-
How to deploy MFA for SCADA environments
December 23, 2025 •
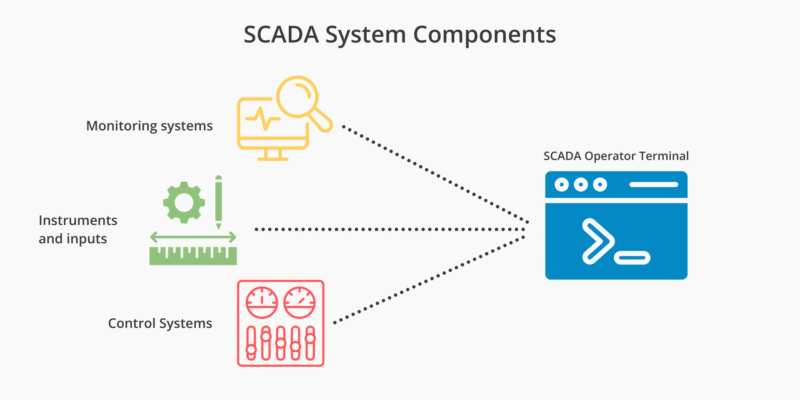
Supervisory Control and Data Acquisition (SCADA) systems manage everything from water filtration and power distribution to chemical manufacturing. Traditionally, these systems were protected by “air-gapping”, the practice of keeping critical infrastructure entirely disconnected from the public internet. However, as the Industrial Internet of Things (IIoT) grows and the need for remote monitoring increases, the gap […]
-
How to migrate to Fortinet IPsec VPN IKEv2 MFA
December 17, 2025 •

Fortinet has signaled a clear direction: organizations should be transitioning off SSL VPN and onto IPsec-based VPNs, specifically IKEv2. This shift aligns with broader industry recommendations around stronger encryption, standardized negotiation, and reduced attack surface. For many customers, though, the technical transition raises a tough practical question: How do you enforce MFA for Fortinet IPsec […]
-
CJIS MFA Requirements: Everything you need to know
October 31, 2024 •

As the new CJIS MFA requirements take effect, how can you ensure that your law enforcement agency remains in compliance with the CJIS Security Policy? Government entities like police stations, sheriffs offices, or other entities that access the FBI’s Criminal Justice Information Services must ensure that sensitive criminal justice information is handled with proper cybersecurity […]
-
How the Azure MFA requirement will affect your organization
September 30, 2024 •

As security threats continue to evolve, Microsoft has updated its policies to introduce an Azure Multi-factor authentication (MFA) requirement that will ensure stronger identity and access management protection for administrator and user accounts. MFA is a proven tool to prevent cyber attacks and protect accounts from unauthorized access. In this post, we’ll explore what these […]
-
Fortinet 2FA Requirement: What your organization needs to know
July 08, 2024 •

The popular VPN and firewall service provider, Fortinet, is taking a strong stance on security by enforcing the adoption of two-factor authentication (2FA) across its entire user base. Learn about the new Fortinet 2FA requirement and how to get your organization ready before the deadline. What is the Fortinet 2FA requirement? Starting on July 24, […]
-
Everything you need to know about Australia’s cybersecurity laws
May 09, 2024 •

In the past year, the parliament of Australia has passed a new cybersecurity laws aimed at cracking down on increasingly harmful ransomware attacks and data breaches that have shaken the country since 2022. Australia now seeks to be a global leader in cybersecurity by 2030, and has introduced sweeping reforms tackling every part of the […]
-
The Ultimate Guide to MFA for Cyber Essentials Certification
November 07, 2023 •
Introduction The Cyber Essentials Certification is a comprehensive program for businesses who want to improve their cybersecurity posture. As with recent updates to data privacy legislation, the requirements of the Cyber Essentials Certification can be confusing, especially when it comes to the specifics of cybersecurity tools and technology required to meet the certification. In this […]
-
What you need to know about the IRS’s MFA requirements
February 01, 2023 •

If you’ve managed federal tax information in the past few months, you may have noticed the introduction of multi-factor authentication to the process. As part of the IRS’s initiative to ensure tax professionals are protecting their client data, the IRS began mandating the use of MFA on critical infrastructure. In this article, we’ll dig into […]
-
The MFA Requirements You Need to Know About
December 12, 2022 •

Multi-factor Authentication (MFA) is becoming more common by the day. The United States government recently announced that it would require MFA sign-in methods for all federal agency staff. Companies are now requiring that users sign in via MFA rather than just using a username and password, and many cyber insurance policies also require that you use MFA. […]
-
Why Radio Stations Need Cybersecurity, And What They Can Do To Protect Themselves
May 14, 2021 •
You might already be thinking, “radio stations, really?’ Surely banks or multi-national corporations like Amazon or even accounting firms would be more of a target for cyber attacks than a station playing tunes and sharing the latest news.
-
March 11, 2021 •
Think cybersecurity is only for companies like Amazon, Equifax, and Sony? Think again.
-
Role of Two-Factor Authentication in Regulatory Compliance and Industry Guidelines
March 19, 2013 •
Summary of regulatory compliance and guidelines related to two-factor authentication in the United States.