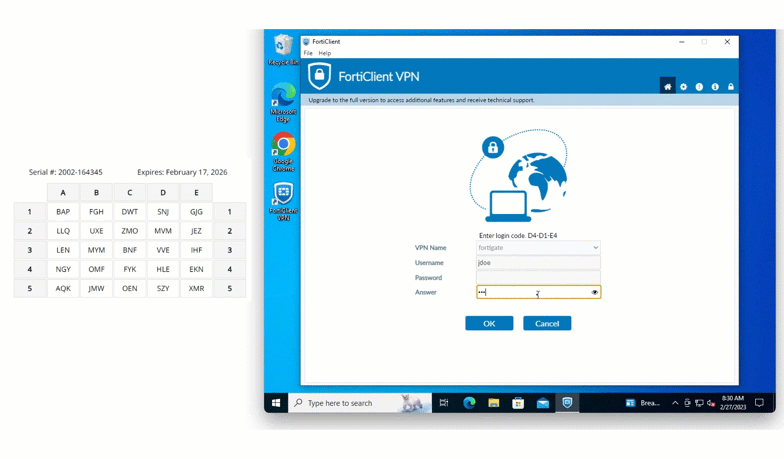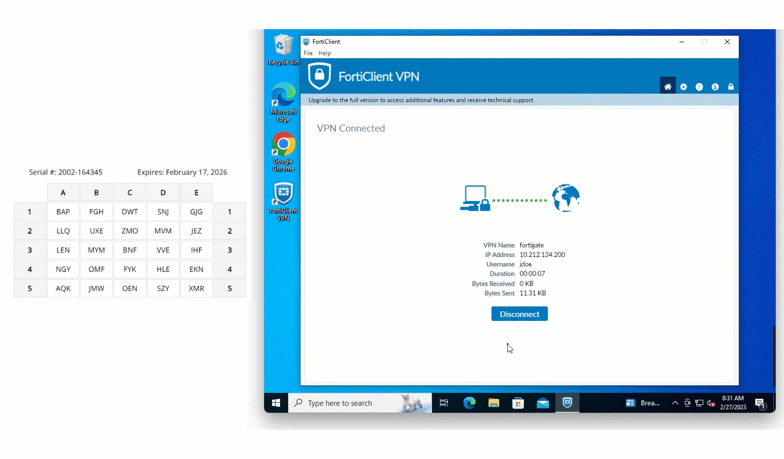
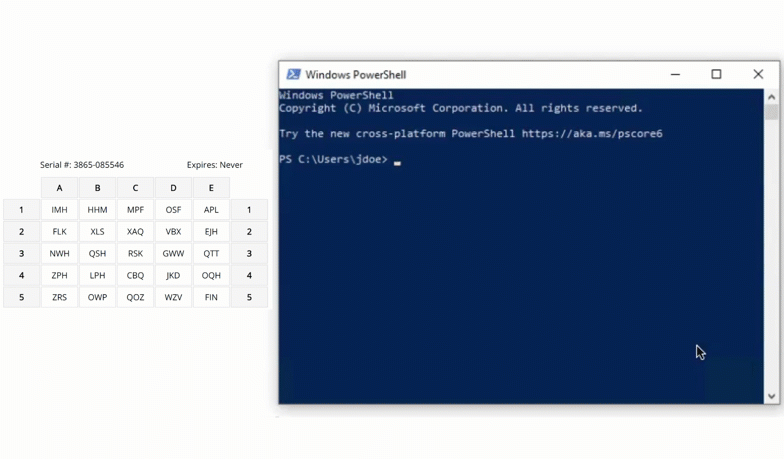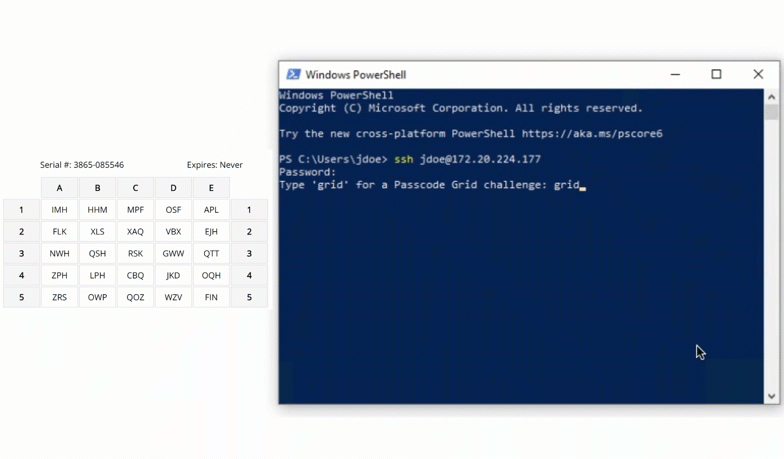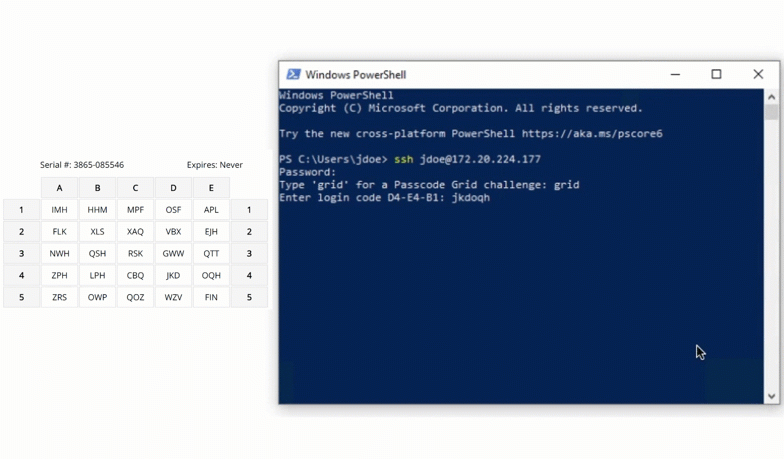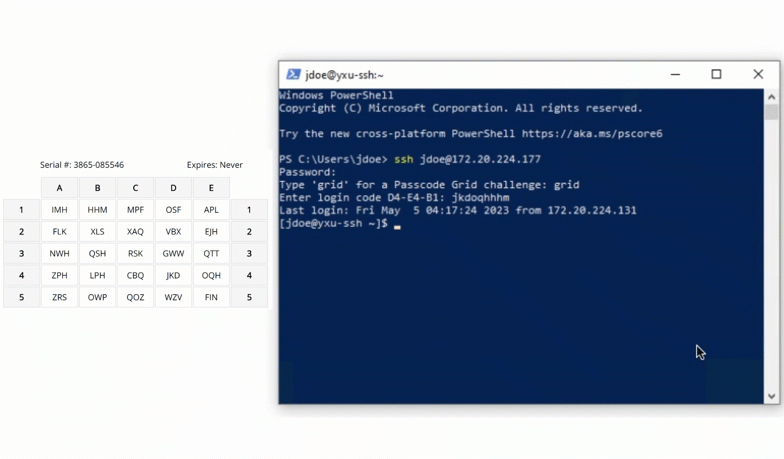
SSH
Protect server access by requiring grid card authentication for SSH logins. This stops attackers from gaining entry with just a compromised password.
Active Directory Federation Services (AD FS)
Secure your AD FS service with grid card MFA. By protecting the authentication flow at the AD FS layer, you strengthen the trusted account that other connected applications and services rely on.
Real-world applications of Grid Cards
Grid cards are a practical form of MFA that shine in environments where traditional second factors aren’t feasible. Instead of relying on mobile devices or tokens, users authenticate with a simple printed card containing randomized codes.
Here are a few scenarios where grid cards provide an ideal solution:
- Factory floors: Operators often need to access shared terminals quickly, and phones are typically restricted for safety reasons. Grid card authentication gives them a secure, phone-free way to log in.
- Call centers: With hundreds of employees authenticating every day, requiring mobile MFA can be disruptive or impractical. A grid card ensures strong security without introducing additional hardware.
- Education environments: Students logging into lab or library computers benefit from MFA without needing to enroll personal devices. Grid card authentication offers schools a low-friction way to enforce stronger login security.
- Remote field operations: In areas with limited cell service or where mobile devices aren’t permitted, a grid card is lightweight, portable, and always available.
- No hardware allowed: High security environments in which no additional technology or hardware is allowed to enter certain areas can also benefit from the paper-based authentication nature of grid cards.
- BYOD restrictions: When end users are restricted from using personal devices, and purchasing tokens or phones for every user would be cost prohibitive, grid cards are a great alternative.
Grid cards provide organizations with a balance of usability and security, especially valuable in industries where compliance requires MFA but mobile devices aren’t an option.
Best practices for maximizing security with Grid Card Authentication
To maximize the security benefits of grid card authentication, organizations should follow best practices that ensure effective implementation and ongoing management. Below are some recommendations to follow:
- Rotate cards: One key practice is to regularly update and rotate the grid cards used by employees or users. This helps prevent the cards from becoming compromised over time and ensures that the authentication process remains secure. Establishing a regular schedule for distributing new cards and retiring old ones can help maintain the integrity of the system.
- Defence in depth: Another important practice is to combine grid card authentication with other security measures, such as strong password policies and regular security training. This is known as a “defence in depth” strategy. By using grid cards as part of a multi-layered security approach, organizations can create a more comprehensive defense against unauthorized access. Additionally, educating users about the importance of security and how to recognize and respond to potential threats can help prevent security breaches and promote a culture of vigilance.
- Regular monitoring: Finally, organizations should continuously monitor and evaluate the effectiveness of their grid card authentication system. This includes regularly reviewing access logs, conducting security audits, and staying informed about emerging threats and vulnerabilities. By proactively identifying and addressing potential weaknesses, organizations can ensure that their grid card authentication system remains robust and effective in the face of evolving security challenges.
Next steps
Grid card authentication is a simple but powerful way to strengthen login security, especially in places where phones or tokens just don’t fit. It’s affordable, easy to use, and removes barriers that often keep organizations from rolling out MFA everywhere it’s needed.
Experience how LoginTC grid cards can secure your organization, even without phones or hardware. Start a free trial today or book a demo with our team.