-
How to Add MFA for Windows Logon
February 19, 2026 •

Your Windows login screen is the front door to your entire network. In an age of sophisticated phishing attacks and rampant credential theft, leaving that door protected by only a password is a significant risk. Implementing strong mfa for windows logon is no longer an optional upgrade; it’s a foundational security measure for any organization. This simple, […]
-
What is RADIUS Authentication?
February 17, 2026 •

Your VPN and Wi-Fi are the front doors to your organization’s network. If they’re secured with only a password, those doors may not be as strong as you think, leaving you exposed to modern threats and struggling to meet compliance requirements. For many organizations, the key to controlling this access lies in a long-standing but […]
-
What Are Authentication Factors? A Complete Guide
February 13, 2026 •

In today’s complex cybersecurity landscape, protecting your organization requires more than just a strong password. You know that Multi-Factor Authentication (MFA) is essential, but understanding the different authentication factors can feel overwhelming. If technical jargon like ‘inherence’ or ‘possession’ seems confusing, or you’re unsure how to choose the right security methods for your team, you’re in the […]
-
MFA Solution Cost: A Complete Guide to Pricing and TCO
February 12, 2026 •

Comparing multi-factor authentication vendors can be frustrating. Pricing models often seem intentionally opaque, making it nearly impossible to calculate the true mfa solution cost for your organization. You’re left worrying about hidden fees, unexpected support charges, and the ongoing resources required for maintenance. This uncertainty makes it difficult to budget effectively and even harder to justify the […]
-
How air-gapped MFA secures isolated networks
February 10, 2026 •

For organizations with critical infrastructure, cloud-based security is not an option. Your security policies demand complete network isolation, which creates a significant challenge: how do you enforce strong multi-factor authentication with zero internet connectivity? This is the precise challenge that a robust air-gapped mfa solution is designed to solve. It provides the strong, modern authentication […]
-
Hybrid Cloud MFA: The Best of Both Worlds for Security
February 09, 2026 •

Your IT landscape is evolving, blending critical on-premises infrastructure with the flexibility of modern cloud applications. This creates a complex security challenge: how do you enforce strong, consistent authentication across both worlds without sacrificing control or agility? For a growing number of enterprises, the answer is a comprehensive hybrid cloud mfa strategy, designed to bridge […]
-
How to deploy MFA for SCADA environments
December 23, 2025 •
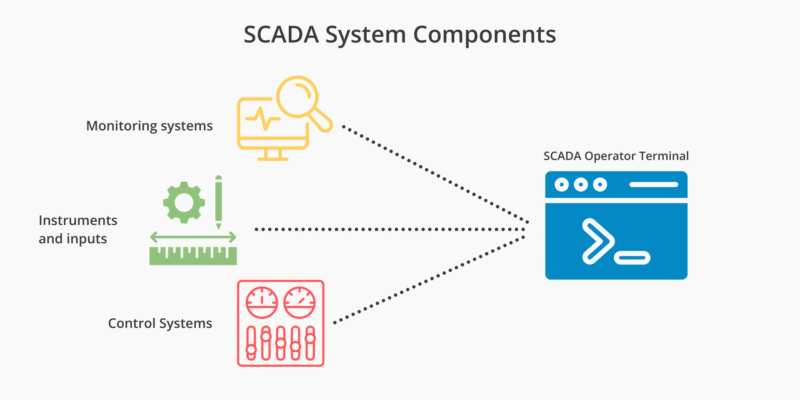
Supervisory Control and Data Acquisition (SCADA) systems manage everything from water filtration and power distribution to chemical manufacturing. Traditionally, these systems were protected by “air-gapping”, the practice of keeping critical infrastructure entirely disconnected from the public internet. However, as the Industrial Internet of Things (IIoT) grows and the need for remote monitoring increases, the gap […]
-
How to migrate to Fortinet IPsec VPN IKEv2 MFA
December 17, 2025 •

Fortinet has signaled a clear direction: organizations should be transitioning off SSL VPN and onto IPsec-based VPNs, specifically IKEv2. This shift aligns with broader industry recommendations around stronger encryption, standardized negotiation, and reduced attack surface. For many customers, though, the technical transition raises a tough practical question: How do you enforce MFA for Fortinet IPsec […]
-
How to add on-prem MFA to Windows Server
November 18, 2025 •

Windows Server powers much of the world’s business infrastructure. Whether it’s managing users, data, and network access behind the scenes, these services are essential. But because these systems often handle administrative logins and remote access, they’re frequent targets for attackers. Multi-factor authentication (MFA) for Windows dramatically reduces that risk. The challenge for many IT teams […]
-
What is federated authentication?
September 22, 2025 •

What is federated authentication? Picture this: an IT administrator at a mid-sized company is tired of employees juggling five different logins just to get through their day. Password resets are piling up, users are reusing weak passwords across systems, and leadership is worried about compliance risks. This is how federated authentication changes the game. Instead […]
-
What is Grid Card Authentication and what are the benefits?
September 04, 2025 •
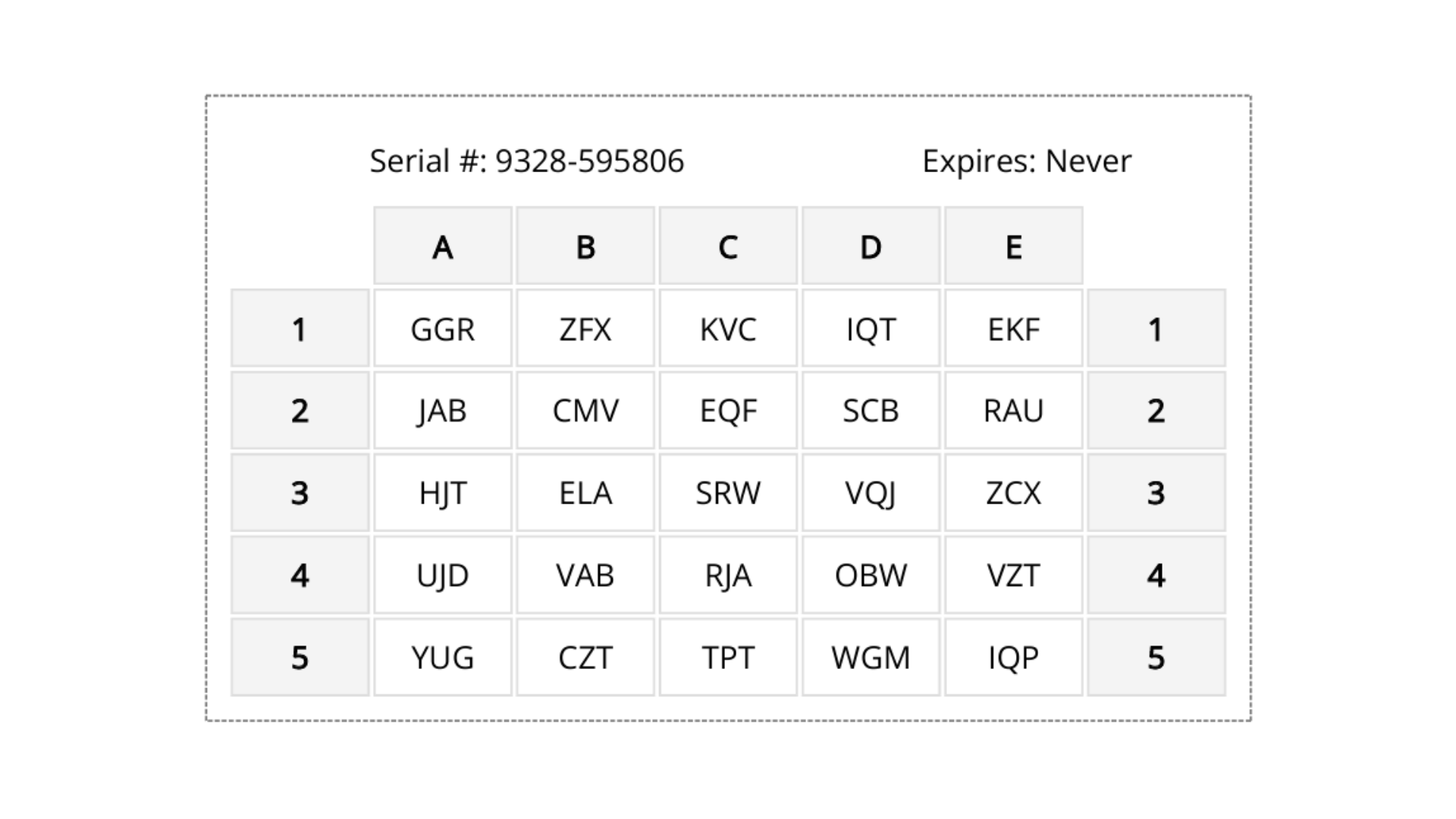
This comprehensive guide takes a look at the details of grid card authentication, illustrating how it works and why it stands out in the crowded landscape of authentication methods. From no-additional costs, to enabling authentication edge cases, there are many benefits to adopting grid card authentication at your organization. Let’s take a look at the […]
-
How to deploy MFA for Microsoft Exchange Server On-Premises
August 12, 2025 •
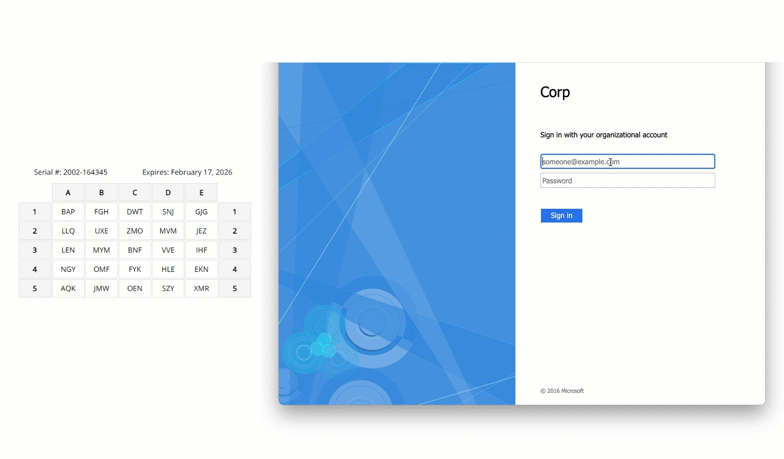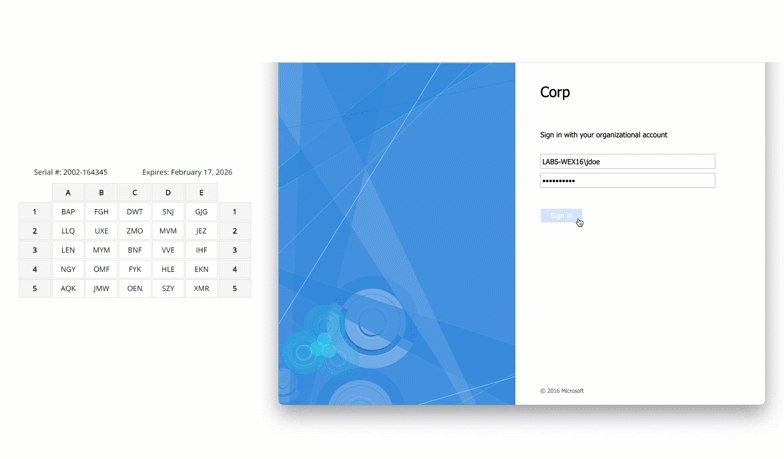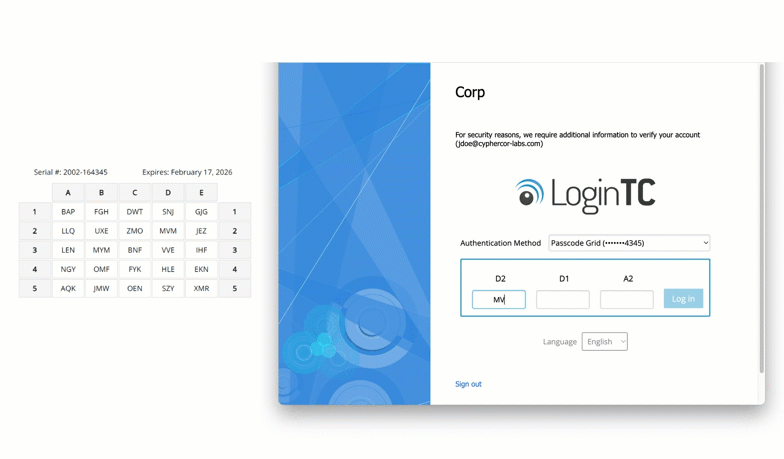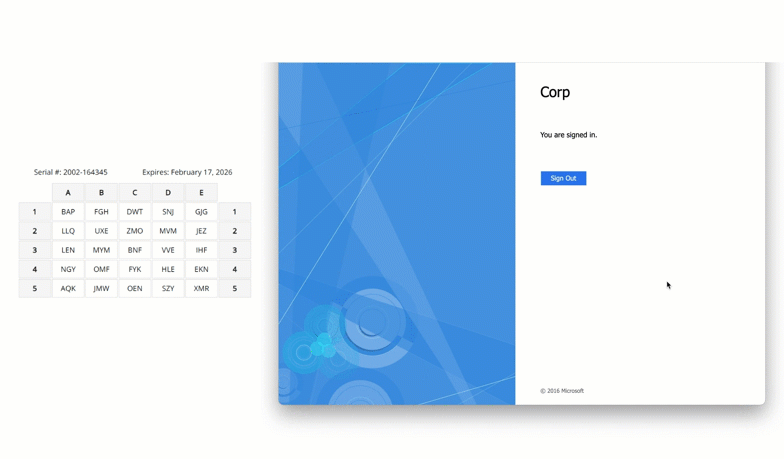
As cyberattacks targeting email systems grow in sophistication, organizations running Microsoft Exchange Server on-premises are increasingly looking to implement multi-factor authentication (MFA) to protect sensitive communications, accounts, and administrative access. Whether you’re hosting Exchange in a regulated environment, repatriating infrastructure from the cloud, or simply looking to close critical security gaps, you can deploy MFA […]
-
Can I use an authenticator app with third-party MFA?
June 26, 2025 •

As more people rely on authenticator apps like Google Authenticator, Microsoft Authenticator, and others in their personal lives, organizations are looking for ways to integrate these familiar tools into their corporate multi-factor authentication (MFA) strategies. Some third-party MFA solutions offer organizations the flexibility to enhance security while providing users with a seamless, straightforward login experience […]
-
How to deploy on-premises MFA for Active Directory
June 09, 2025 •

Safeguarding your Active Directory with on-premises multi-factor authentication (MFA) is a critical step towards developing robust security infrastructure that will keep your organization protected from cyber threats. While cloud software continues to dominate markets, many businesses are deciding to repatriate their data from the cloud, owing to a number of factors. For example, according to […]
-
Why Zero Trust MFA is essential for your business security
April 21, 2025 •
Imagine if you went to the airport and the one and only time they checked who you were, or what you were doing there, was right at the front door. This approach might stop some security threats, but this overreliance on one entry point leaves too much room for error, and threats could slip by. […]
-
Cloud repatriation: What it means for the future of on-premises technology
January 28, 2025 •

Cloud repatriation isn’t just a buzzword—it’s a survival strategy for modern businesses. Companies like Dropbox, Adobe, and GEICO have in recent years migrated their data off the cloud and back into in-house data servers run on their premises. From lower costs, to more control, to better security, there are many reasons why organizations are choosing […]
-
MFA for air-gapped network security
January 20, 2025

When designing air-gapped network security controls, one aspect that is often overlooked is the need for multi-factor authentication (MFA). While air-gapped networks are effective in protecting highly sensitive data and critical systems, it’s integral to not leave them susceptible to attacks they can’t fight on their own. In this blog post, we’ll discuss how MFA […]
-
Cybersecurity for small business: How MFA can prevent devastating cyberattacks
January 08, 2025 •

Cybersecurity for small business is no longer optional—it’s a critical investment, especially when over 60% of SMBs that experience a cyberattack are forced to close their doors within the next year. As SMBs often have fewer resources and IT know-how, choosing cost effective and highly efficient cybersecurity solutions is of the utmost importance. That’s why […]
-
What is the YubiKey vulnerability?
September 10, 2024 •

The announcement of a YubiKey vulnerability is making headlines as researchers uncover a method for cloning the popular phishing-resistant security keys. But what does this vulnerability involve, and how much can it compromise your security? Continue reading to learn more about this YubiKey vulnerability. What is a YubiKey? YubiKeys are a type of security key […]
-
How to use MFA to prevent cyber attacks
August 19, 2024 •

As an IT administrator, it’s likely you hear often that MFA can be used to prevent cyber attacks. You may be wondering if that is true, and how it works. In this article, we’ll go through what MFA is and some notable stories of when cyber attacks could have been prevented with MFA. By the […]
-
How to protect offline backups
July 25, 2024 •

Offline backups are a common security tool to ensure your organization can recover from ransomware attacks. Yet many organizations don’t know how to completely protect offline backups. In this article, we’ll unpack what an offline backup is, the ways to protect offline backups, and additional security measures you may not have considered. Table of Contents […]
-
CDK Global Attack: How to protect your car dealership
June 27, 2024 •

Cyber criminals are wreaking havoc on car dealerships across North America, as a popular software called CDK Global tries to recover from a ransomware attack. The attack has knocked out critical services for car dealerships, with no firm answer on when services will come back online. Learn more about the attack as well as information […]
-
What is the Check Point VPN vulnerability?
June 25, 2024 •

A new vulnerability in Check Point VPN is causing headaches for IT administrators around the world. In this post we’ll discuss what the new Check Point VPN vulnerability is, how it’s affecting people, and what you can do to protect your organization. What is the Check Point VPN vulnerability? On May 27, 2024 Check Point […]
-
External authentication methods in Microsoft Entra ID
May 14, 2024 •

Microsoft has announced that external authentication providers will now be able to integrate natively into the Microsoft Entra ID platform. Microsoft has invited LoginTC to be an external authentication provider with Entra ID. Read on to learn more about what this means for your organization, and your MFA choices in a Microsoft environment. Why should […]
-
Everything you need to know about Australia’s cybersecurity laws
May 09, 2024 •

In the past year, the parliament of Australia has passed a new cybersecurity laws aimed at cracking down on increasingly harmful ransomware attacks and data breaches that have shaken the country since 2022. Australia now seeks to be a global leader in cybersecurity by 2030, and has introduced sweeping reforms tackling every part of the […]
-
How to migrate from the Azure MFA Server
May 03, 2024 •
Microsoft is depreciating their on-premises MFA solution, Azure Multi-Factor Authentication Server, starting September 30, 2024. If you’re an Azure MFA Server customer, you may be wondering what options there are for you to stick with a trusted on-premises solution for your MFA needs. In this blog post, we’ll explore what your options are for moving […]
-
On-Prem, On-Premise, or On-Premises? What do you call MFA software not deployed in the cloud?
March 14, 2024 •
On-premises, on-premise, or on-prem MFA? Whatever you call it, this blog post explores what on-premises technology is, the different names for it, and how you can utilize it at your organization. What is an on-premises MFA solution? On-premises MFA software gives you the full functionality of a third-party MFA solution but with added control over […]
-
How to protect your organization against Citrix Bleed
December 20, 2023 •
Introduction The latest vulnerability affecting Citrix systems, known as Citrix Bleed, has emerged as a critical threat to the private data of organizations and individuals around the world. This critical security issue has impacted countless companies and individuals globally, emphasizing the need for better security measures. In this blog post, we will explore what the […]
-
Data Privacy Legislation: What is it and how does it affect your company
October 02, 2023 •

As more of our personal and private information is stored and transmitted online, data privacy has become a major concern for individuals and businesses alike. In the United States, there have been numerous attempts to establish comprehensive data privacy legislation, but progress has been slow and often contentious. In this blog post, we’ll take a […]
-
The Cost of a Bad MFA Implementation
May 29, 2023 •
If you’re considering implementing an MFA solution at your organization, you’re probably wondering what the cost of MFA is going to be, and what that price tag will include. IT departments are increasingly stretched thin, and getting company-wide buy-in for cybersecurity products can be a challenge. That’s why you need to find the MFA solution […]
-
May 02, 2023 •

As cyber attacks become more sophisticated, organizations are turning to multi-factor authentication (MFA) as a way to secure their systems and data. MFA adds an extra layer of security by requiring users to provide two or more factors of authentication before granting access. However, not all MFA solutions are created equal. To ensure that your […]
-
Why is LoginTC the simplest MFA solution on the market?
June 22, 2022 •
With many MFA options on the market, it’s hard to know how to evaluate them all and decide which solution works best for you. One of the reasons our customers come to us is how easy and user-friendly LoginTC is to operate. You’ve heard us say that LoginTC can be set up in just one […]
-
Why the healthcare industry needs to think about cyber health too
May 26, 2022 •
The healthcare industry is at the top of the list in terms of high-risk industries for cyber attacks. There are a few reasons as to why this would be, and yes it’s exactly what you’re thinking of. Healthcare data holds information that is valuable to cyber criminals and with the industry moving towards more online […]
-
Does your MFA provider support offline Windows Logon and RDP authentication?
April 18, 2022 •
Are you a Windows user and need remote access to your laptop or desktop? With remote work continuing to permeate our workplaces, logging in remotely to a Windows system persists as a common and often insecure activity that users across the globe perform every day. Many administrators correctly want to add a layer of security […]
-
The World’s First Non-OTP Two Factor Authentication Chrome App: The LoginTC Chrome Extension
April 01, 2022 •
Did you know that LoginTC has a chrome extension?! This feature came out in 2015 and was the world’s first non-OTP two factor authentication chrome app! This feature is a breakthrough in the cybersecurity industry and was truly ahead of its time when it was released and yes, you guessed it, it works on Chrome […]
-
How To Protect Your Legacy System
March 22, 2022 •
Do you have an existing legacy system still connected to your active network? Perhaps an old financial system or database, something containing integral and sensitive information that either can’t be or is too difficult to port to a newer system. If you do, you’re not alone. It’s estimated that around 30% of an organization’s technology […]
-
Heightened Security Threats Call For Heightened Security Measures
March 11, 2022 •
Governments around the world are waking up to the threat of cyber crime. According to an executive order from the White House in May of last year, small improvements to their protection won’t cut it and instead need to make a bold change and make significant investments in order to protect the government and its […]
-
Supply Chain Data Breaches: Toyota Dealership
March 04, 2022 •
Imagine you’re the owner of a manufacturing company. You produce thousands of products a day and store valuable information on your servers. Then all of a sudden you get notified of a data breach from one of your suppliers and your information has been affected yet again. Scrambling to figure out the source, you’re losing […]
-
How to make your employees part of the cybersecurity equation
February 11, 2022 •
Cybersecurity can be confusing for employees to understand. Often employees think of something that management has to worry about, and don’t realize they play an integral role in ensuring the security of the company they work for. They might think, where do I even start? Or how does cybersecurity affect me? What can I do […]
-
Why you need full MFA deployment to protect your company
February 04, 2022 •
The COVID-19 pandemic and the rise in employees working from home has prompted companies to think of more secure ways to keep their private information safe. Despite this shift in thinking, the majority of companies are only protecting certain departments with MFA rather than every user. “Not putting MFA on all of your applications is kind of […]
-
Why you shouldn’t ignore the social media factor when protecting your business from hackers
January 27, 2022 •
Imagine this, you’re taking a break from work and scrolling through Facebook when you receive a message from a friend about a video that went viral and you’re in it. Curiosity kicks in and you think “what video?” and so you click the link, and at first everything is fine. You see it was a […]
-
How many five-letter cybersecurity words can you name?
January 19, 2022 •
The Wordle craze has taken the internet by storm, and knowing your cybersecurity lingo could help you figure out the daily word puzzle more than you realize.
-
January 06, 2022 •
This year at Cyphercor, we’re taking a close look at cybersecurity trends for 2022 and what we can expect in the industry.
-
What’s on your cybersecurity wish-list?
December 06, 2021 •
This year at Cyphercor, we’re taking a close look at cybersecurity trends for 2022 and what we can expect in the industry.
-
Is an on-premises 2FA solution right for you
November 18, 2021 •
We’re taking a look at what on-premise technology is, how it differs from cloud technology, and how it could be beneficial to your business.
-
Cybersecurity Awareness Month: How You Can Phight the Phish
October 14, 2021 •
Cybersecurity awareness month is here! Learn more about how to protect yourself from phishing scams using 2fa systems.
-
October 06, 2021 •
October marks Cybersecurity Awareness Month and this week’s theme is being cyber safe! Read more about how you can stay cyber safe both at work and at home!
-
“6 Barriers To Implementing 2FA and How To Overcome Them” Webinar Recap
October 01, 2021 •
Missed our webinar? Don’t worry we got you covered. We outlined everything you need to know about implementing 2fa. Learn more today!
-
Data Breaches in the Manufacturing Industry
September 15, 2021 •
Data breaches and two factor authentication, how an extra layer of security can save your company millions and not slow down production. Learn more!
-
Two Factor Authentication: Data Hacks and Breaches
September 08, 2021 •
Two Factor Authentication, how it can protect your company’s information from hackers and data breaches. Learn more! Learn more
-
5 Back-to-work Cybersecurity Tips
July 13, 2021 •
If you listen closely, you’ll hear the sound of millions of workers returning to the office after a long hiatus working from home.
-
Hackers Are Pinpointing Accounting Firms, Leading To Identity Theft. Here’s How To Get Protected
April 05, 2021 •
How would you feel if the person you trust most gave all your personal and financial information to someone else behind your back? Pretty angry, right?
-
Amazon and Walmart’s Not-So-Secret Weapon Against Cyber Attacks
March 05, 2021 •
What do Amazon and Walmart have in common? Besides being industry-leading Fortune 500 multinationals, they both understand the importance of 2-Factor Authentication (2FA)
-
The Hard Truth About Cyber Security
September 12, 2018 •
Everyday prominent companies are making news headlines about security breaches, LoginTC has the answer to maturing your security stature
-
Chinese Company Installs Backdoor on Android Devices
August 29, 2018 •
BYOD and Two-Factor authentication
-
How Formula 1 Utilizes Remote Access & the Importance of Network Security
August 14, 2018 •
Two-Factor authentication can help boost your cyber security strategy
-
Cost Implications To Lack of Cyber Security
February 17, 2017 •
Real dollar losses when two-Factor authentication is not considered
-
Google’s Warning of Hacking Group Involvement
January 05, 2017 •
Two-Factor authentication can help protect your account
-
LoginTC Becomes an Official Partner of WatchGuard
December 09, 2016 •
LoginTC is pleased to announce our official partnership with WatchGuard. WatchGuard is one of the leading competitors of advanced network security, including firewall and threat management solutions
-
NIST No Longer Accepts SMS as a Two-Factor Authentication Method
November 30, 2016 •
LoginTC is pleased to announce our official partnership with WatchGuard. WatchGuard is one of the leading competitors of advanced network security, including firewall and threat management solutions
-
Top 3 reasons to avoid SMS when choosing a 2-factor authentication provider
May 15, 2015 •
The majority of smartphone-based two-factor authentication (2FA) providers today use SMS to deliver second factor codes or one-time passwords to users. Here’s why they shouldn’t.
-
March 24, 2015 •
Phishing attacks remain pravelent and continue to increase in sophistication. In this blog, we focus on SMiShing, SMS-based phishing attacks. Learn how to protect yourself with two-factor authentication.
-
Top 5 reasons hard tokens are hard to manage
March 16, 2015 •
Hard Tokens are the most common method of 2FA deployment. But that doesn’t make them the best method. Here are 5 reasons why hard tokens are hard to manage!
-
How to set up your VPN with LoginTC 2FA
March 05, 2015 •
Enabling two-factor authentication for your VPN is simple with LoginTC. Here’s how to set it up.
-
How VPN admins & security managers use LoginTC to protect their networks
February 25, 2015 •
Some insight into how VPN administrators and security managers are currently using LoginTC two-factor authentication to protect their networks.
-
The need for contextual information within multifactor authentication
February 19, 2015 •
LoginTC seamlessly incorporates contextual information into its 2FA system for real-time threat detection / fraud alert.
-
January 28, 2015 •
Remote access to a Cisco (or any) VPN on a mobile device, such as a smartphone or tablet, using two-factor authentication (2FA) is simple with LoginTC. We break it down for readers in this blog.
-
More remote work, more risk: How two factor authentication can help
January 16, 2015 •
A survey by Regus anticipates more remote work in 2015. This blog explains why that means 2FA is necessary.
-
Two-Factor Authentication Worldwide using LoginTC
April 02, 2014 •
How to provide secure access to internal and external applications worldwide
-
Fundamental OTP Disadvantages & Problems in Two-Factor Authentication
January 14, 2014 •
Think one time passwords are a second factor? Think again.
-
Wearable Devices and the Future of Two Factor Authentication
December 18, 2013 •
“Something you have” doesn’t have to mean “Something you need to fish out of your bag”
-
The Use of Secure Remote Password in LoginTC
December 06, 2013 •
How LoginTC uses the Secure Remote Password Protocol to increase security.
-
Passwords Are a Shared Problem
November 29, 2013 •
Password breaches are a shared problem – why two-factor authentication will prevail.
-
August 30, 2013 •
Any authentication should bolster security while keeping administrators and users happy and informed.
-
Connect Your Smartphone via VPN with Two Factor Authentication
March 04, 2013 •
How to enable Two Factor Authentication on your smartphone to access VPN connections.
-
Performance Analysis of Mobile Push Notification Networks
February 08, 2013 •
A discussion on the importance of mobile push notification networks to LoginTC and how we test and monitor the networks for performance.
-
Why Passwords Are No Longer Reliable
February 02, 2013 •
News of stolen passwords at the New York Times and Twitter allow fraudsters to access user accounts and emails.
-
LoginTC Differentiators From Other Two Factor Authentication Solutions
January 11, 2013 •
A frequent question Cyphercor has to address from potential customers and prospects is regarding LoginTC’s differences from other two-factor solutions in the marketplace. In this blog post we go over some of these differentiators.