Software OTP Tokens Guide
OverviewLoginTC software tokens are capable of generating One-Time Passwords (OTPs) for accessing resources protected with LoginTC.
Managing Software OTP TokensSoftware OTP tokens are only displayed on the LoginTC App if they are enabled for that LoginTC Domain.
Enabling / Disabling for a Domain
To enable or disable software OTP tokens for a domain:
- Log in to LoginTC Admin
- Click Domains
- Select the domain you want to modify
- Click on Settings:
- Scroll down to Software OTP Token
- Select either Enabled or Disabled
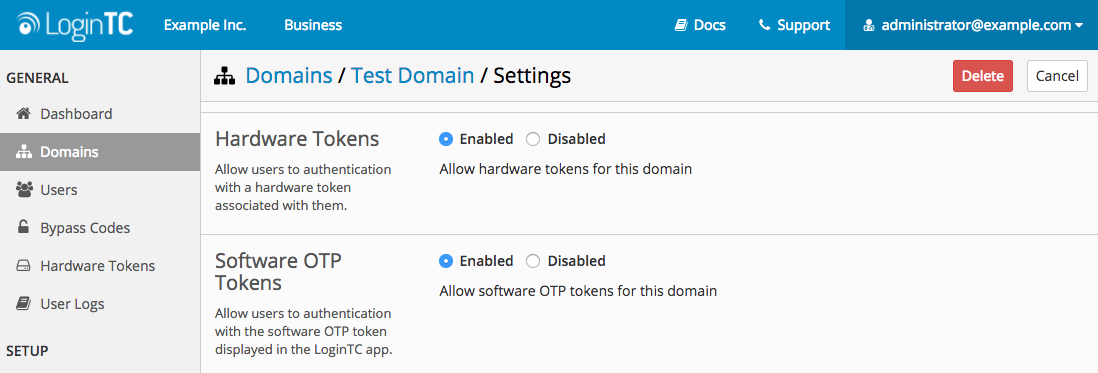
- Scroll down to the bottom of the page and click Update
Enabling / Disabling for specific Application
To enable or disable software OTP tokens for a specific application:
- Log in to LoginTC Admin
- Click Applications
- Select the application you want to modify
- Select the appropriate application policy
- Under Authentication Methods Scroll down to Software One-time Password (OTP)
- Select either Enabled or Disabled
- Scroll down to the bottom of the page and click Save
LoginTC App Requirements
LoginTC software OTPs require the following LoginTC App versions:
- LoginTC Android 2.2.0+
- LoginTC iOS 2.2.0+
- LoginTC Chrome 1.2.0+
If your device has an older version of the LoginTC App you may upgrade to the newest version from your platform’s app store.
Connecting to a VPN
When authenticating, a user enters their username normally. In the password field, they should should enter their password followed immediately by a comma and the One-Time Password (OTP) displayed on the LoginTC app. The OTP is valid for 30 seconds. An indicator beside the OTP informs the user how much time is left.
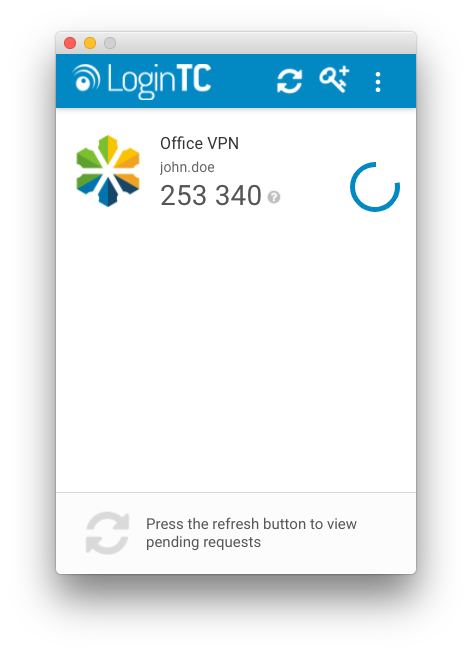 Regular input (without OTP):
Regular input (without OTP):
username: john.doe
password: johnPasswordInput with OTP:
username: john.doe
password: johnPassword,253340If the OTP is valid, the user will be authenticated without a request being sent to their 2nd factor device. If the OTP is invalid the user’s request will be denied.
Warning
There must not be any spaces between the password, the comma, and the OTP
Using OTPs with Challenge Authentication Mode (LoginTC RADIUS Connector)
The software OTPs work great with the Challenge Authentication Mode if you are using the LoginTC RADIUS Connector and if your RADIUS clients support it. When using the Challenge Authentication Mode, the user will be prompted to enter an OTP or press 1 to proceed with the standard LoginTC Push authentication.
For more examples see: LoginTC Passcode
TroubleshootingIf your users are having difficulty authenticating with OTPs, check the Logs page in the LoginTC RADIUS Connector web interface:
- Log in to your RADIUS connector web UI
- Click Logs
Software OTPs Not Enabled for Domain
If a user is trying to access a domain where software OTP token authentication is not enabled, you will find the following error message within their authentication attempt:
2016-08-04 13:40:25,163 - DEBUG - Checking for otp
2016-08-04 13:40:25,300 - DEBUG - otp are not enabled for this domain
2016-08-04 13:40:25,300 - CRITICAL - Invalid credentials for user john.doe
Exception: Invalid credentials for user john.doeYou can enable or disable software OTP token authentication for a domain from the LoginTC Administration Panel. Click here for more information
Invalid OTP
If a OTP is detected, you will find the following log messages associated with the user’s login attempt:
2016-08-04 17:17:31,568 - DEBUG - Checking for otp
2016-08-04 17:17:31,607 - DEBUG - otp enabled for this domain
2016-08-04 17:17:31,607 - DEBUG - Possible otp detected
2016-08-04 17:17:31,616 - DEBUG - Verifying otp for john.doe
2016-08-04 17:17:31,616 - DEBUG - Calling-Station-IP is null, not sending originating IP Address
2016-08-04 17:17:31,684 - CRITICAL - Invalid otp
APIException: Invalid otpIn this case, the user may be attempting to use a OTP that is either: – Not associated with the user – Out of Sync
You can check the state of a user’s otp through the LoginTC Admin Panel. Click here for more information on enabling software OTP tokens.